Update: On September 23, 2021, the Exchange Team announced that effective October 1st, 2022 basic authentication, regardless of usage will be permanently disabled in all tenants.
Update: On June 17, 2021, the Exchange Team announced that they are going to turn of basic authentication for tenants not using it.
Update: On February 5th, 2021, the Exchange Team announced that turning off legacy authentication in H2, 2021 is postponed until further notice. When they resume the program, they will let customers know with a 12 months notice. They did announce that they will continue to turn off Basic Authentication protocols not in use within tenants. They also announced that they will add support for Modern Authentication into the MAPI, RPC, and Offline Address Book (OAB) protocols.
Update: On April 3rd 2020, the Exchange Team announced that due to the COVID019 crisis, they will postpone disabling legacy authentication until the second half of 2021.
Update: On April 30 2020, the Exchange Team announced that OAuth 2.0 authentication for IMAP and SMTP AUTH protocols is now available. In order to leverage this functionality mail clients need to start using it (so they need an update). Michel de Rooij did a nice article on how to configure Thunderbird for oAuth2 which you can read here: Configuring Exchange Online with IMAP & OAuth2
Update: On May 28 2020, the Exchange Team announced that OAuth support for POP is now also available for Exchange Online.
Update: On June 30th 2020, the Microsoft Exchange Team announced support for Modern Authentication in scripts using the new Exchange PowerShell module, see: Modern Auth and Unattended Scripts in Exchange Online PowerShell V2
Update: On July 28th, the Microsoft Exchange Team announced some new changes to Modern Authentication controls in the Microsoft 365 Admin center, see: Basic Authentication and Exchange Online – July Update
Update: On October 27, 2020 I presented on this topic for the Windows Management User Group Netherlands Tuesday Webinar, together with Erik Loef. This session has been recorded and can be viewed here: WMUG NL Tuesdays Featuring Erik Loef and Kenneth van Surksum
On March 7, 2018 the Microsoft Exchange Team announced that on October 13, 2020 it would stop the support for Basic Authentication (also called Legacy authentication) for Exchange Web Services (EWS) in Exchange Online (EXO), the version of Exchange offered as a service part of Office 365. EWS is a web service which can be used by client applications to access the EXO environment. The team also announced that EWS would not receive any feature updates anymore, and suggests customers to transition towards using Microsoft Graph to access EXO.
One and a half year later, on November 20, 2019 the Exchange Team also announced to stop supporting Basic Authentication for Exchange ActiveSync (EAS), Post Office Protocol (POP), Internet Message Access Protocol (IMAP) and Remote PowerShell on October 13 2020 as well. Authenticated Simple Mail Transfer Protocol (SMTP) will stay supported when used with Basic Authentication.
Instead of supporting Basic/Legacy authentication Microsoft will move towards only supporting Modern Authentication for most of the methods used to connect to Exchange Online.
So what is this Legacy/Basic and Modern Authentication exactly?
When using Basic/Legacy Authentication application sends a username and password with every request to Exchange Online which either forwards the credentials towards Azure AD or a federated authentication provider like Active Directory Federation Services (ADFS). The problem with Basic/Legacy authentication is that it’s vulnerable to brute force or password spray attacks.
Modern Authentication is based on OAuth 2.0 and the Active Directory Authentication Library (ADAL) providing token based authentication. OAuth 2.0 in this case is the protocol being used, and ADAL is used to authenticate against Azure AD.
Token based authentication, as described by the World Wide Web Consortium (W3C):
“The general concept behind a token-based authentication system is simple. Allow users to enter their username and password in order to obtain a token which allows them to fetch a specific resource – without using their username and password. Once their token has been obtained, the user can offer the token – which offers access to a specific resource for a time period – to the remote site. Using some form of authentication: a header, GET or POST request, or a cookie of some kind, the site can then determine what level of access the request in question should be afforded.“
So Microsoft wants you to move towards Modern Authentication since it’s a more secure solution. Another big advantage of using Modern Authentication is that it can leverage Azure AD Conditional Access, giving you the option to force MFA for users among other options. See my blogpost series on Azure AD Conditional Access for more information about implementing Conditional Access..
How can I check whether Modern Authentication is enabled or not?
If your tenant was created after August 1, 2017 Modern Authentication is turned on by default, that does not mean that in the meantime someone disabled Modern Authentication of course.
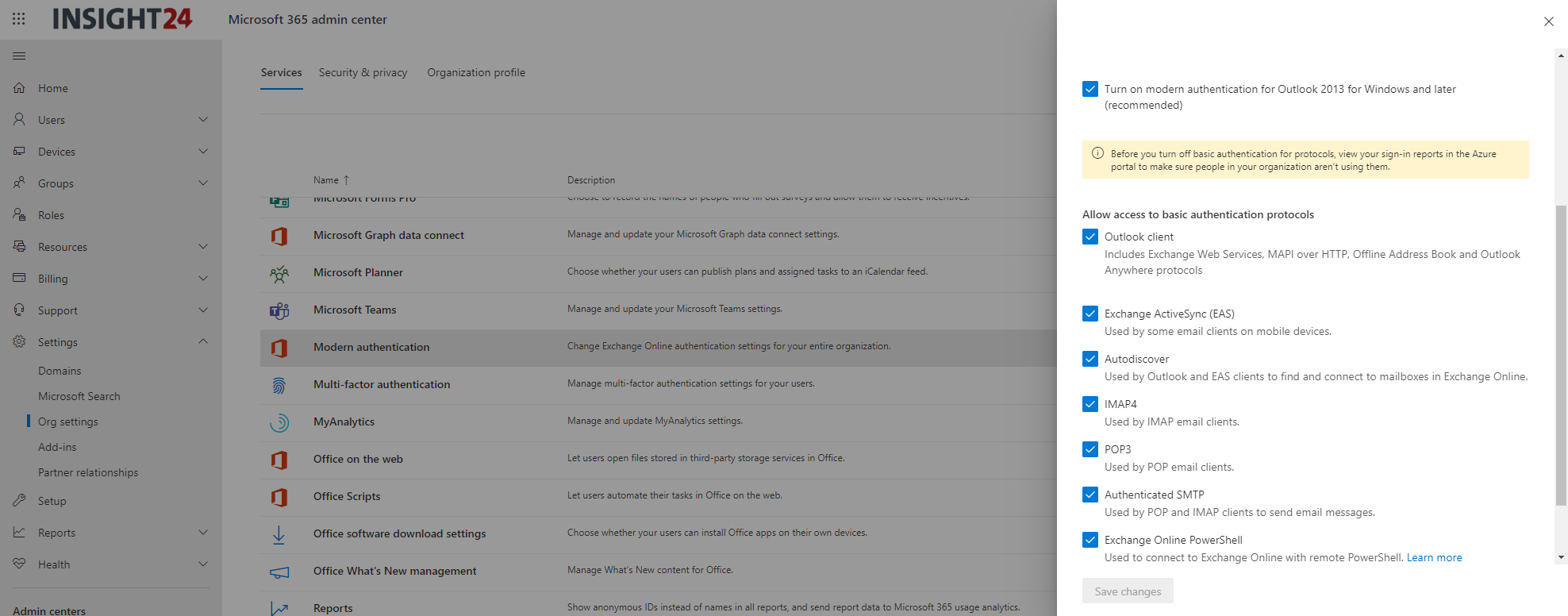
The easiest way to check if Modern Authentication is enabled is by looking in the Microsoft 365 Admin Center. Once in the Admin Center go to Settings -> Settings – > Modern Authentication. Here you can check if Modern authentication is enabled.
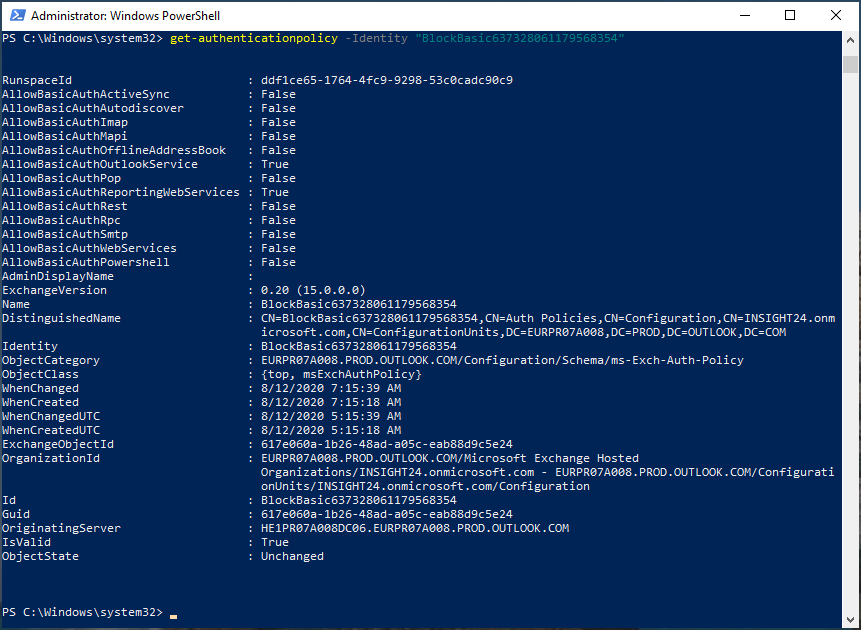
The other way to check whether Modern Authentication is enabled is by using PowerShell, below an example on how to do this using Cloud Shell.
![Machine generated alternative text:
Microsoft Azure
Powersnell O ?
Requesting a Cloud Shell. Succeeded.
Connecting terminal...
Welccme to Azure Cloud Shell
Type "az" to use Azure CLI
Type '"help" to learn about Cloud Shell
K)TD: Switch to Bash frcm PowerShe11 : bash
VERBOSE: Authenticating to Azure .
VERBOSE: Building your Azure drive .
Azure : /
PS Azure: Connect-DCPSSession
Sesrcf7 resources, services. Enc docs (G+/)
Q
O
WARNING: The names of some imported commands from the module
bose parameter. For a list of approved verbs, type Get-Verb.
WARNING: The names of some imported commands from the module
bose parameter. For a list of approved verbs, type Get-Verb.
Azure : /
PS Azure: Get-(hganizationConfig I Format-Table Name,OAuth*
' tmp_treuwtui. xbr '
' tmp_treuwtui. xbr '
-Auto
include unapproved verbs that might make them less discoverable.
include unapproved verbs that might make them less discoverable.
To find the commands with unapproved verbs,
To find the commands with unapproved verbs,
run th
run th
Name
INSIGHT24. or-microsoft. cæ
Azure : /
PS Azure:\> C]
ulth2C1ientProfi1eEnab1ed
True](https://www.vansurksum.com/wp-content/uploads/2020/03/Modern-2-1024x547.png)
This is not all though, since it’s possible to define how users can connect to their mailbox on the properties of the user.
Microsoft 365 Admin Center -> Users -> Active Users -> Select User -> Mail -> Email apps and select Manage email apps.
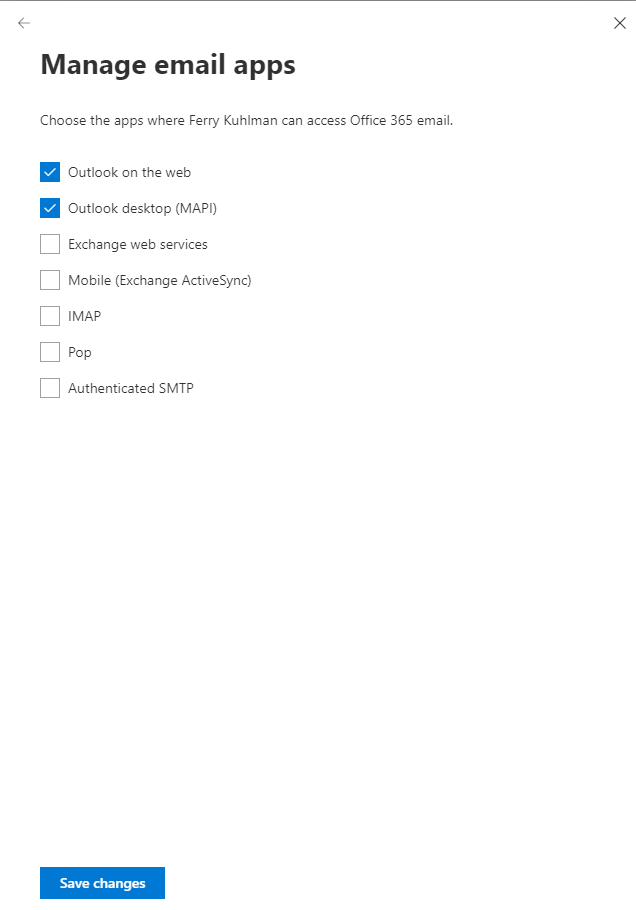
Update (August 2020): By disabling the protocol for a user we disable the protocol as a whole and not just basic authentication. For example, currently IMAP can be used using either Legacy or Modern Authentication.
This is for example a good option to set if you don’t want users to use IMAP at all, whether that is IMAP with or without Modern Authentication capabilities. If you want to disable access to IMAP using basic authentication you must use an authentication policy. More on authentication policies later.
What about other Office 365 Services?
Besides Exchange Online also SharePoint online (SPO) and Skype for Business (SfB) Online can be using basic/legacy authentication as well. While busy with the transition, you might want to consider moving those workloads to Modern Authentication as well.
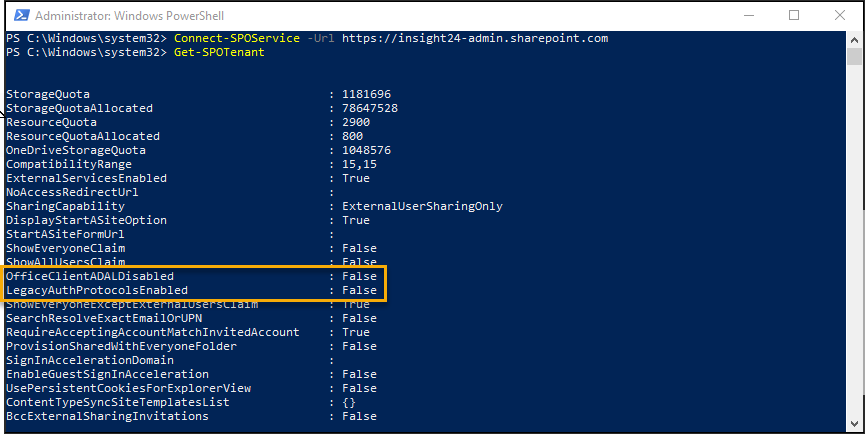
Check SharePoint Online for basic/legacy authentication
Checking whether SPO is using basic/legacy authentication is depending on two settings, which can be displayed using the Get-SPOTenant commandlet in PowerShell. The first one is OfficeClientADALDisabled, which when set to true specifies that Modern Authentication is disabled. The second one, LegacyAuthProtocolsEnabled, when set to True this enables Office clients using non-modern authentication protocols (such as, Forms-Based Authentication (FBA) or Identity Client Runtime Library (IDCRL)) to access SharePoint resources.
Check Skype for Business Online for basic/legacy authentication
Checking whether Skype for Business Online is configured for basic authentication is described in details by Ronni Pedersen in his blog: “Enable modern authentication for Skype for Business Online“
Am I safe if Modern Authentication is enabled?
Even if you have Modern Authentication enabled, a user is still able to access his/her mailbox using legacy/basic authentication via one of the enabled protocols defined on the users mailbox properties. You can either disable this access via the user properties as described below, or you can enable a Conditional Access policy, see: How to: Block legacy authentication to Azure AD with Conditional Access.
What to do if you don’t have Modern Authentication enabled?
If Modern Authentication is not enabled, changes are really high that clients still access EXO using basic/legacy authentication. Most current email clients support Modern Authentication and will automatically switch to Modern authentication once your tenant has been switched to Modern Authentication enabled. Outlook 2013 needs some extra registry keys for example in order for Modern Authentication to be used.
Even though some of the applications support Modern Authentication, they potentially have to be reconfigured. For example an Outlook client which uses IMAP to connect to the EXO mailbox, should be reconfigured to start using the “default” Outlook Desktop option via Mail API (MAPI). Microsoft has stated that they are working on POP and IMAP implementations which work with Modern Authentication. If you really have a valid case of keeping POP and IMAP enabled for some clients, then make sure that once Microsoft provides the option for modern authentication that you transition towards that solution.
The challenge is with older email clients (Outlook 2010 and others), services and scripts which use EWS or scripts which still use basic/legacy authentication. iOS and MacOS support Modern Authentication in their most recent versions, as with Android it gets tricky since there are so many versions, therefore Microsoft recommends switching to the Outlook App for using email hosted by EXO. Extra advantage here is that you can manage the Outlook app using Mobile Application Management (MAM).
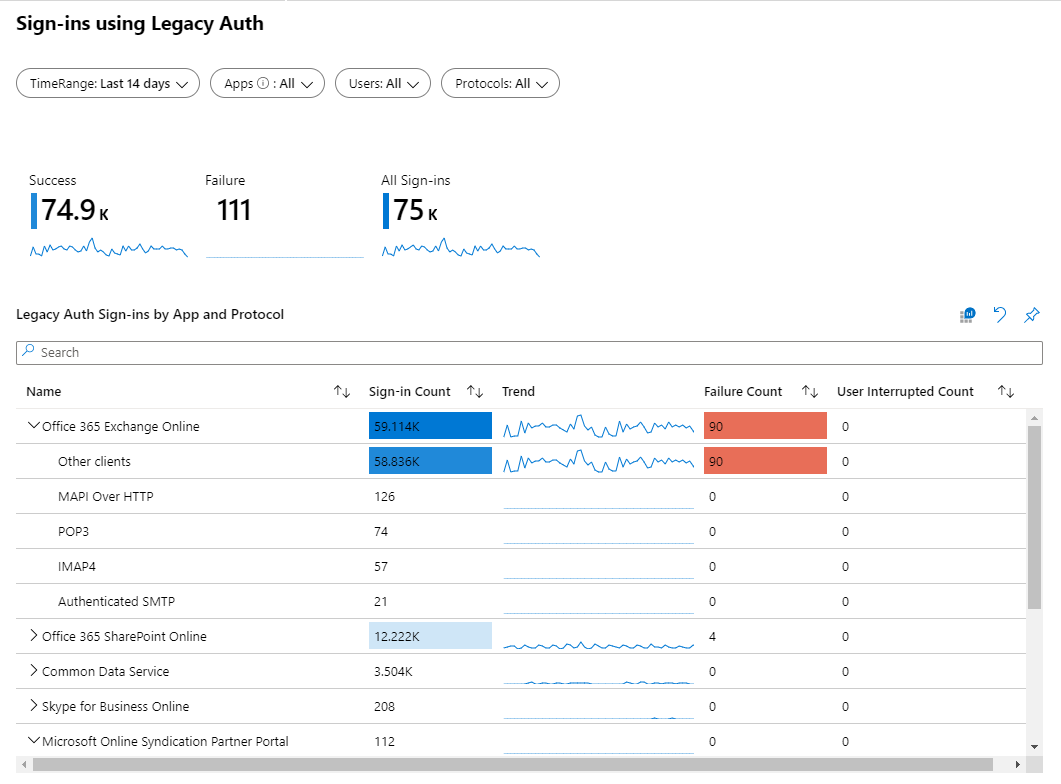
In order to get an idea of what you are dealing with, it’s important to first measure whether or not Basic/Legacy authentication is being used or not, this can be done using either Azure AD sign-ins logging, Azure AD workbooks or other methods (f.e. using KQL queries when you send your Azure AD logs to a Azure Log Analytics workspace).
Azure AD sign-ins logging
Go to the Azure Active Directory admin center, and browse to sign-ins. Add filters for Client app and Application.
For Client App select the following client apps: Auto Discover, Exchange ActiveSync, Exchange Online PowerShell, Exchange Web Services, IMAP4, MAPI over HTTP, Offline Address Book, Other Clients, Outlook Anywhere (RPC over HTTP), Outlook Service, POP3 and Reporting Web Services.
If you also filter on Application (starts with Office 365 Exchange Online) you will get a nice overview. In the picture below you can find a nice (anonymized) overview of clients still using Legacy/Basic Authentication to access EXO.
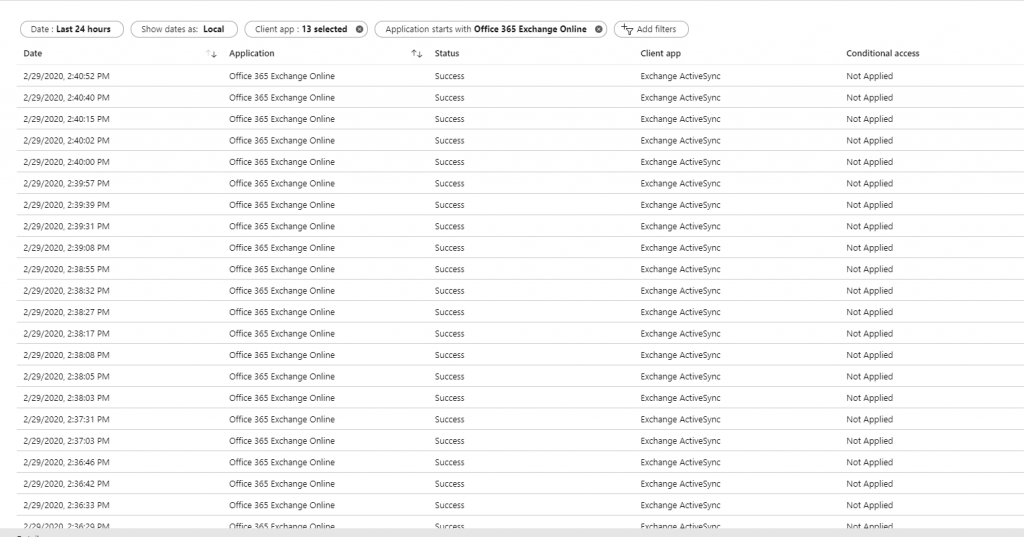
You can export the results, and work from there in Excel, allowing you to sort etc.
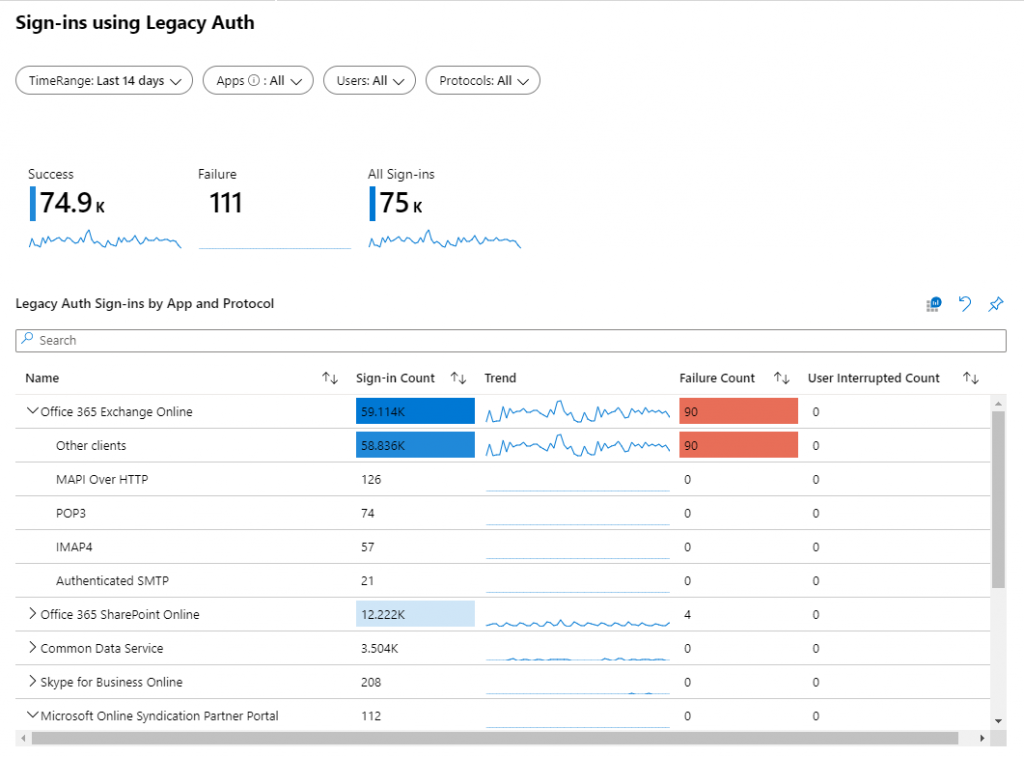
Use the Sign-ins using Legacy Auth workbook
Another option is to use the Sign-ins using Legacy Auth workbook
Steps to migrate from Basic/Legacy authentication to Modern Authentication
Step 1: Determine if you are affected, the longer you are running Exchange Online the higher the chance
Step 2: Determine which users are still using Basic/Legacy authentication, if you have processes running using EWS transition those to use the Microsoft Graph.
Step 3: Determine if these users are using a mail client which supports Modern Authentication, if you have clients which do not support Modern Authentication you must upgrade those clients first
Step 4: Turn on Modern Authentication and verify whether clients connect to EXO using Modern Authentication, you can check this for example in the Outlook Connection Status which should display Bearer* instead of Clear* – see this article for more information.
Step 5: Continue with clients still using MAPI over HTTP, POP3, IMAP4 and help users to transition to MAPI – you can do this by automation, creating user instruction or helping out those users one by one depending on amount and diversity of solutions used
Step 6: Disable all protocols using basic/legacy authentication on the mailboxes of the users
Step 6 (Updated august 2020): Disable basic/legacy authentication either in the default Authentication Policy, or by creating a custom policy and applying it to your users.
You can modify the default authentication policy by modifying the UI in the Microsoft 365 Admin Center.
If you want more granular control, you can use PowerShell to define one or more authentication policies which you can apply to users.
Step 7: Keep measuring whether basic/legacy authentication is used, once there are no clients anymore using basic/legacy authentication, enable the “Block legacy authentication to Azure AD” Conditional Access policy to make sure that the door stays closed.
Conclusion
Microsoft disabling basic/legacy authentication on October 13 this year can have a huge impact on your organization if your clients are still using basic/legacy authentication. If you start today, you should still have enough time to make sure that you are ready for the moment that Microsoft flips the switch. Even though there is a chance that Microsoft will postpone the change if they determine that many customers have not made preparations, the switch will be performed in the near future. So you should better be prepared.
References
Upcoming changes to Exchange Web Services (EWS) API for Office 365, March 7th 2018
Improving Security – Together, September 20th 2019
Basic Auth and Exchange Online – February 2020 Update, February 25th 2020
Disable Basic authentication in Exchange Online
How to: Block legacy authentication to Azure AD with Conditional Access
Enable or Disable POP3 or IMAP4 access for a user
Azure AD Authentication Library for .NET
Enable modern authentication in Exchange Online
How modern authentication works for Office 2013 and Office 2016 client apps
Need clarification on the sentence Even if you have Modern Authentication enabled, if a user is still able to access his/her mailbox using legacy/basic authentication.”
Should it instead read “Even if you have Modern Authentication enabled, a user is still able to access his/her mailbox using legacy/basic authentication.”
?
The context is to clear up a misconception – Can you simultaneously have BOTH Modern Authentication AND Basic Authentication enabled at the same time?
In other words are Modern and Basic mutually exclusive or not? If they are not, and can be enabled at the same time, do mail clients that use Modern use Modern, and those that can’t use Basic?
Is the safest procedure to first enable Modern to reduce the attack surface by use of safer protocols for those clients that can, but to not disable Basic to prevent cutting off those still using old clients?
Trying to avoid a massive Scream Test when we enable Modern Auth for a very large organization.
Thanks and GREAT ARTICLE!
Hi Josef,
Thank you for leaving a comment,
First of all, you are right about the sentence, it should be “Even if you have Modern Authentication enabled, a user is still able to access his/her mailbox using legacy/basic authentication”. So the idea is that if you enable Modern authentication, you do that for clients accessing the EXO environment using the MAPI protocol, if on the other hand POP/IMAP/EAS are still enabled (which use legacy authentication), and the user configures his/her mailclient to connect using one of these protocols, the connection is still basic.
Migration towards Modern authentication in an environment where multiple ways of connecting mailboxes is used, should be (IMHO), to first make sure that newly created email accounts connect correctly right away. So put everyone in a Group, create the conditional access policies for blocking legacy authentication and forcing the outlook client – exclude the group with all the current users, so that if a new user is created (and not member of the group) that user can only connect using Modern authentication. Also disable all of the unwanted protocols on the mailboxes of the new users.
Step 2: Would be to disable “not in use” protocols on the mailboxes of the users, so f.e. if a user is using IMAP currently, make sure that you disable all the other protocols so that yo know for sure that the user cannot configure another client using POP for example
Step 3: Instruct users to move towards a supported email client (Any client on managed devices/Outlook on non-managed devices – the idea should be that we should be able to manage the data) – once moved to the preferred way, remove the user from the group (therefore making the already created CA policies applicable to that user as well)
Step 4: Continue doing that until the group is almost empty.. I don’t think that the group can become totally empty in a complex hybrid environment but it shouldn’t contain a lot of accounts
Step 5: For the accounts still in the group, create additional CA policies which only allow connections from trusted IP ranges.
I hope this answers (some) of your questions, transforming towards Modern authentication is a complex process and should be carefully planned. I totally agree that you want to avoid the massive Scream Test 🙂
/Kenneth
Hello Kenneth,
Great article, thanks for that.
I’m currently working on the analysis of all our legacy authentications in Azure to prepare the future disablement.
I have a simple question, when I go around the sign-ins log, under client AP column I can filter by POP and IMAP (but not POP3 or IMAP4) in the legacy protocols. I want to be sure before continuing my investigation, Microsoft will disable POP3 and IMAP4 but not POP3TLS, POP3S, IMAPS, IMAP TLS right?
Thanks,
Javier
Hi Javier,
Thanks for visiting my blog.
Microsoft states that the following options are considered legacy authentication protocols, so I assume that when you create a CA policy that below protocols will be blocked – haven’t tested each of them individually though.
Authenticated SMTP – Used by POP and IMAP client’s to send email messages.
Autodiscover – Used by Outlook and EAS clients to find and connect to mailboxes in Exchange Online.
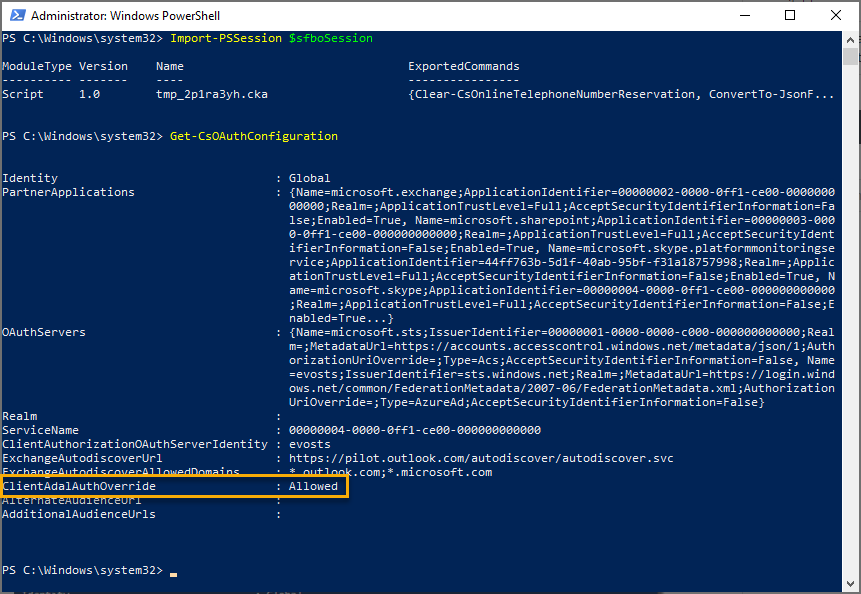
Exchange Online PowerShell – Used to connect to Exchange Online with remote PowerShell. If you block Basic authentication for Exchange Online PowerShell, you need to use the Exchange Online PowerShell Module to connect. For instructions, see Connect to Exchange Online PowerShell using multi-factor authentication.
Exchange Web Services (EWS) – A programming interface that’s used by Outlook, Outlook for Mac, and third-party apps.
IMAP4 – Used by IMAP email clients.
MAPI over HTTP (MAPI/HTTP) – Used by Outlook 2010 and later.
Offline Address Book (OAB) – A copy of address list collections that are downloaded and used by Outlook.
Outlook Anywhere (RPC over HTTP) – Used by Outlook 2016 and earlier.
Outlook Service – Used by the Mail and Calendar app for Windows 10.
POP3 – Used by POP email clients.
Reporting Web Services – Used to retrieve report data in Exchange Online.
Other clients – Other protocols identified as utilizing legacy authentication.
See: https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/block-legacy-authentication#legacy-authentication-protocols
Microsoft has announced that Modern Auth support for POP and IMAP in EXO is rolling out, see: https://techcommunity.microsoft.com/t5/exchange-team-blog/basic-auth-and-exchange-online-february-2020-update/ba-p/1191282 but besides that I haven’t found any documentation doing some further explanation on this yet (whether POP3TLS,POP3S,IMAPS,IMAPTLS is considered “Modern”) – I created a Github issue for that as we speak: https://github.com/MicrosoftDocs/OfficeDocs-Exchange/issues/2004
There is another issue with the Conditional Access policy as well, the fact that it block “Legacy authentication” as a whole, this can mainly cause issues with backup products (like Veeam) which due to API constraints still must access SharePoint using an account via Legacy Authentication. Those accounts must be excluded from the Block Legacy Authentication policy, then to keep working. The wait if for Microsoft to come with an update to their API’s so that backup products can fully leverage Modern Authentication as well.
Sorry for the long answer, it just isn’t simple and there are a lot of exceptions and things to consider. Starting with the reporting based on sign-in logging is a good starting point though!
/Kenneth
https://docs.microsoft.com/en-us/exchange/clients-and-mobile-in-exchange-online/disable-basic-authentication-in-exchange-online
Hi Kenneth,
Your article cleared many of my questions about legacy and modern authentication.. Nice article.
Thanks !
Thank you Purna,
If you have any follow up questions please let me know. I will find the answers and update the article if needed.
Regards,
Kenneth
Hi Kenneth,
Its Greate Article.
I am a dotnet Developer and we need to download the emails/read the emails for the automation process.
For that we have used the .Net Nuget package “Microsoft.Exchange.WebServices” and its working fine. for this new Authentication type is there a change in the existing process.
Thanks in advance for the help.
Regards,
Srikanth G
Hi Srikanth,
As long as the Nuget package accesses EWS using Modern Authentication you should be fine. I’m not familiar with this package though, so you should test.
You can do this using a “Block Legacy Authentication” Conditional Access policy which you target to the user using the functionality of the package.
Hope this helps,
Regards,
Kenneth
Great!
No, very FEW commercial client support Modern Authentication, obviously because Microsoft wants it that way. Outlook is the ONLY email client that DOES support it. Oh guess what! It’s a Microsoft Product!
I have followed the steps above, but Mac O/S outlook does not support this? Windows 10 users do not have any issues.
Outlook On The Web and Outlook Desktop (MAPI) are the only Email Apps allowed to use.
Microsoft Outlook running on top of macOS is supported, at least if you are running a supported version. I have several of these devices in the environment where I’m doing a large migration at the moment.
Hi Clemens, token based authentication instead of user/id password based authentication is not something that only Microsoft is doing. It’s also not true that only Outlook supports it, see the article by Michel to which I refer describing how to configure Thunderbird here: https://eightwone.com/2020/07/01/configuring-exchange-account-with-imap-oauth2/