In August last year, I published eight articles in a series on Conditional Access, and later when finished I decided to bundle those articles in a paper which I made available on the TechNet Gallery. In March this year, Microsoft decided to retire the TechNet Gallery, so I had to find another solution to host this paper and some of the additional workflows and spreadsheets I posted as well. For now I’ve decided to host these on GitHub since that is an easy accessible location as well.
The articles I wrote at that time, will remains as is, and I’ve decided to update the paper once in a while to reflect the current status of Conditional Access. Even though some of the information in the articles is outdated, I still think that they can be of value.
Below I’ve summarized the articles I published last year:
- Conditional Access demystified, part 1: Introduction
- Conditional Access demystified, part 2: What is Conditional Access?
- Conditional Access demystified, part 3: How does Conditional Access work?
- Conditional Access demystified, part 4: Designing a Conditional Access strategy
- Conditional Access demystified, part 5: Implementing Conditional Access
- Conditional Access demystified, part 6: Troubleshooting Conditional Access
- Conditional Access demystified, part 7: Modifying Conditional Access to suit your special needs
- Conditional Access demystified, part 8: Resources and further references
So what’s new?
The following updates have been made:
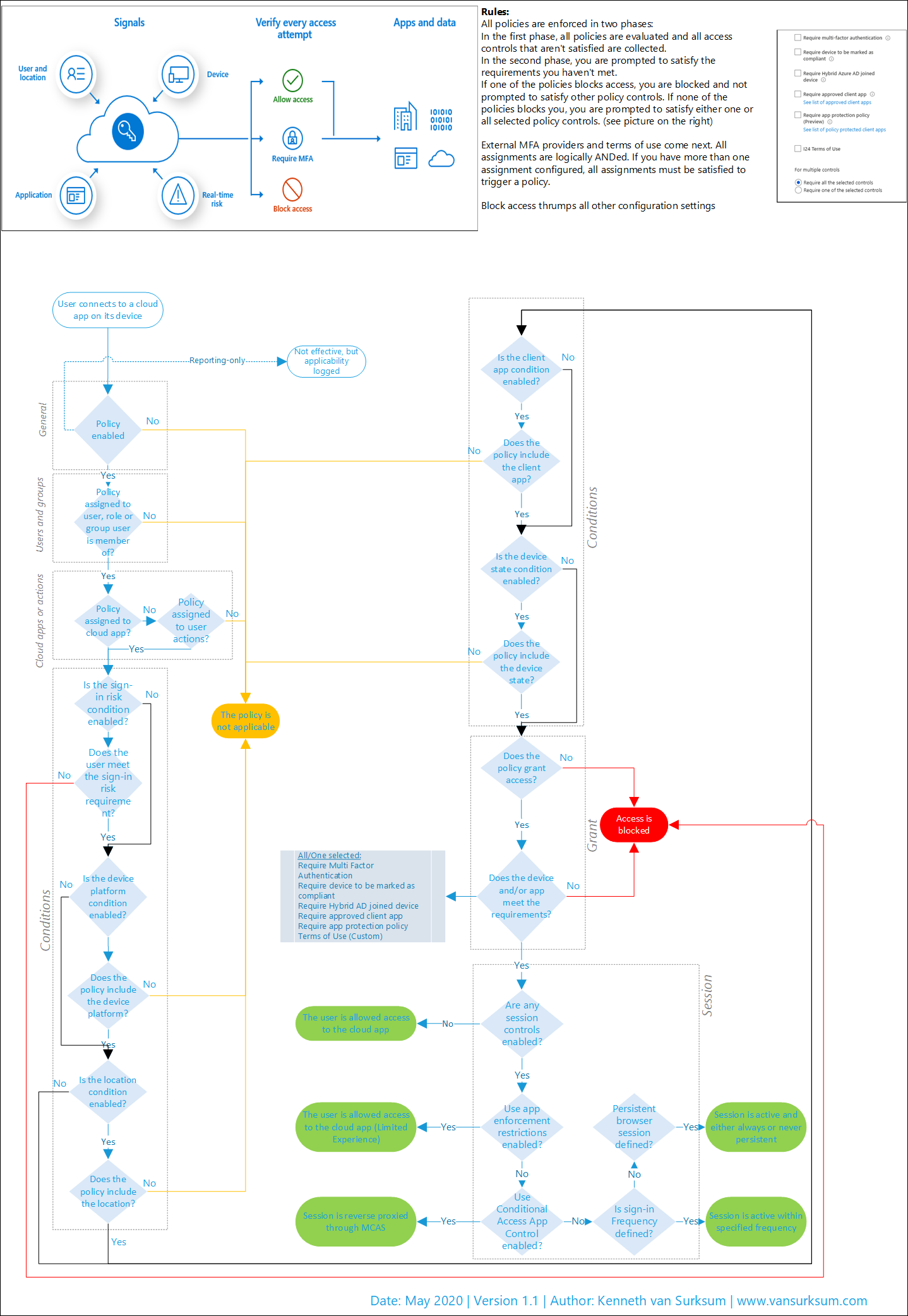
Workflow Cheatsheet
The goal of the cheatsheet was to have an A4 sized flowchart which can help you while you are either trying to understand your current policies, troubleshooting or just want to make sense of how Conditional Access policies work.
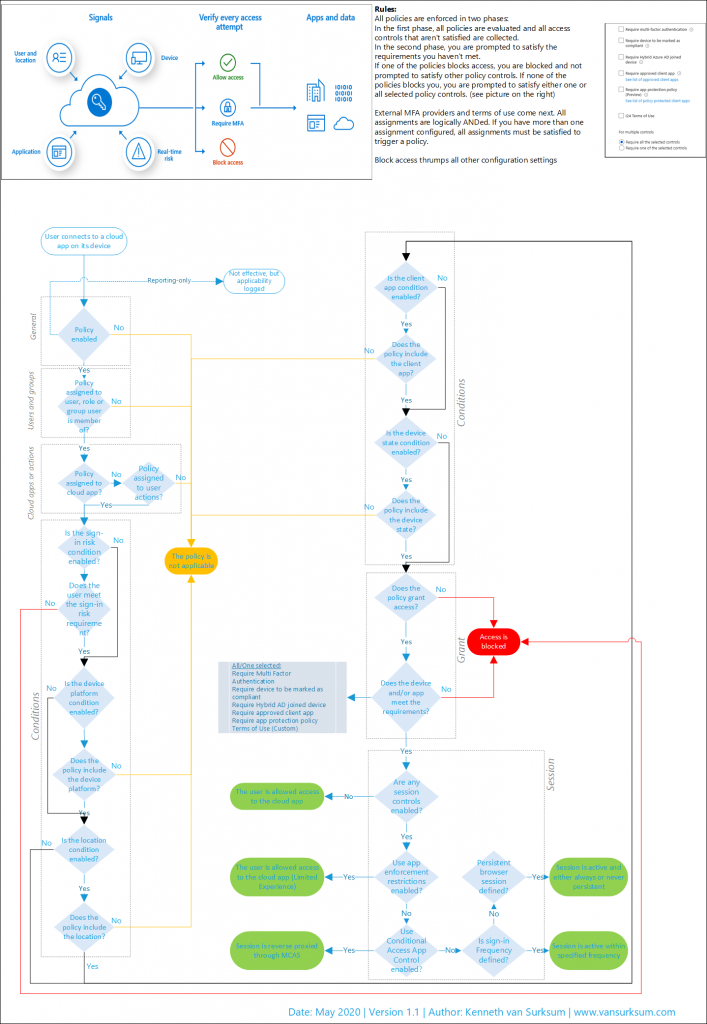
Download: Conditional Access Workflow – v4.pdf
Implementation workflow
The goal of the implementation workflow is to help you get started when you want to implement Conditional Access, based on the information in the paper the workflow can be really helpful to make the necessary steps visible. I’ve updated the workflow by removing the Baseline policies, for which Microsoft decided not to continue with them in favor of Security Defaults, see: Microsoft deprecates Conditional Access baseline policies in favour of Security Defaults, here is what you need to know and do. Instead I create references to the Microsoft recommended Conditional Access policies which have the same functionality as the Baseline policies.
Download: Conditional Access Implementation Workflow – V1.2.pdf
Documentation spreadsheet
The documentation spreadsheet (in Microsoft Excel format), can help you to document your current Conditional Access policies, or document the policies you want to create. I found out myself that If you document all your conditional access policies, you automatically see if some policies can be simplified or combined. In the end, it’s better to keep your policies simple and easy to understand.
To give you a start, I also integrated the described policies from the workflow in the documentation spreadsheet to give you a starting point.
Download: Conditional Access Policy Description-v1.1.xlsx
Conditional Access Demystified Whitepaper
The paper has been updated with the latest information to my knowledge, between august last year and May 2020 some things have changes, and I’m sure some things will change again in the next coming months.
In the paper I created some references to articles or implemented information from them which I wrote in the meantime, like:
- Azure AD Identity Protection deep dive
- License requirements for administering Microsoft 365 services
- Extending Conditional Access to Microsoft Cloud App Security using Conditional Access App Control
- Microsoft is going to disable basic/legacy authentication for Exchange Online. What does that actually mean and does that impact me?
Download: Conditional Access demystified-v1.1.pdf
Conclusion
Updating the conditional access material requires a lot of work and validation, but I hope it was worth it. If it can at least help some people, I’ve reached my goal.
If you have any comments, or find some things which are wrong, please let me know in the comments or by reaching out to me on social media.
16 thoughts on “May 2020 update of the Conditional Access Demystified Whitepaper, Workflow cheat sheet, Implementation workflow and Documentation spreadsheet”