This article is part 6 of a series, for which the following articles are available:
Conditional Access demystified, part 1: Introduction
Conditional Access demystified, part 2: What is Conditional Access?
Conditional Access demystified, part 3: How does Conditional Access work?
Conditional Access demystified, part 4: Designing a Conditional Access strategy
Conditional Access demystified, part 5: Implementing Conditional Access
Conditional Access demystified, part 7: Modifying Conditional Access to suit your special needs
Conditional Access demystified, part 8: Resources and further references
In this part of the series we will go into more detail on where we can find information which can help us to troubleshoot Conditional Access policies.
What if tool
The first tool we are going to discuss is the Whatif tooling. You can find the Whatif tooling by clicking on the What If icon on the Conditional Access policy overview page.
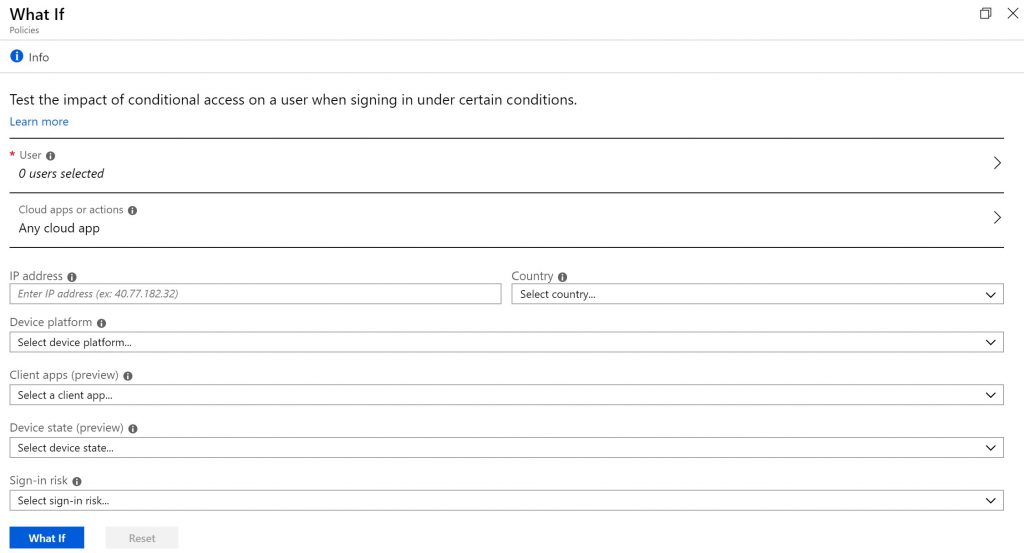
With the whatif tooling you can determine which policies are applicable for a certain scenario. If you run the tooling it will give you an overview of which policies will apply and which policies will not apply including the condition that hasn’t been met.
A possible outcome can be:
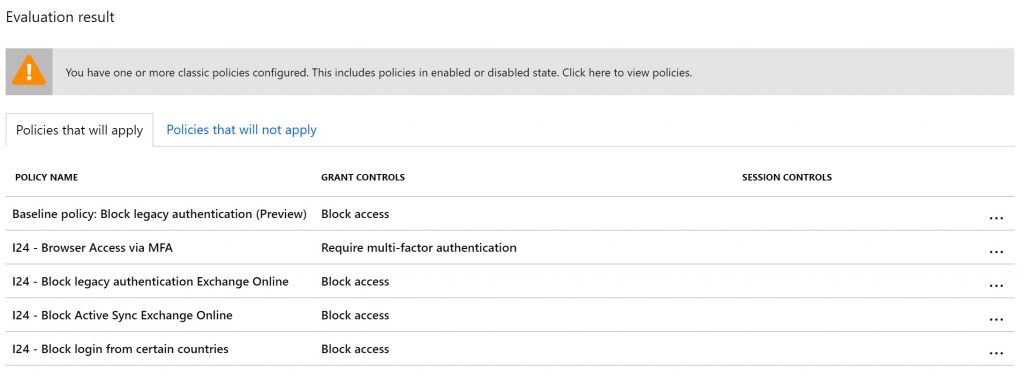
There are some things the What if tooling is not capable of displaying though, that is that the effective outcome for the user, take for example the outcome of the example above – I’m still granted access to the cloud apps even though some “Block access” controls apply.
Azure Active Directory sign-ins logging
Once the policy is implemented you can use sign-ins logging from Azure Active Directory. Sign-ins logging is available under the monitoring section of Azure Active Directory, in the overview you can see all the sign ins and once a sign in is selected you can find more information about the circumstances under which the sign-in took place.
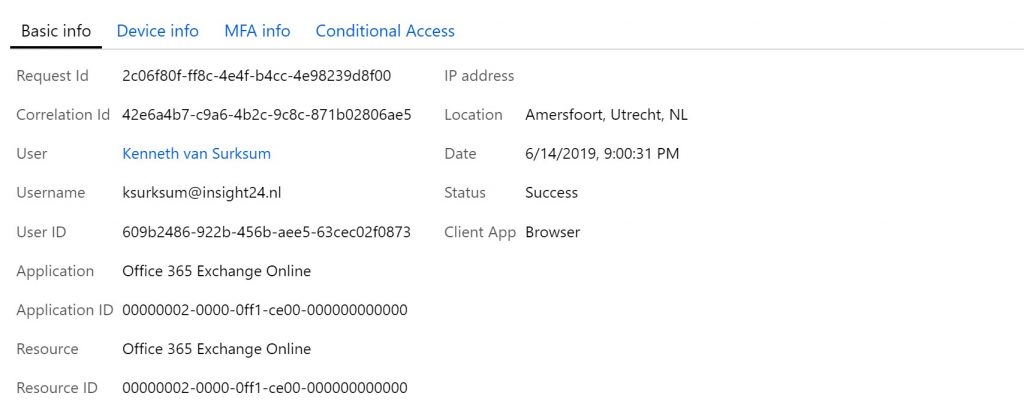
Below is an example of the outcome. On the basic page you can see the user involved, the IP address the user is coming from (removed from the screenshot for obvious reasons) and what client app was used to access the cloud app (in this case Office 365 Exchange Online).
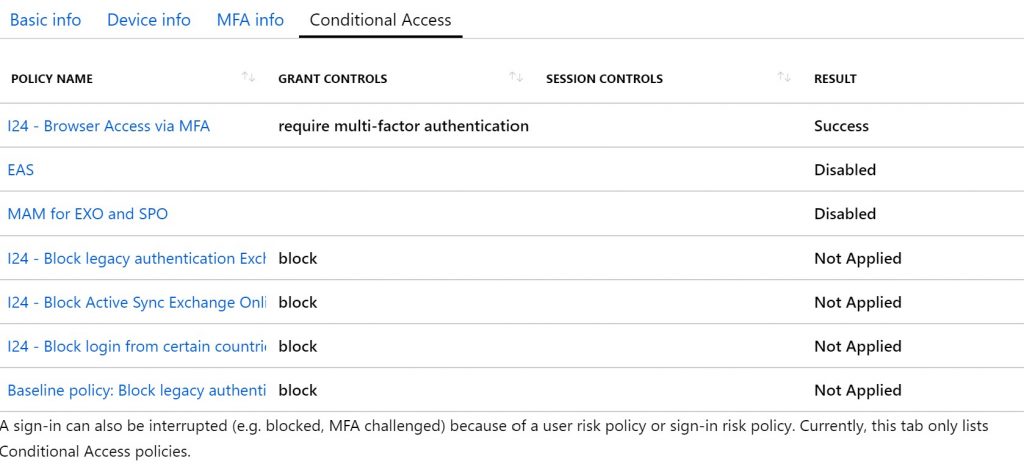
On the tab Conditional Access you can see which policies are applied for this scenario.
Where to find help and provide feedback
There are many resources where you can find help on Azure Active Directory Conditional Access, when troubleshooting at first Google/Bing is your best friend here. If those search engines don’t give the expected result you can always ask at the following forums, or reach out using twitter and other social media channels.
- Azure Active Directory @ MSDN – https://social.msdn.microsoft.com/Forums/en-US/home?forum=WindowsAzureAD
- Azure Active Directory @ Stack Overflow – https://stackoverflow.com/questions/tagged/azure-active-directory
If something doesn’t work as expected another good source could be to check the Azure Active Directory user voice page, where a certain functionality might already be noticed by somebody else who requested the product team to solve it. You can find the UserVoice page for Conditional Access here: https://feedback.azure.com/forums/169401-azure-active-directory/category/167259-conditional-access
In the next part (part 7) of this series I’m detailing some of the options to extend Conditonal Access in order to meet special needs