
In Q1 2017 Microsoft released the Pass Through Authentication (PTA) functionality as part of Azure AD connect. With the release of Azure Active Directory (Azure AD) Pass-through Authentication allowed for your users to sign in to both on-premises and cloud-based applications using the same passwords without the need to implement a Active Directory Federation Services (ADFS) environment.
With this options we now have the following authentication options available when setting up a hyrid identiy:
- Password hash synchronization (PHS) – https://docs.microsoft.com/en-us/azure/active-directory/hybrid/whatis-phs
- Pass-through authentication (PTA) – https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-pta
- Federation (AD FS) – https://docs.microsoft.com/en-us/azure/active-directory/hybrid/whatis-fed
Many Microsoft customers started integrating with Azure AD before 2017, at that time they only had two options available to them, either Password Hash Sync or using the ADFS federation option. Where the ADFS federation option was the only way to authenticate a user using an on-premises Domain Controller. So with ADFS we created a federated trust between your on-premises Security Token Service (STS) and the federated domain you’ve specified in your Azure AD tenant.
For most companies, implementing the ADFS functionality is a relatively expensive option though just for this purpose, since an ADFS environment mostly consitst of more than 1 deployed server. The example below gives an idea of a possible ADFS implementation where the ADFS servers as hosted on Azure IaaS virtual machines.
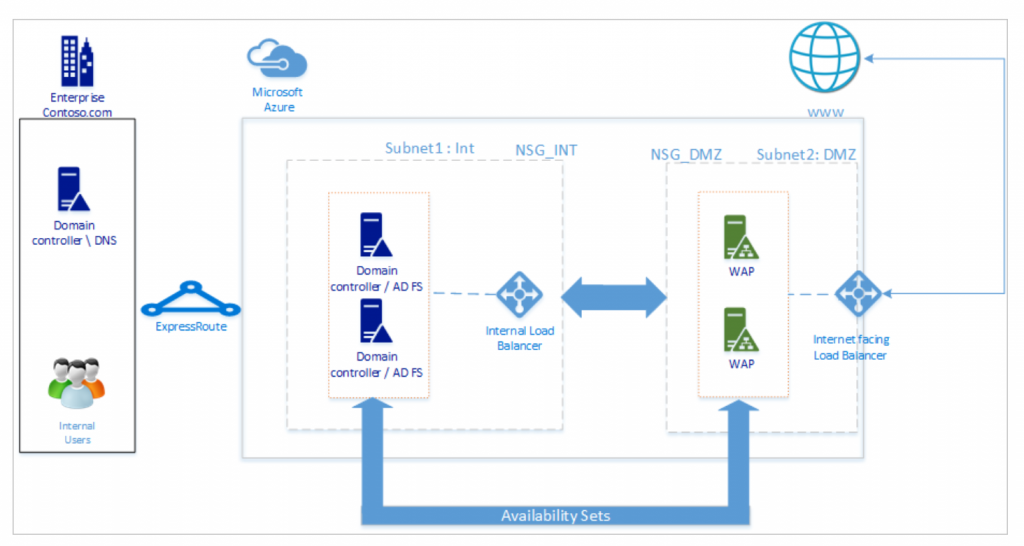
Source: Deploying Active Directory Federation Services in Azure – https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/deployment/how-to-connect-fed-azure-adfs
ADFS is also more complex to manage compared to hosting the same functionality in Azure AD, if you use Azure AD and ADFS you also have 2 environments with overlapping functionality.
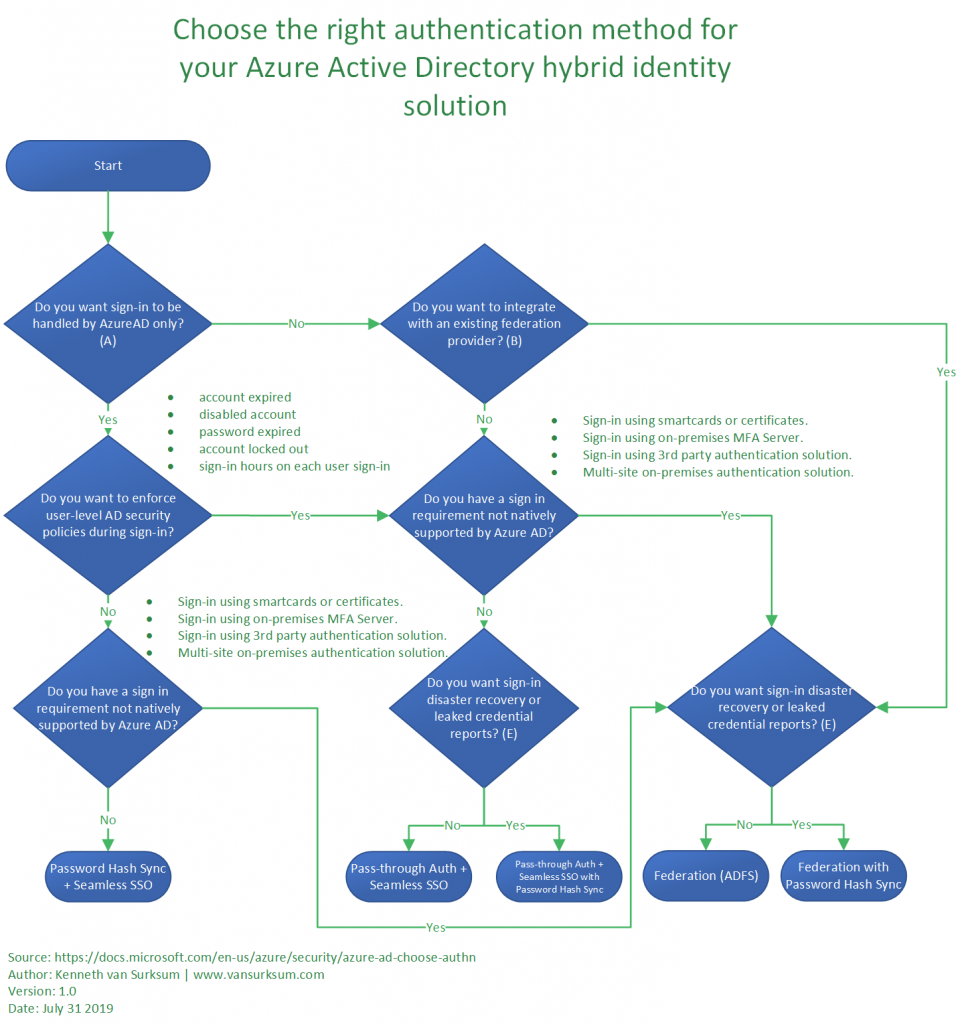
Microsoft provides some guidance on what type of authentication method to use when you do a green-field deployment of Azure AD, schematically this looks like the schema below, you’ll see that using the PTA option is valid for many scenario’s.
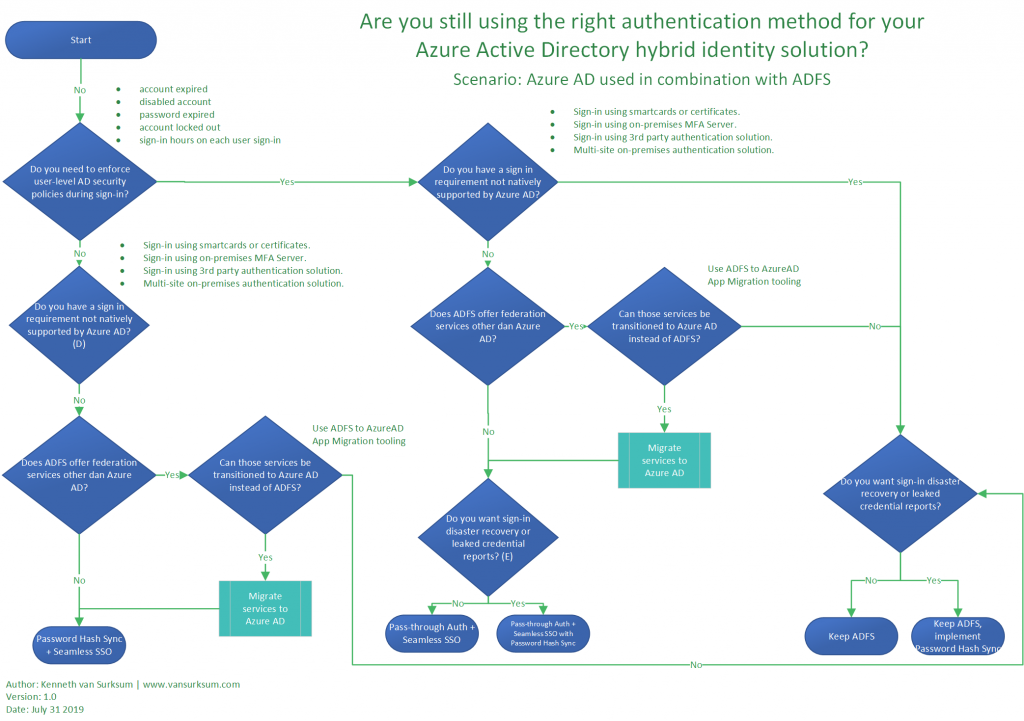
If you are currently on ADFS though, it might be worthwhile to transition to Pass Through Authentication (PTA) of Password Hash Synchronization (PHS) only. In order to make that decision, I have created the following flowchart, which can hopefully help you choose whether to keep ADFS or transition to another authentication method. This flowchart is also available as a separate download on Github here: https://github.com/kennethvs/blog/blob/master/Azure%20AD%20authentication%20integration%20flowchart.pdf
For many applications which might now be redirected towards your ADFS infrastructure, there is now support available to redirect that application to use Azure AD, Microsoft publishes tutorials for many 3rd party SaaS applications here: https://docs.microsoft.com/en-gb/azure/active-directory/saas-apps/tutorial-list
I reached out on twitter to find some reasons which could possible block the transition towards PTA or PHS, below are some of the responses:
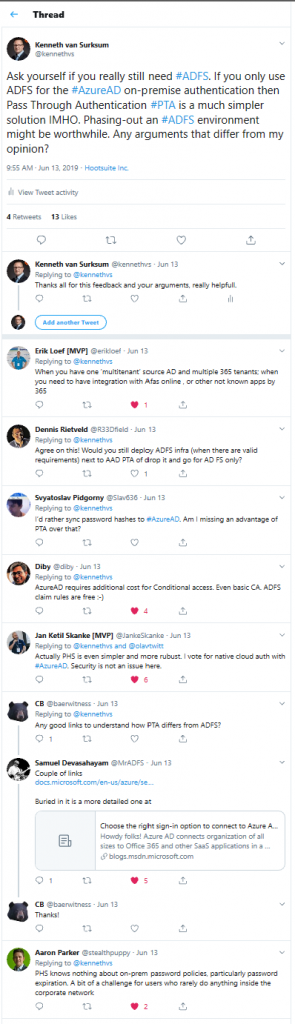
Some of the comments provided are:
- When you have one ‘multitenant’ source AD and multiple 365 tenants; when you need to have integration with Afas online , or other not known apps by 365
- I’d rather sync password hashes to #AzureAD. Am I missing an advantage of PTA over that?
- PHS knows nothing about on-prem password policies, particularly password expiration. A bit of a challenge for users who rarely do anything inside the corporate network
- AzureAD requires additional cost for Conditional access. Even basic CA. ADFS claim rules are free 🙂
- Actually PHS is even simpler and more rubust. I vote for native cloud auth with #AzureAD. Security is not an issue here.
- Agree on this! Would you still deploy ADFS infra (when there are valid requirements) next to AAD PTA of drop it and go for AD FS only?
Conclusion:
Just because at time of integrating Azure Active Directory the only options to have an on-premise validation of the user account signing in was Active Directory Federation Services, that requirement could be solved in another way today. When you only use ADFS as the federation mechanism for Azure AD logins only, consider moving to Pass Through Authentication instead.
Migration from ADFS to PTA is described in the following article: Migrate from federation to pass-through authentication for Azure Active Directory – https://docs.microsoft.com/en-us/azure/active-directory/hybrid/plan-migrate-adfs-pass-through-authentication
Some references used while writing this article:
What is hybrid identity with Azure Active Directory? – https://docs.microsoft.com/en-us/azure/active-directory/hybrid/whatis-hybrid-identity
Five tips to improve the migration process to Azure Active Directory – https://techcommunity.microsoft.com/t5/Azure-Active-Directory-Identity/Five-tips-to-improve-the-migration-process-to-Azure-Active/ba-p/445364
Azure AD pass-through authentication- https://www.jgspiers.com/azure-ad-pass-through-authentication/
Support Tip: A Quick Look at Azure AD Connect and Hybrid Identity – https://techcommunity.microsoft.com/t5/Intune-Customer-Success/Support-Tip-A-Quick-Look-at-Azure-AD-Connect-and-Hybrid-Identity/ba-p/717280
Ten things you need to know about Pass-through Authentication – https://dirteam.com/sander/2019/02/28/ten-things-you-need-to-know-about-pass-through-authentication/
Your Pa$$word doesn’t matter – https://techcommunity.microsoft.com/t5/Azure-Active-Directory-Identity/Your-Pa-word-doesn-t-matter/ba-p/731984
I will add the “NO GO” question for me was self service password reset. If you have it turned on for ADFS for external users to be able to reset their password, then you will need to buy an Azure AD P1/P2 or an O365 E3/E5 license for each and every user you want to enable. We run E1 licenses so that turns into a non-starter.
Good remark Chris
To be honest because of the fact that I mainly work with Enterprise customers, not having Azure AD Premium available almost never occurs in my line of work. You do have a valid remark though and you are absolutely right that this is a NO GO if you want to maintain that functionality. Depending on the size of your organization transitioning from Enterprise plans to Business Premium plans (for up to 300 users) could be beneficial and give you the P1 edition, but that is a whole other topic.
Thanks for visiting my blog!
/Kenneth
ADFS is still required if you want to use hybrid WHfB right?
Coert,
Depends on how you configured your environment for WHfB certificates.
If you have Key Trust configured, you can transition, Certificate trust requires ADFS indeed.
See: https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-faq
Regards,
Kenneth
Thank you for the verry good article.
One thing tho: Do we need ADFS for Exchange Hybrid Enviroment?
Hi,
No there is no hard requirement that states that you need ADFS for your Exchange Hybrid environment,
Thanks for visiting my blog,
Regards, Kenneth