On modern workplaces we use authentication techniques provided by Windows Hello for Business, like biometric and PIN. Due to this, user don’t login with their password all the time. Nowadays Microsoft even recommends to not set any password expiration policies because passwords which expire make users select predictable passwords, composed of sequential words and numbers which are closely related to each other. So, by forcing users to create complex passwords and by making sure that common passwords cannot be used anymore and by using multi-factor authentication techniques we can keep the account more secure.
If users work primarily on their Windows 10 modern workplace and sign-in using their biometric details or PIN, they might forget their password though since it’s never asked. Companies especially see this happening after holidays, where end users returning from their holiday have forgotten their password.
By enabling Self Service Password Reset (SSPR) in your Azure Active Directory you can delegate the task of resetting a password back to the user. This can save you a lot of support calls. The functionality relies on the fact that users have a 2nd authentication factor configured and needs to be setup first by the user before it can be used. SSPR is a functionality which requires at least Azure Active Directory Premium P1 licensing for all users using its functionality.
This blogpost will go through the necessary steps giving you an overview on how to enable it, configure it and use it from both an user and administrator perspective.
Enabling Self Service Password Reset
SSPR can be enabled from the Azure Active Directory admin portal, the settings related to SSPR can be found under the Password Reset section. After enabling the feature for All or a selected set of users (based on Azure AD group). While testing the setup it might be a good idea to enable the functionality for a specific set of users first.
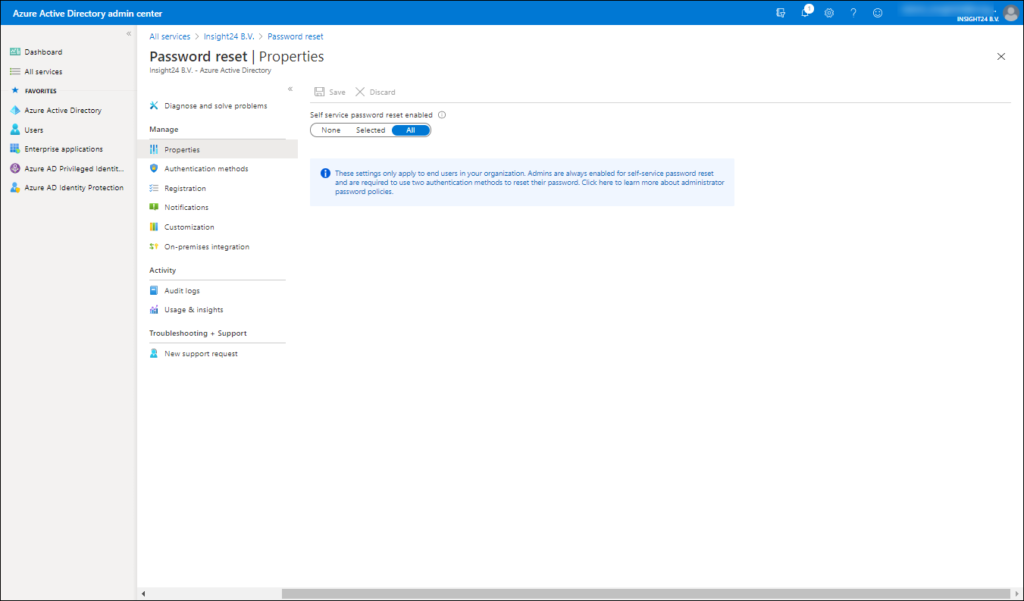
Configuring Self Service Password Reset
You can configure SSPR first without it being enabled, this is handy because you can execute the configuration first, below are the settings you can make:
Authentication Methods
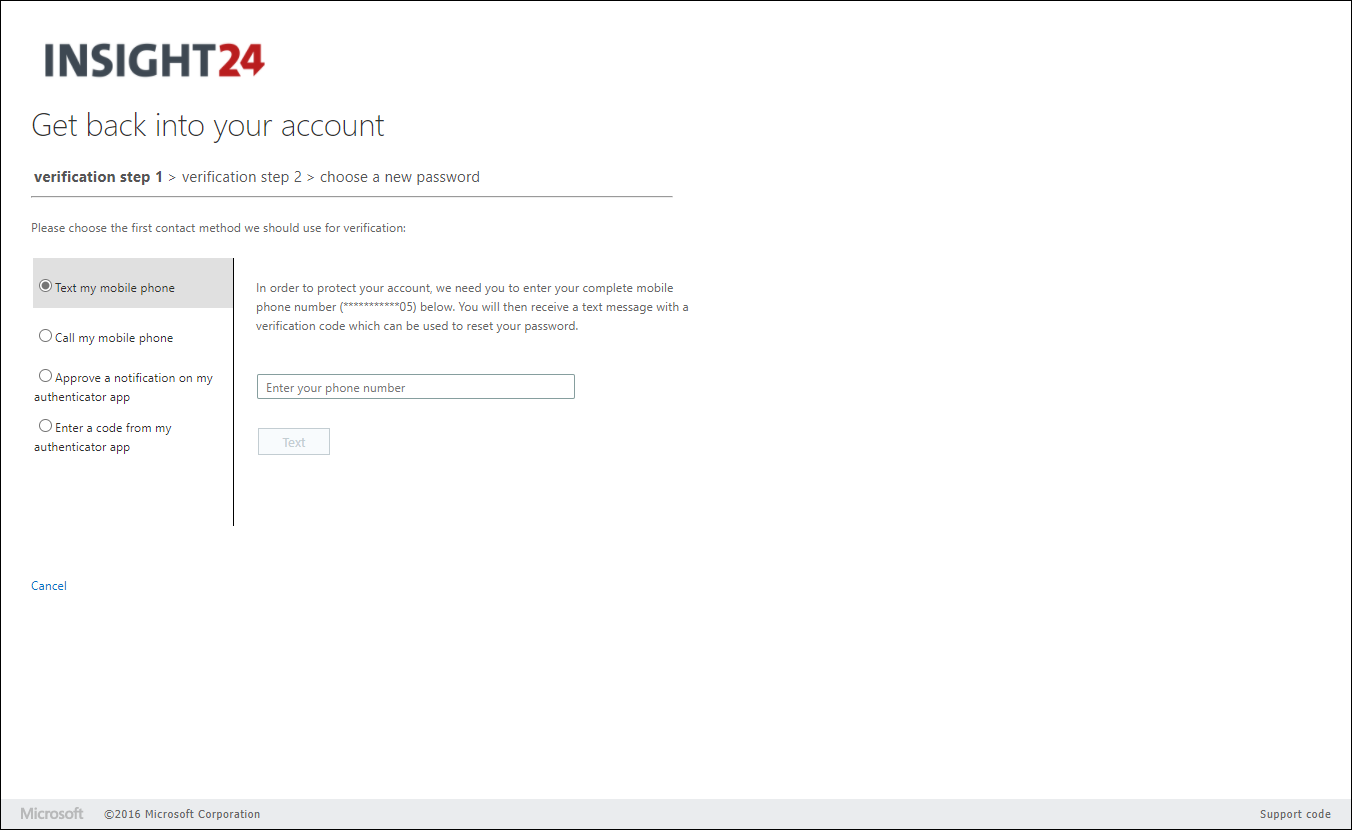
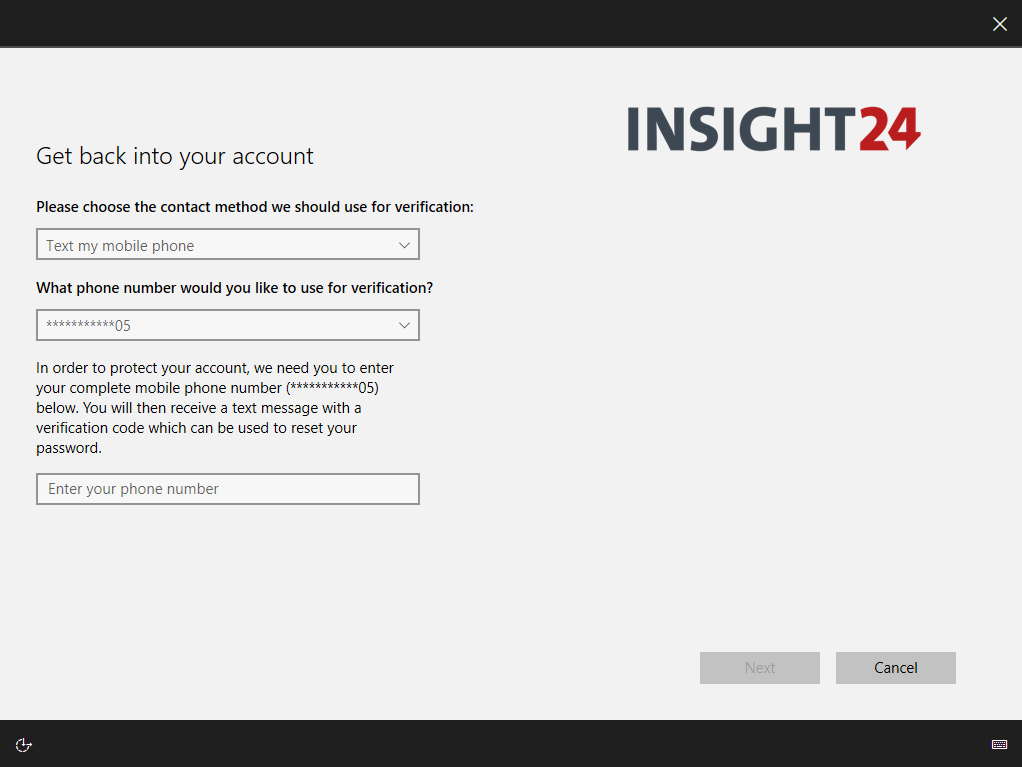
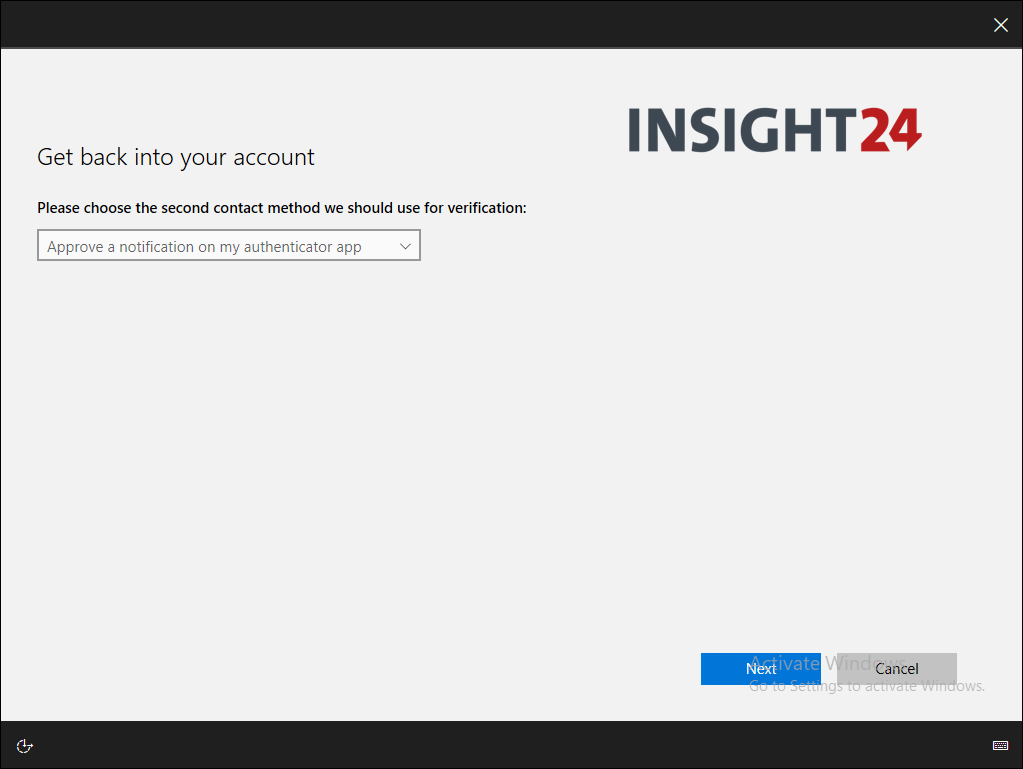
On the authentication methods page you can define the number of alternate methods of identification a user must have to reset their password. This should either be one or two alternate methods.
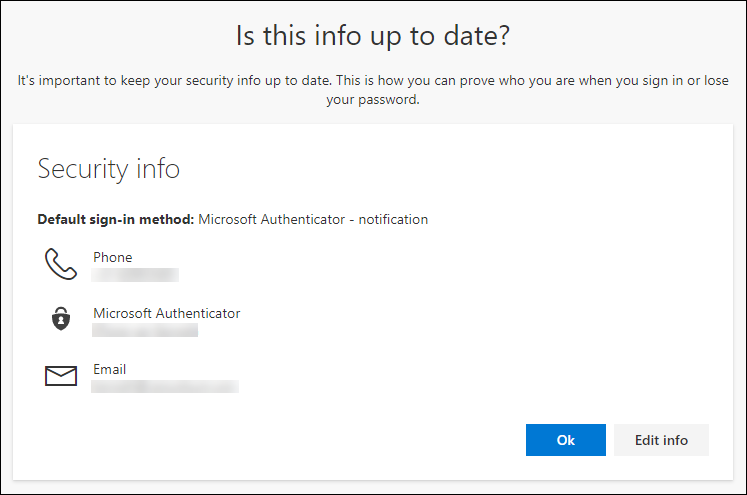
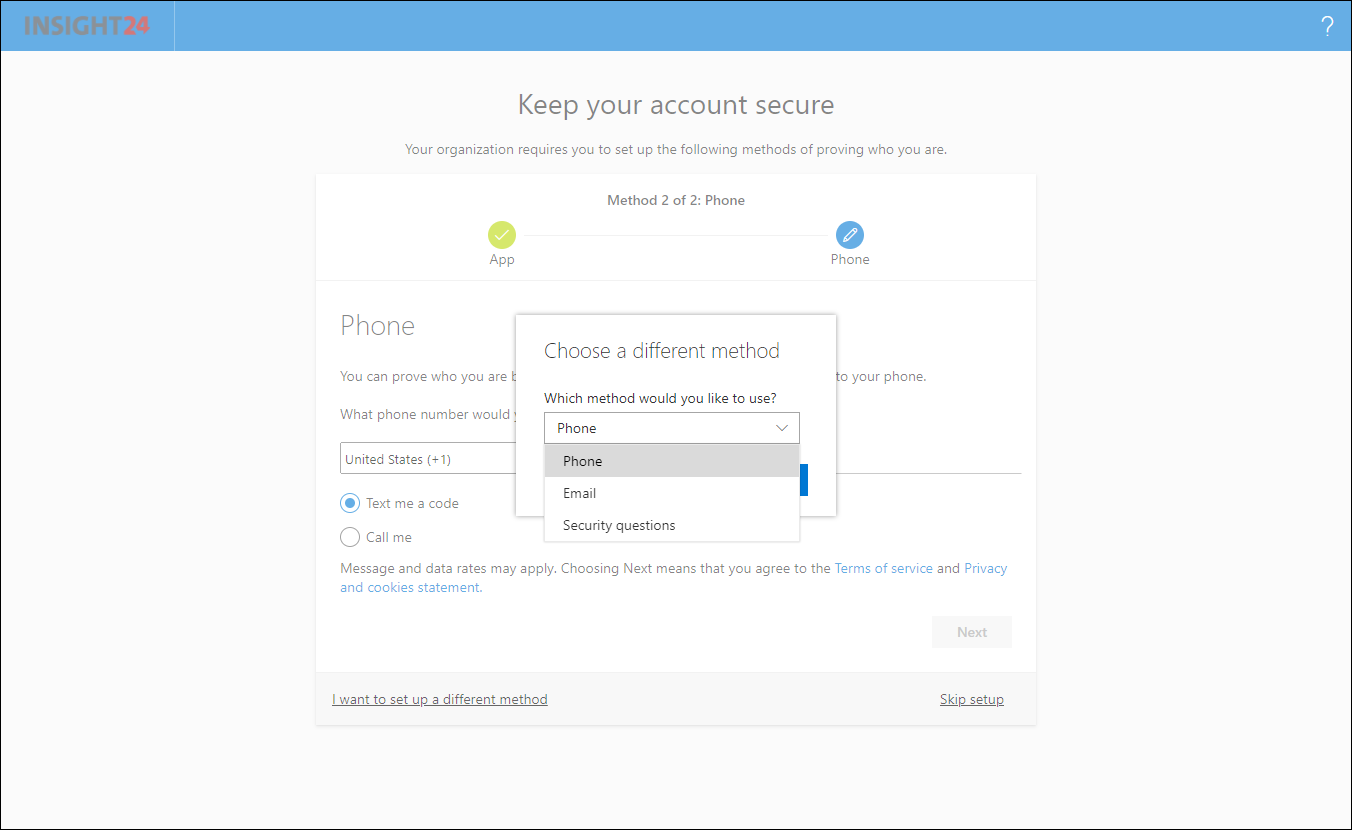
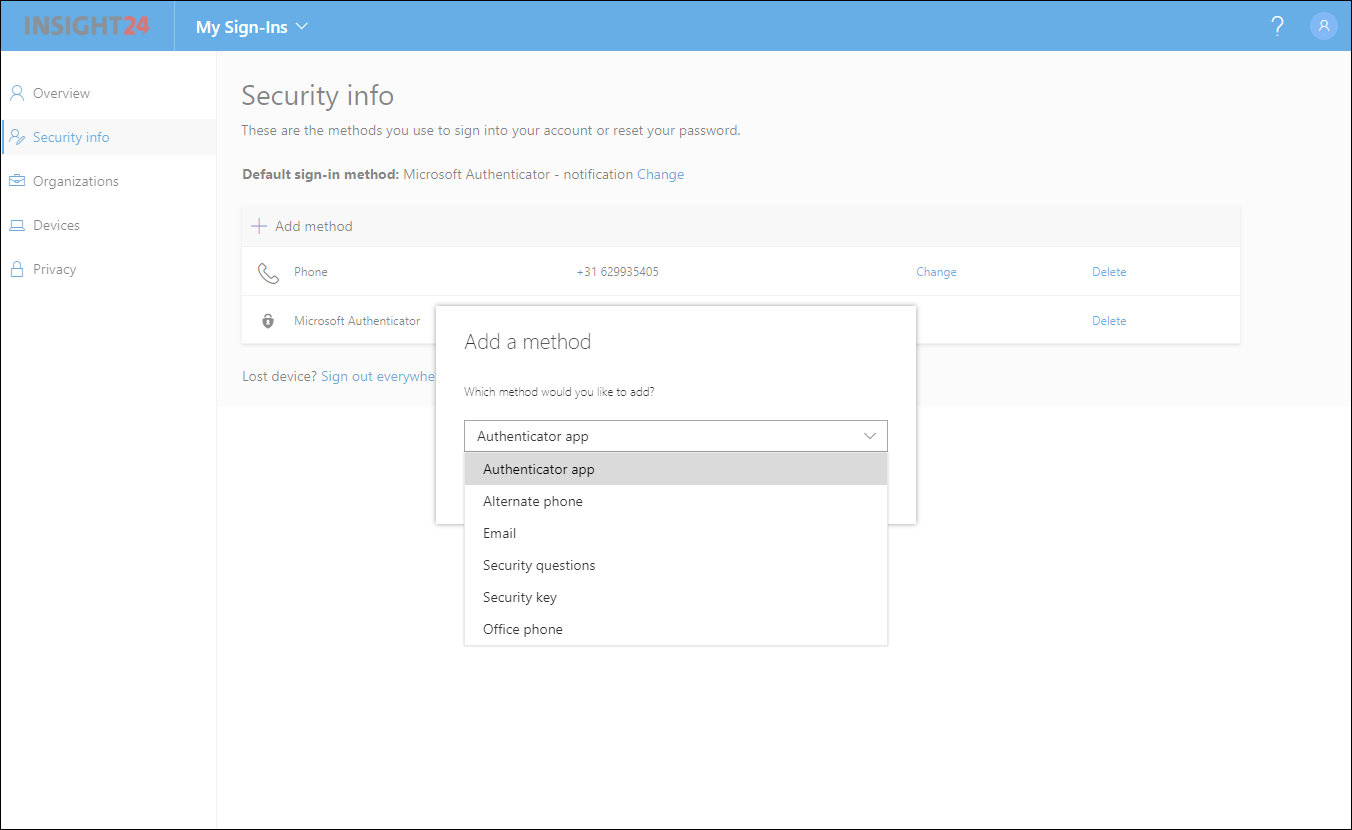
You can also specify which methods are available for the user, to use when using the SSPR functionality. These methods must be registered first of course, the best way to that that is to use the Security Info section on their My Sign-ins page. You can redirect users using the shorturl: https://aka.ms/setupsecurityinfo
The following methods are available:
- Mobile App Notification
- Mobile App code (verification code)
- Mobile Phone
- Office Phone
- Security Questions
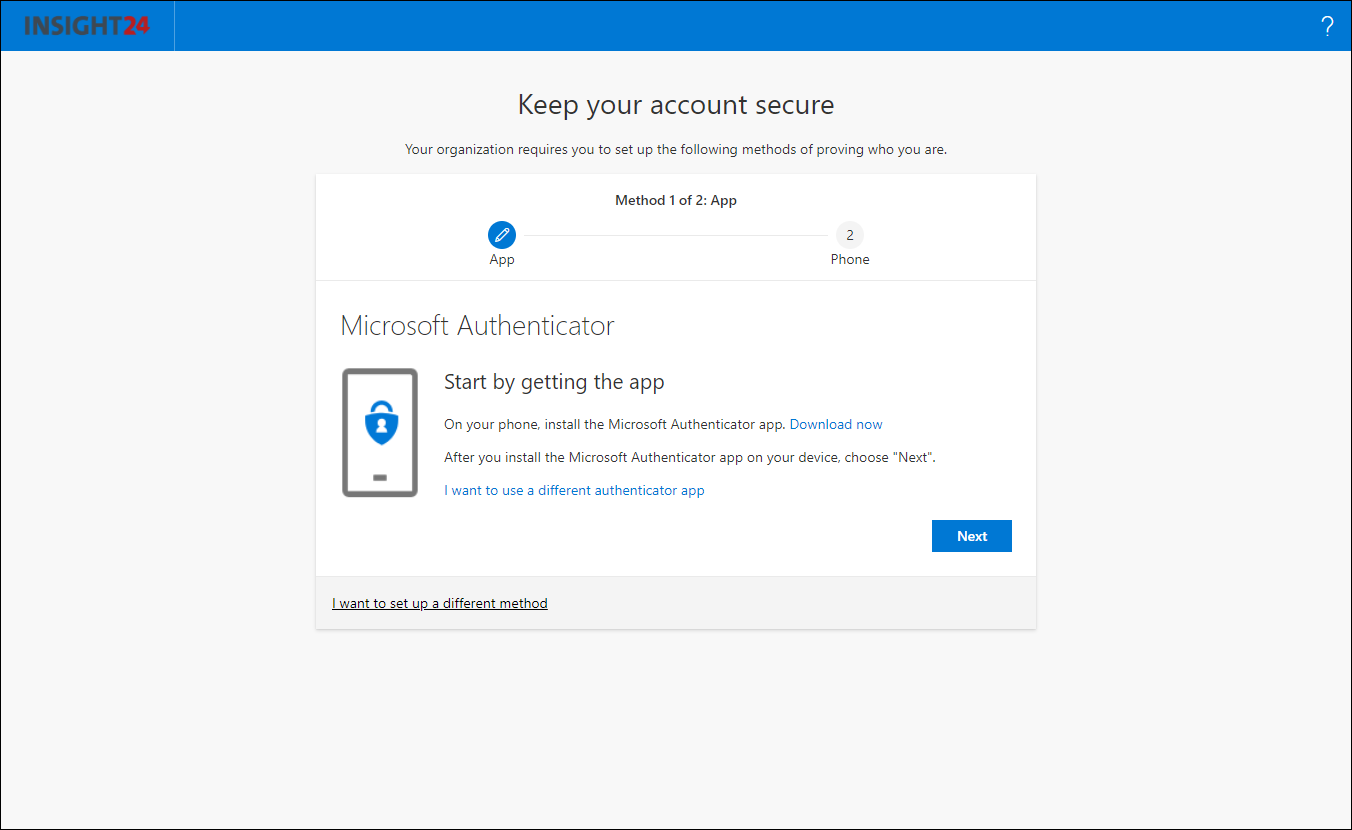
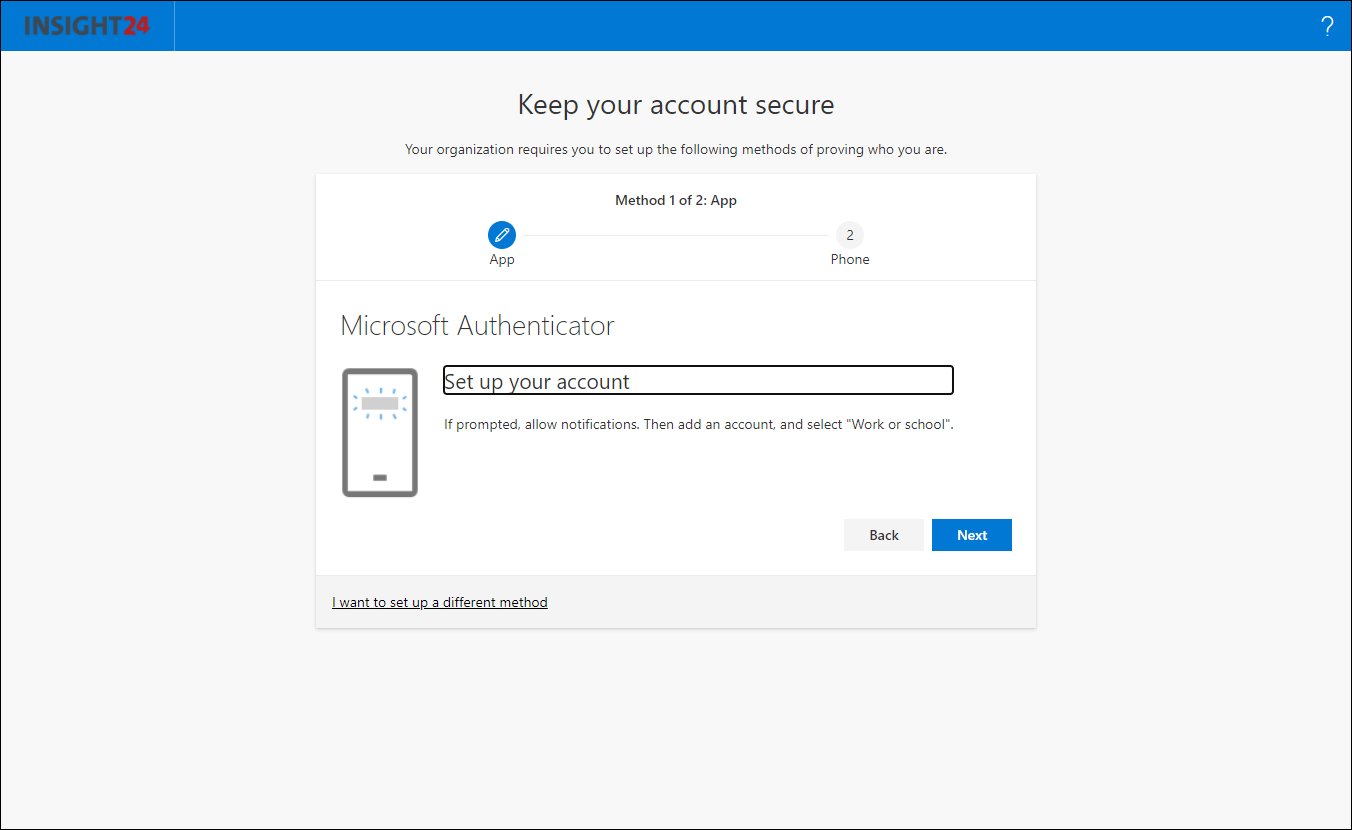
With Mobile app notification and Mobile app code you must have setup the Mobile app first, this can be done by redirecting your users to either the MFA setup page or by using the Security Info registration page. There are some restrictions when using the Mobile app though.
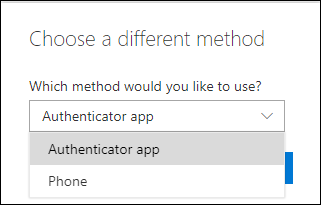
When you configure the number of alternate methods of identification to “1”, you can only use verification code from the Mobile app and not the Notification option, the option to select Mobile app notification will be greyed out. When this setting is set to “2”, both options can be used. You also cannot select the Authenticator app and only one additional method, in that case you must at least have two additional methods selected. The reason for this restriction has to do with the fact that the old SSPR registration experience, available via https://aka.ms/ssprsetup didn’t provide the option to register for MFA, this is now solved by the new preferred way to setup SSRP (and MFA) by using the Security Info registration page.
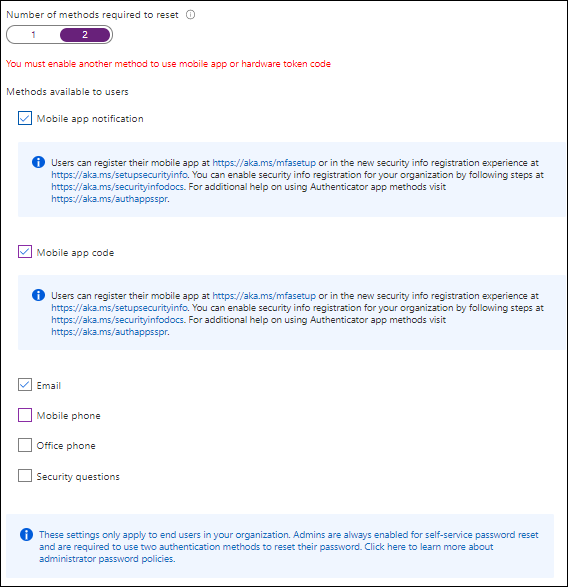
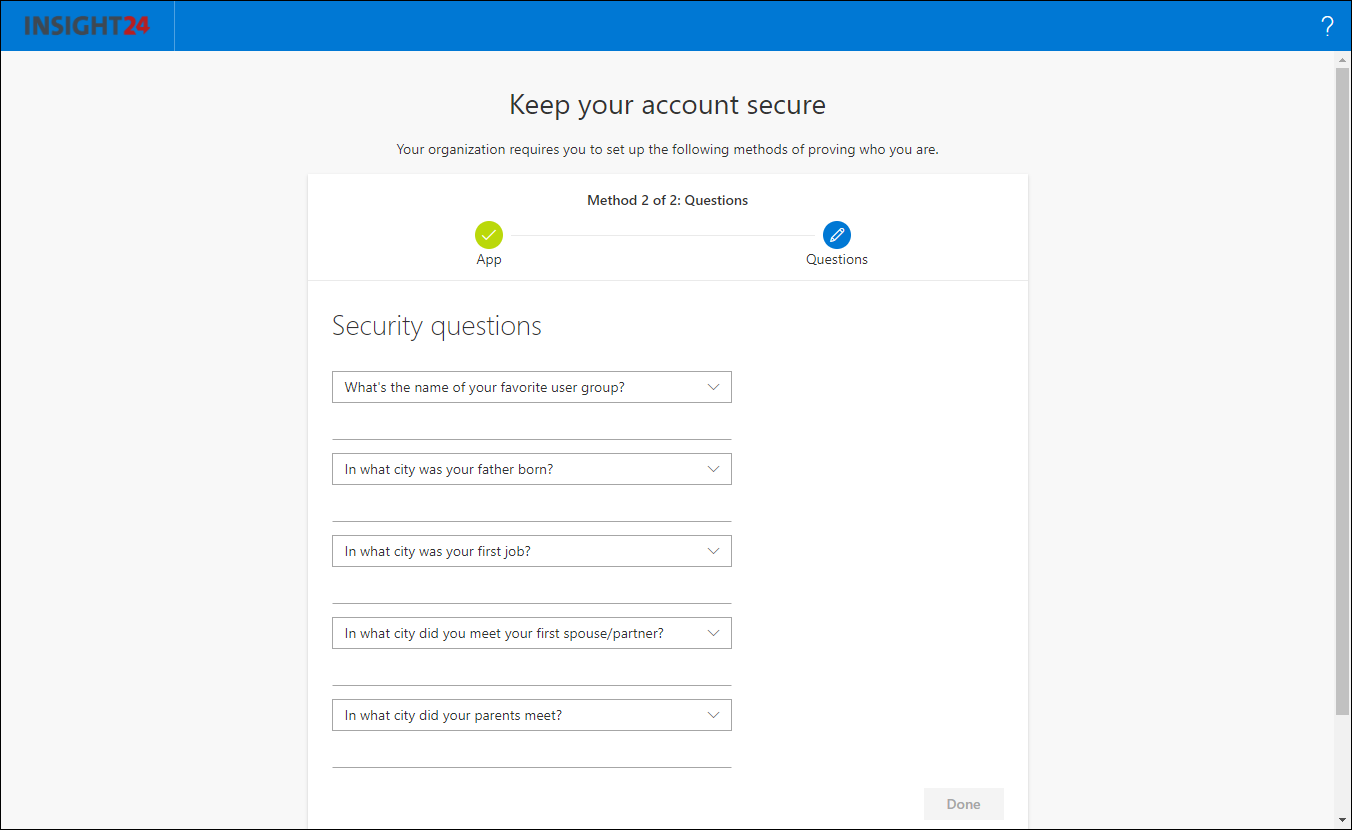
If security questions are selected, new options appear in the configuration page, you must specify the amount of questions the user must answer in order to register, and the amount of questions which must be correctly answered in order to be allowed to reset their password.
To specify the security question, the Administrator can either choose to use Predefined questions, or to create new ones. The predefined questions which can be selected are:
- In what city did you meet your first spouse/partner?
- In what city did your parents meet?
- In what city does your nearest sibling live?
- In what city was your father born?
- In what city was your first job?
- In what city was your mother born?
- What city were you in on New Year’s 2000?
- What is the last name of your favorite teacher in high school?
- What is the name of a college you applied to but didn’t attend?
- What is the name of the place in which you held your first wedding reception?
- What is your father’s middle name?
- What is your favorite food?
- What is your maternal grandmother’s first and last name?
- What is your mother’s middle name?
- What is your oldest sibling’s birthday month and year? (e.g. November 1985)
- What is your oldest sibling’s middle name?
- What is your paternal grandfather’s first and last name?
- What is your youngest sibling’s middle name?
- What school did you attend for sixth grade?
- What was the first and last name of your childhood best friend?
- What was the first and last name of your first significant other?
- What was the last name of your favorite grade school teacher?
- What was the make and model of your first car or motorcycle?
- What was the name of the first school you attended?
- What was the name of the hospital in which you were born?
- What was the name of the street of your first childhood home?
- What was the name of your childhood hero?
- What was the name of your favorite stuffed animal?
- What was the name of your first pet?
- What was your childhood nickname?
- What was your favorite sport in high school?
- What was your first job?
- What were the last four digits of your childhood telephone number?
- When you were young, what did you want to be when you grew up?
- Who is the most famous person you have ever met?
You can also specify some question questions, like “What’s the name of your favorite user group?”
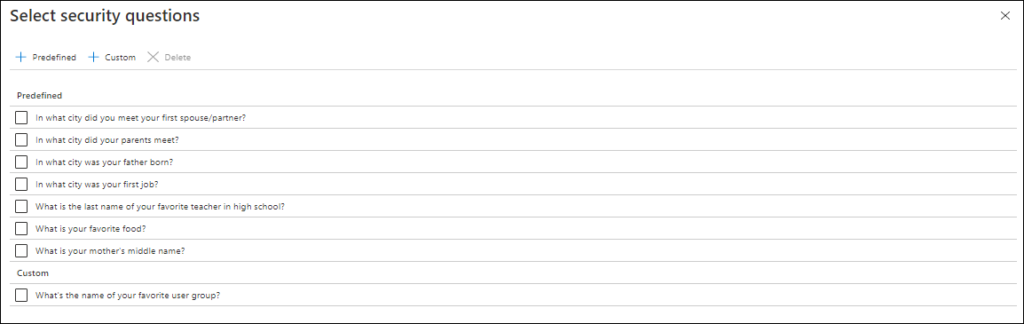
Registration
Under registration you can configure if users are required to register their authentication methods when signing in. This setting only applies to end users. Administrators are always enabled for self-service password reset and are required to use two authentication methods to reset their password.
If registration is required, unregistered users are prompted to register their own authentication information when they sign in for the first time. If registration is not required, you’ll have to provide your users with a link to the Security Info registration page set to “No,” or configure some of the settings on the Authentication methods page of the user properties in Azure AD.
Jan Bakker, wrote an interesting article on how to provision some of the authentication methods coming from other systems which you provide to Power Automate which populate the authentication methods using the Graph API.
Check: Prepopulate phone methods for MFA and SSPR using Graph API
You can also specify the interval in days when users are required to re-confirm their authentication information. If this is set to 0 users never have to re-confirm, the maximum value is 730 days.
Notifications
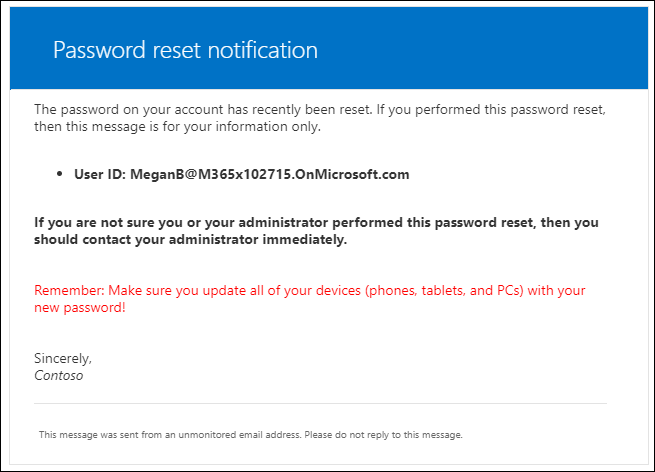
On the notifications page you can specify whether users are notified after their password is reset using the SSPR functionality. The user receives an email on their primary and alternate email address. You can also specify if other admins (global administrators) receive a notification in case one of the administrators changes its password using SSPR.
Customization
On the customization page, you can specify a custom helpdesk email or URL for end users to see. There are quite some scenario’s where SSPR will not work and you might want to provide your end users with information about how to reach out to IT support when needed.
On-Premises Integration
If you are using Azure AD Connect to synchronize your on-premises identities coming from Active Directory to Azure AD you can configure the On-premises integration option.
In order for this to work, you must make sure that password writeback is enabled in the Azure AD connect configuration.
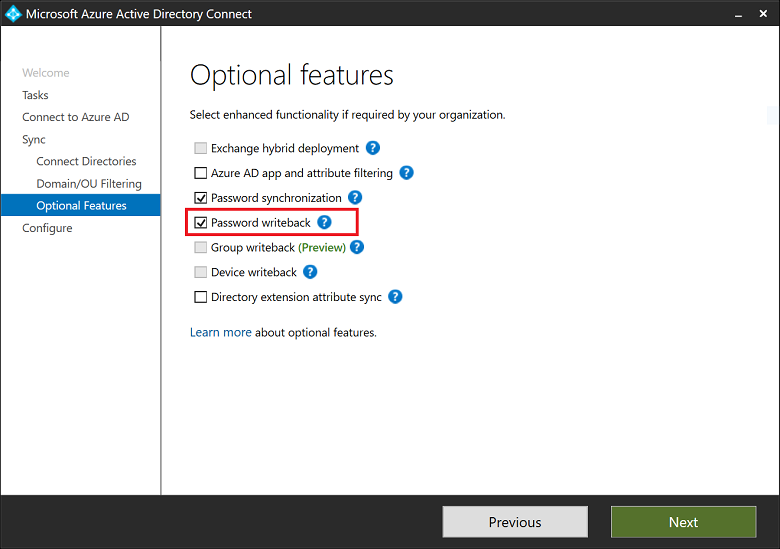
You must also make sure that the on-premises account used for Azure AD connect, has enough rights on the user objects to perform the password reset/unlock of the account. If you used “defaults” during the configuration of Azure AD Connect the MSOL_<random number> account already has the necessary rights. If you decided to use a pre-created account you must verify if this account has the necessary rights. See: Configure account permissions for Azure AD Connect on how to configure the AD account with just enough rights to perform password resets on behalf of the user.
Reporting on SSPR usage
Once SSPR is setup and in use, you can use the Usage & insights page to view some statistics about the registration and usage within your organization.
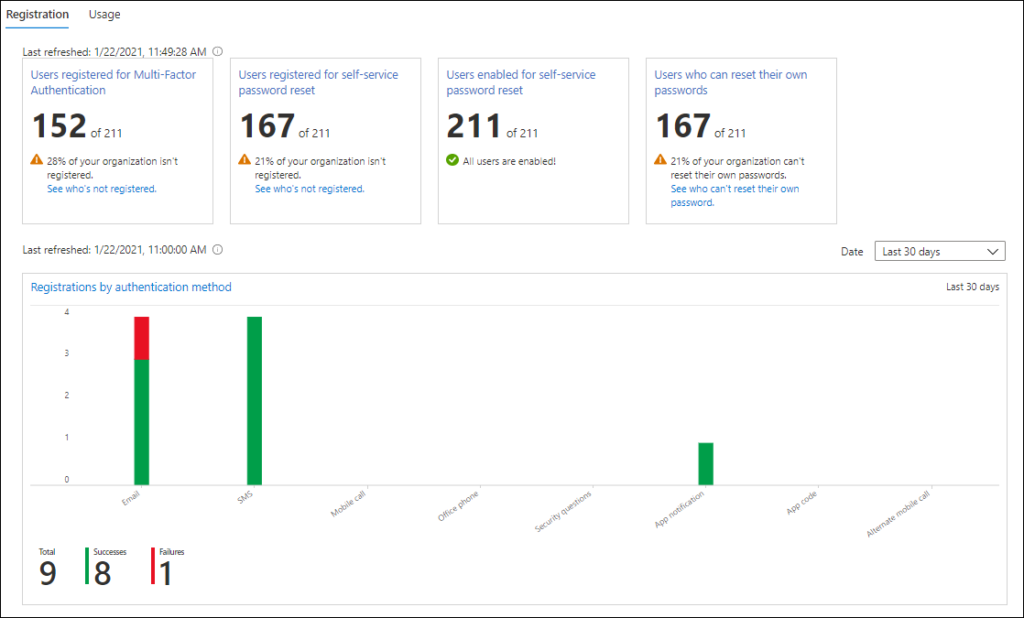
On the Registration page you can see some figures about:
- Users registered for Multi-factor authentication
- Users registered for SSPR
- Users enabled for SSPR
- Users who can reset their own password
The page also provides some hyperlinks to more concrete information, like who the users are not registered for MFA. From that page you can also download the list of users.
On the Usage page you can see a report on the usage of SSPR within your organization. You can specify a maximum timeframe of 30 days, and the report will show you the authentication methods used. Also here you can use a hyperlink to end up on a page with more concrete information.
Setup SSPR as an end user
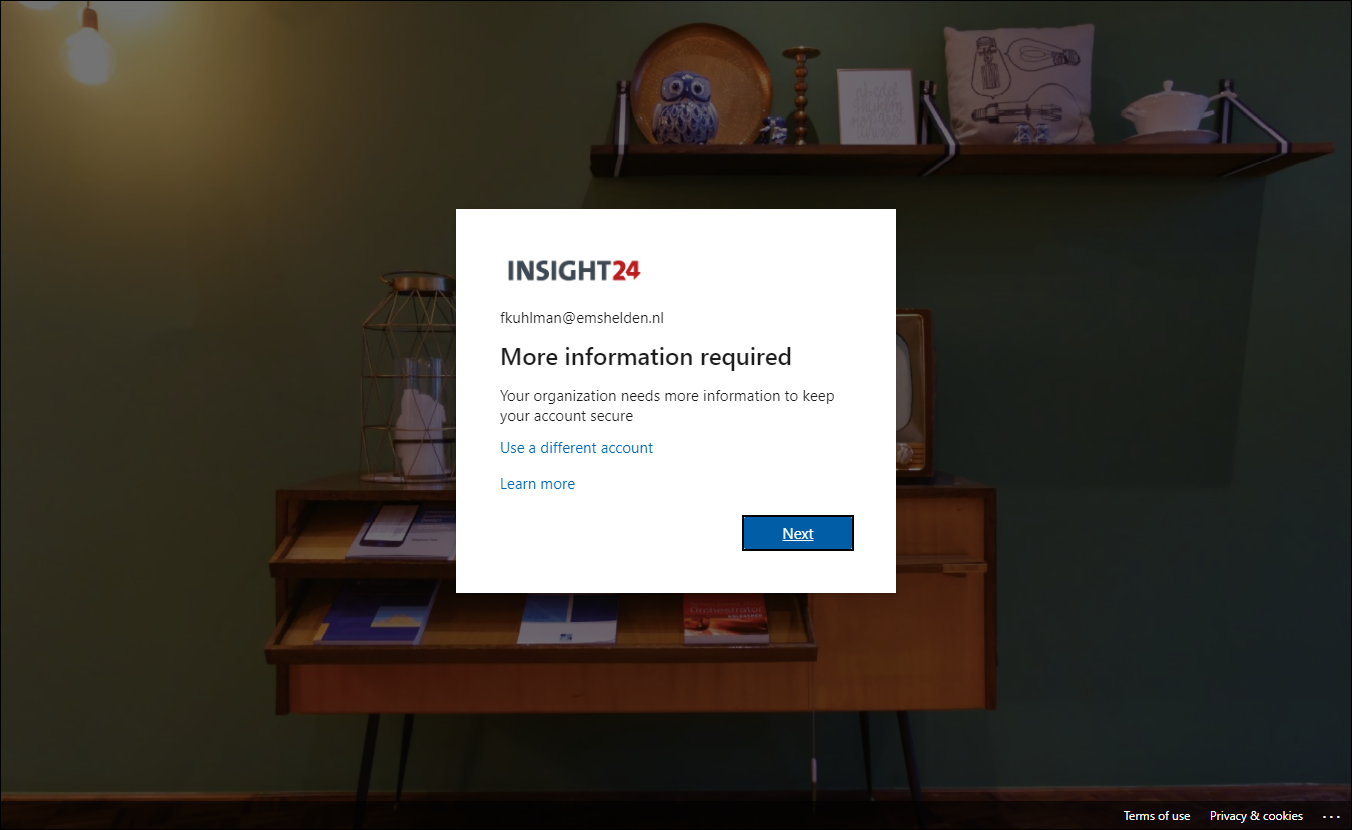
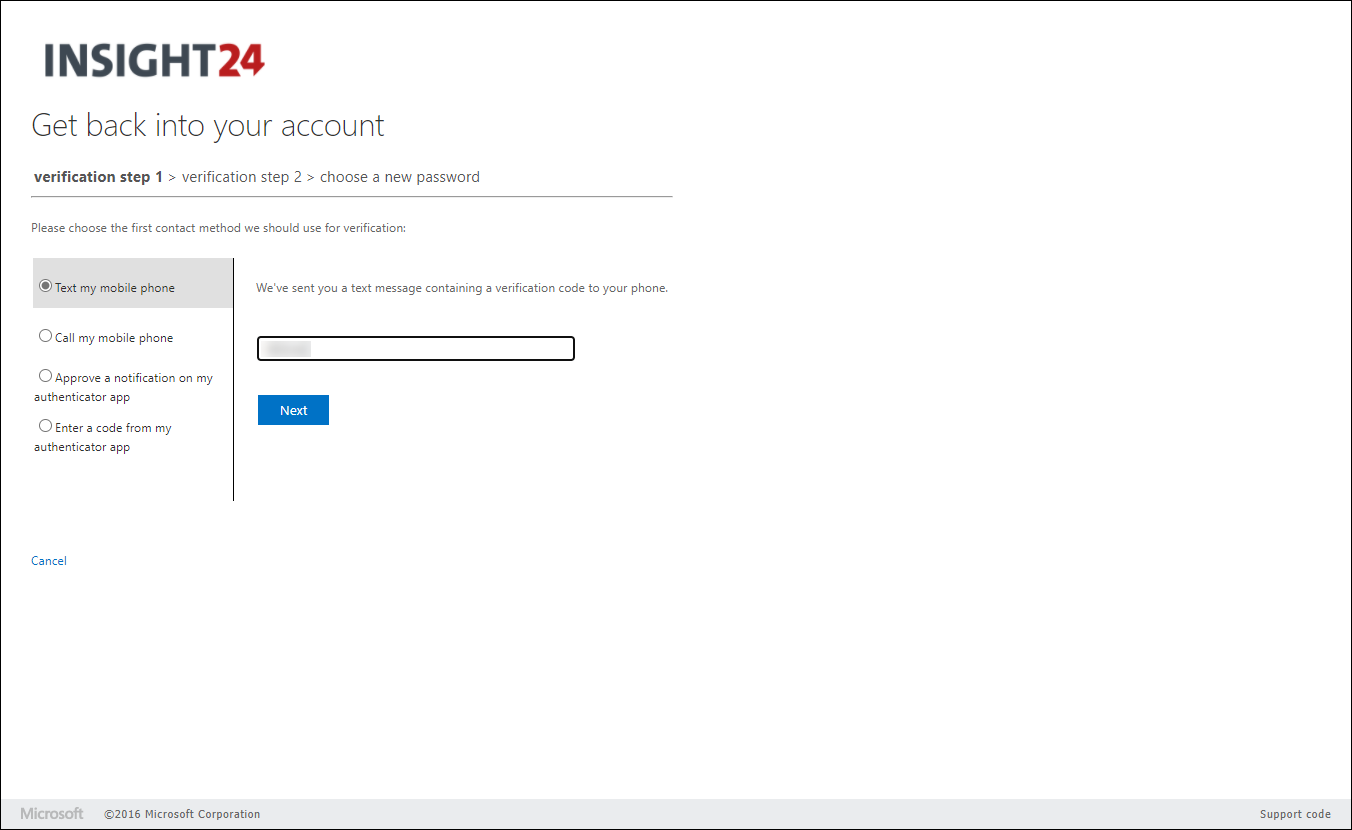
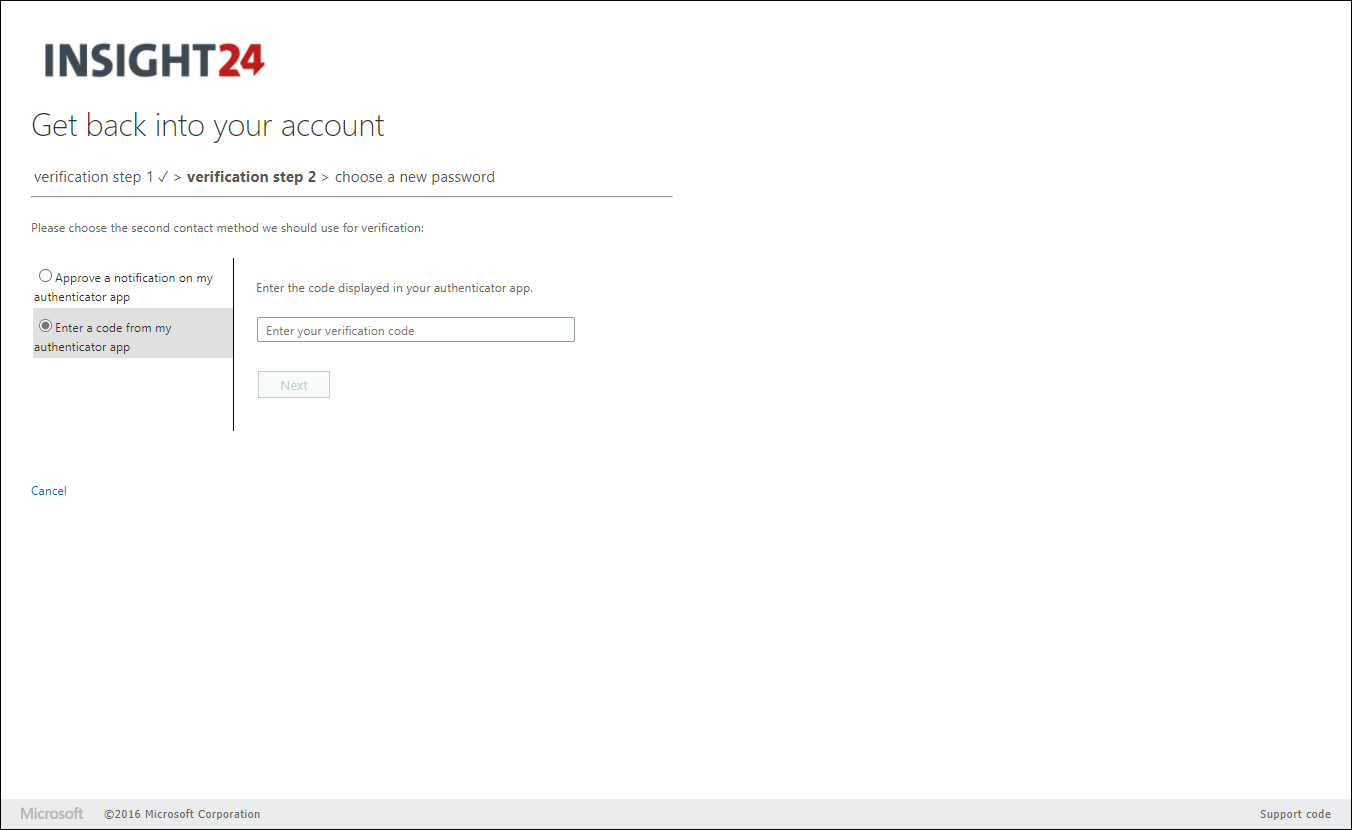
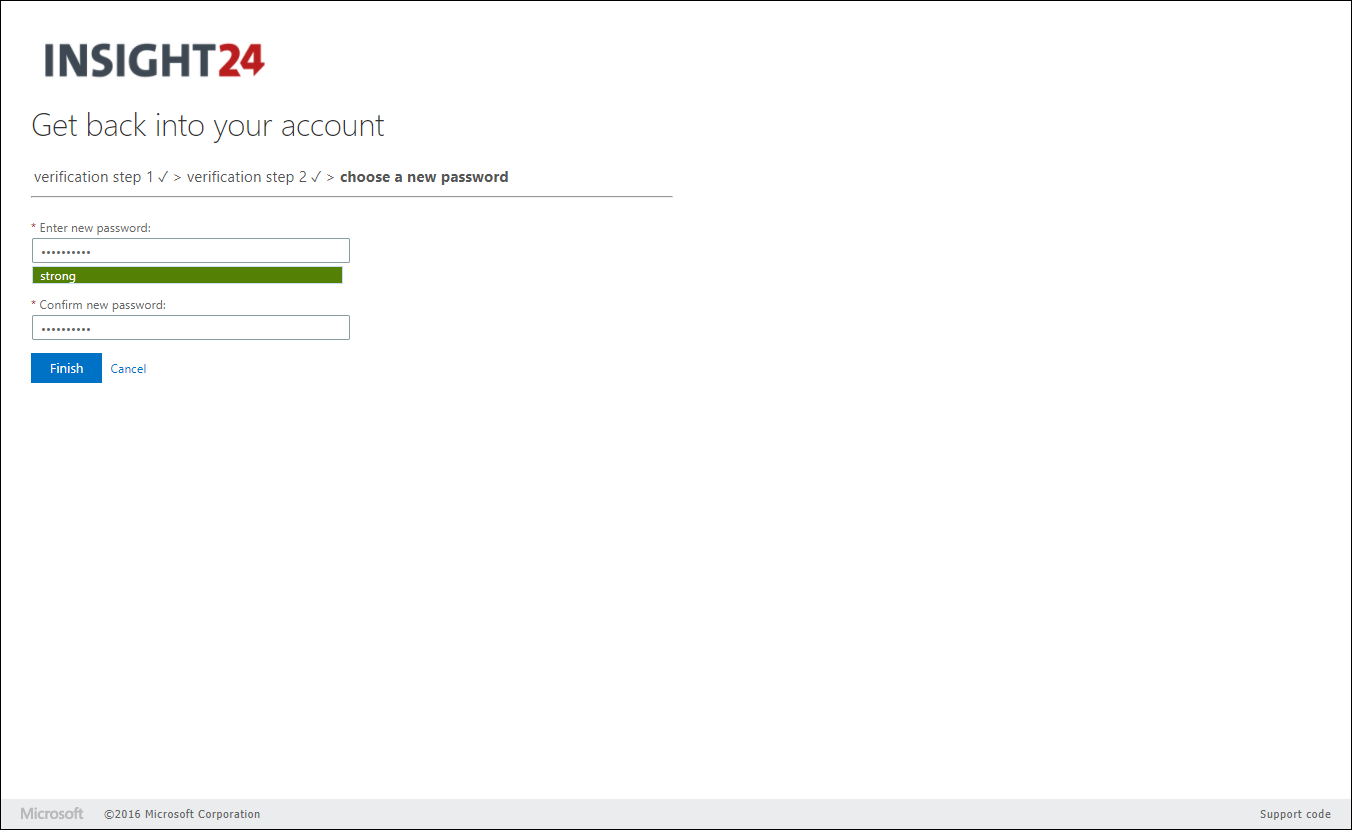
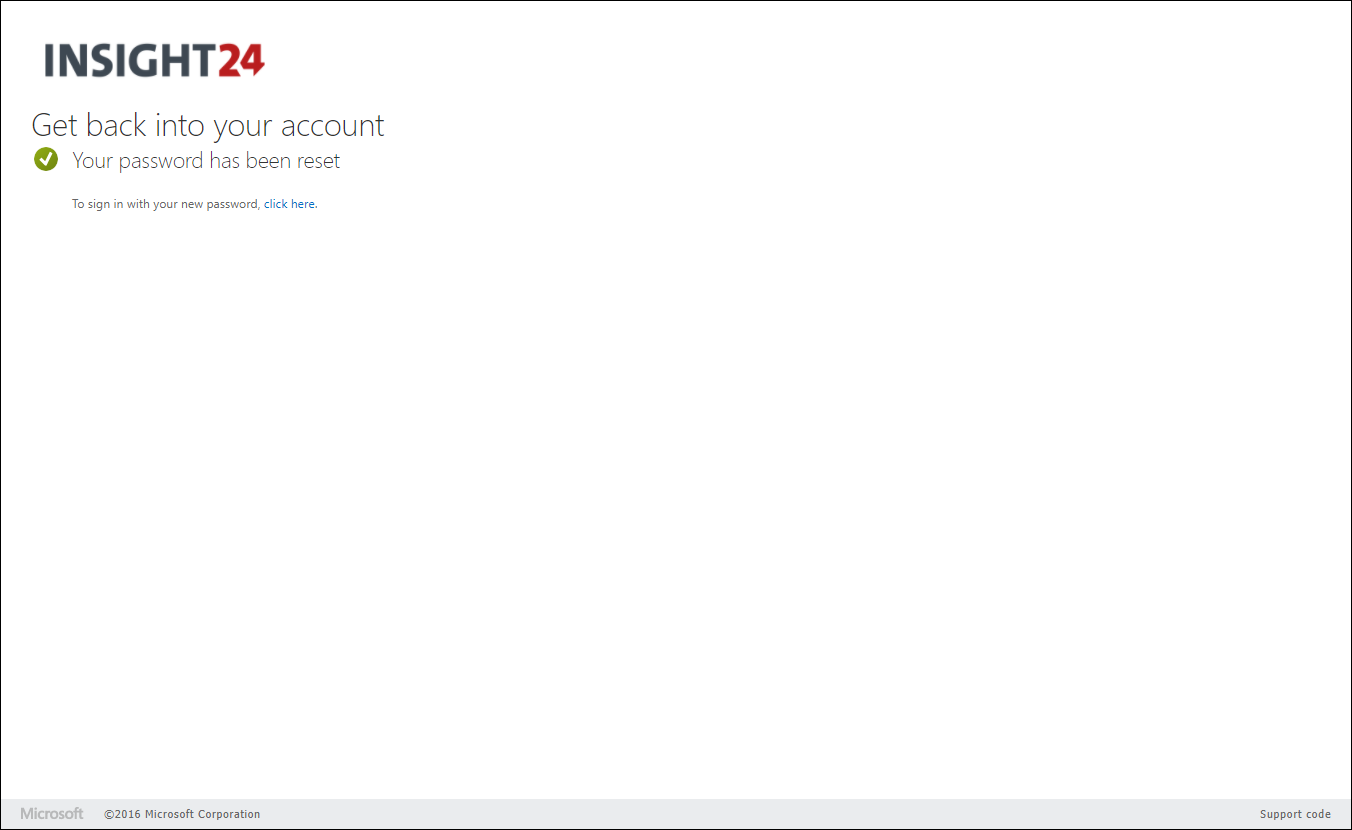
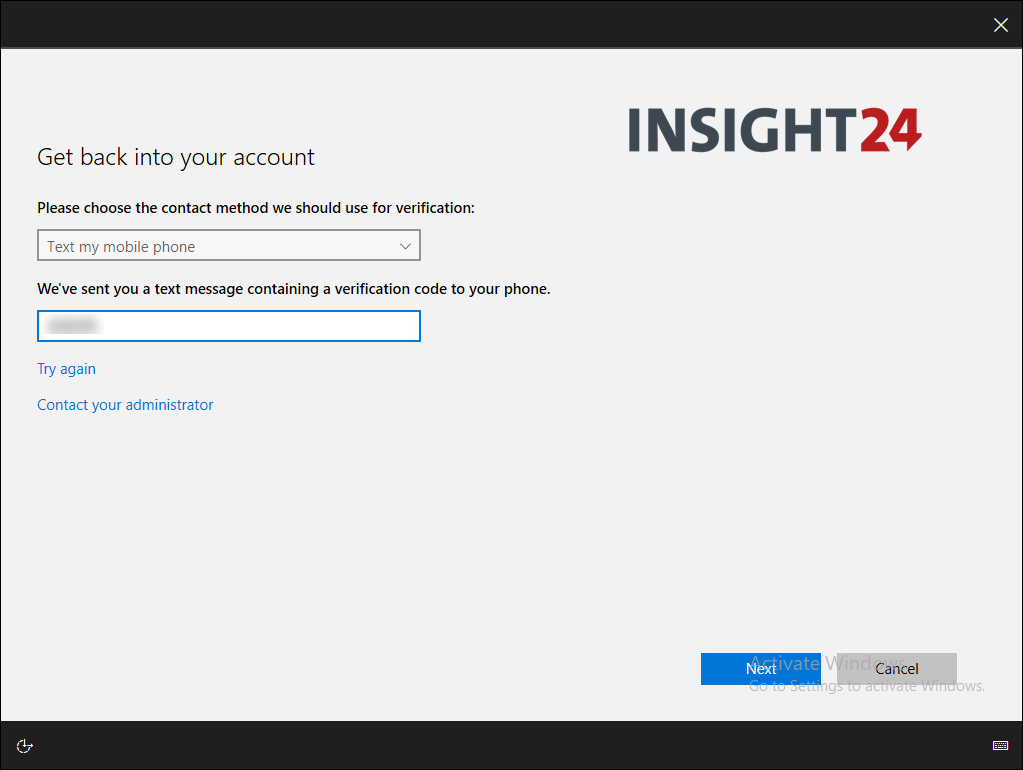
When an end user who has no authentication methods defined, or hasn’t registered for SSPR yet logs on, he/she will be provided with a “More information required” notice. When the user clicks Next they are redirected to the Security info registration page, where they can either provide or validate their authentication methods.
How can user change its password?
The user can change its password in several ways. The methods are:
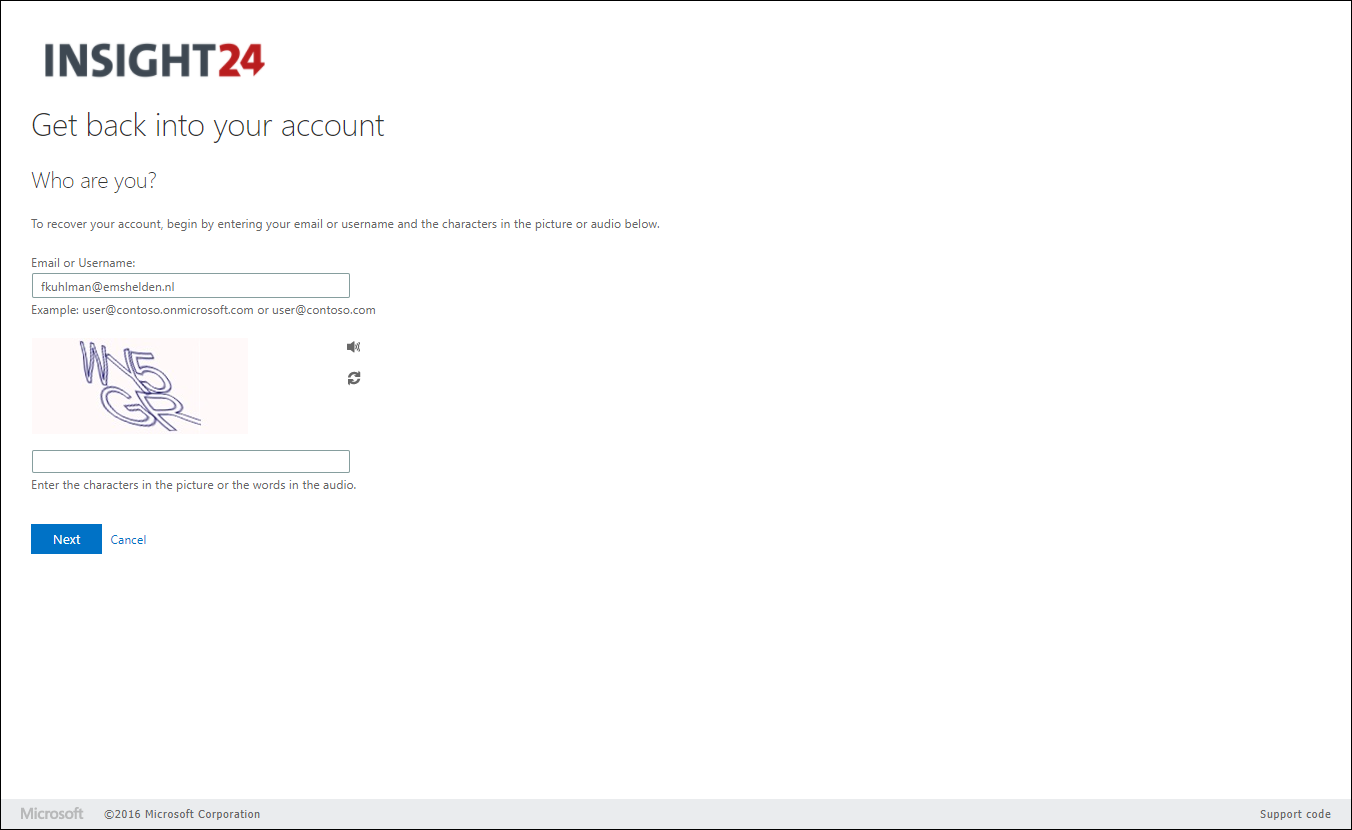
- By using the Forgot my password link on the sign-in page
- By clicking on the reset password link on the Windows 10 login screen
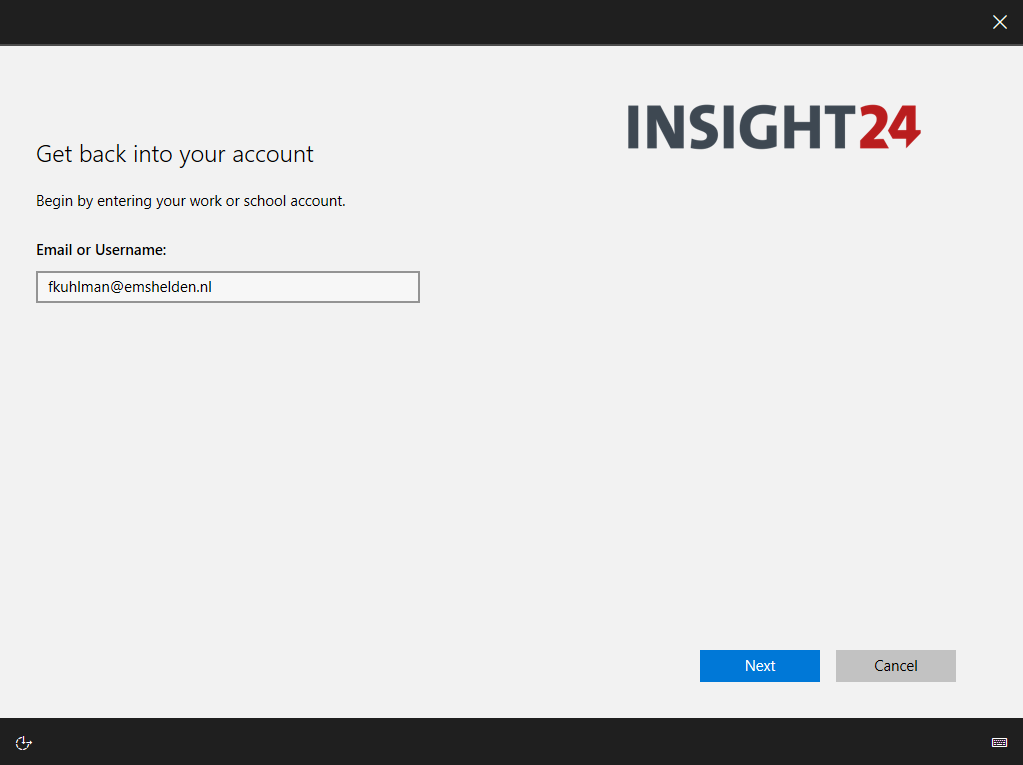
- By browsing to the Self Service Password Reset page using either https://aka.ms/sspr or https://passwordreset.microsoftonline.com/
Forgot my password on the sign-in page
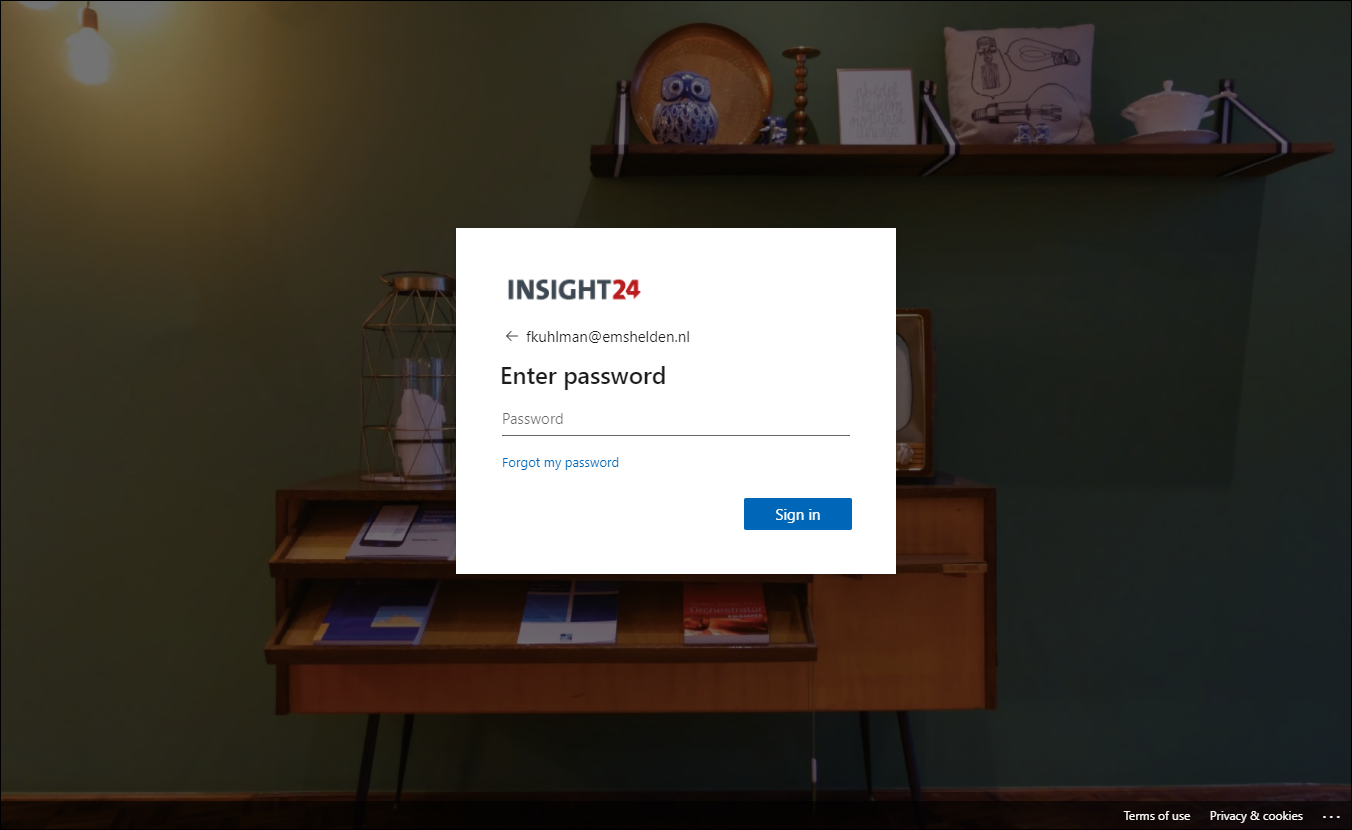
If a user signs-in to Azure AD, the user can use the “Forgot my password” link on the Enter password page when signing in to the web.
What about Admins?
Admin accounts are enabled for SSPR by default, also they have to use 2 authentication methods to be able to reset their password. So, the policy for administrators can be different from the one defined for your end users. Administrators cannot use the security questions as an authentication factor.
The policy applies when 30 days have elapsed in a trial subscription, a custom domain has been configured for the Azure AD tenant and when Azure AD connect is in use to sync identities from on on-premises Active Directory.
The following administrative roles are considered admin accounts:
- Helpdesk administrator
- Service support administrator
- Billing administrator
- Partner Tier1 Support
- Partner Tier2 Support
- Exchange administrator
- Skype for Business administrator
- User administrator
- Directory writers
- Global administrator or company administrator
- SharePoint administrator
- Compliance administrator
- Application administrator
- Security administrator
- Privileged role administrator
- Intune administrator
- Application proxy service administrator
- Dynamics 365 administrator
- Power BI service administrator
- Authentication administrator
- Privileged Authentication administrator
You can disable the use of SSPR for administrator accounts using the Set-MsolCompanySettings PowerShell cmdlet. The -SelfServePasswordResetEnabled $False parameter disables SSPR for administrators.
If an admin resets its password, other admins will be notified as well.
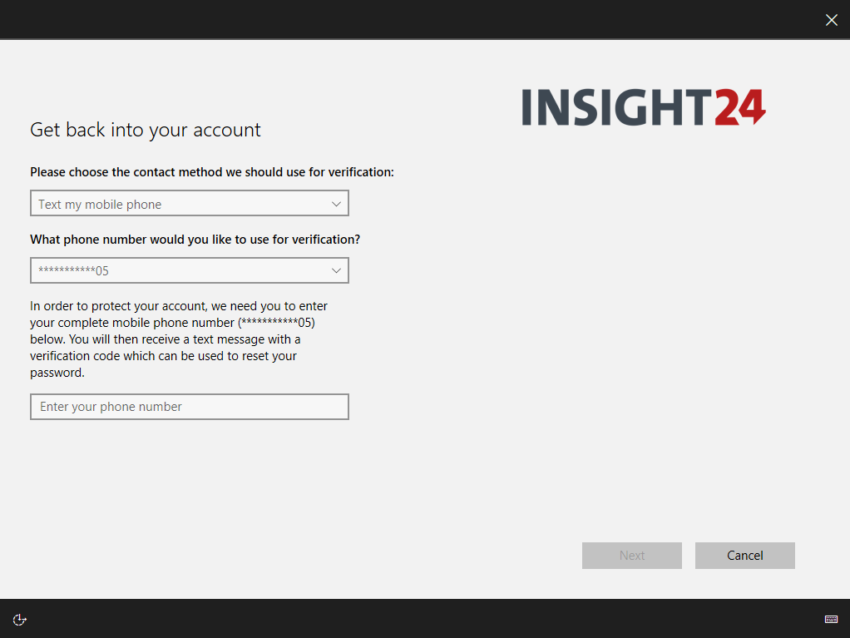
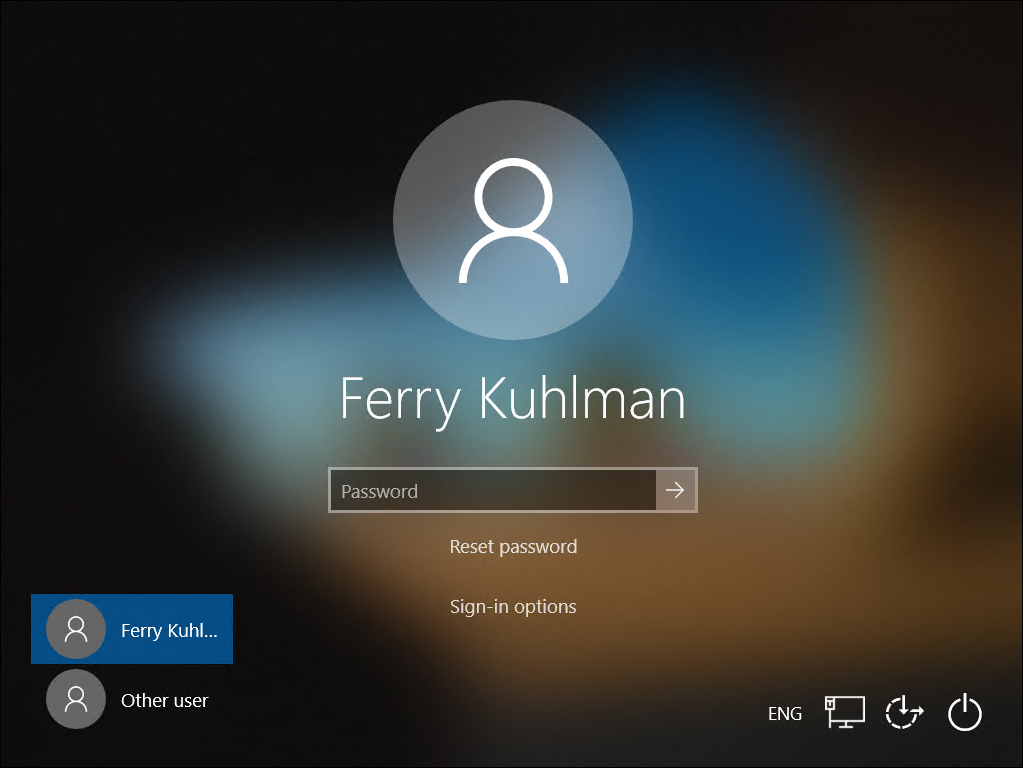
Clicking on the reset password link on the Windows 10 login screen
You can enable a “Reset password” link at the password login screen of a Windows 10 device. Microsoft explains how to enable this functionality via a custom OMA-URI configuration policy setting the ./Vendor/MSFT/Policy/Config/Authentication/AllowAadPasswordReset with a value of 1. More about setting up this functionality in this article: Enable Azure Active Directory self-service password reset at the Windows sign-in screen
Conclusion
Enabling Self Service Password Reset (SSPR) is a welcome addition for your Microsoft Modern Workplace. It’s easy to setup, customizable to your needs and even not too complex to setup if you synchronize your identities using Azure AD Connect. My suggestion would be to enable this in your tenant and explain your users how to leverage its functionality.
For the rollout, Microsoft provides all kind of material which can help you bring the message to your end users, you can find that here: Self-service password reset rollout materials
never stated what roles or permissions are required to setup SSPR in azure. Is Global Administrator required or is there a granular permissions subset that can accomplish the task of setup and or troubleshooting?