In January, Microsoft announced that they released a public preview allowing entitled customers to create Azure AD access reviews for guest users across all Microsoft Teams and Microsoft 365 Groups in the organization.
By implementing Access Reviews, an identity governance feature you can review members of groups, enterprise applications and roles within your Azure Active Directory. Access Reviews requires Azure AD Premium P2 licenses for users who benefit from the functionality, see: How many licenses must you have?
Some scenario’s in which you might want to use Access Reviews are:
- Validate membership of Azure AD privileged roles on a regular basis
- Validate access to Applications on a regular basis
- Review members of policy exception groups, for example users excluded for a particular Conditional Access policy
- And now also, owners of a Teams or Microsoft 365 group can review the guest memberships on a regular basis
Access Reviews for Azure AD privileged roles have been described in my article about Azure AD Privileged Identity Management (PIM), which can be found here: Lessons learned while implementing Azure AD Privileged Identity Management (PIM)
The need for Governance of Guest users
From a governance perspective, having external guest users in your Azure AD environment is a challenge. As you might know Guest users can be created in your Azure Active Directory when:
- A user in your Azure AD shares a specific document with an external user
- A user in your Azure AD invites an external user to become member of a Microsoft Teams or SharePoint site
- There might also be some other scenarios….
Fact is, that once a Guest user account has been created, it can stay in your Azure AD for ever and ever. This is a challenging security risk, since those Guest users have access to your company data. Might the account of the Guest user been compromised, then the person in possession of the compromised Guest account also has access to your company data. It’s possible to require Guest user to also require a second factor authentication though, which is a good first security measure you can take.
What you want to do though, is have some process in place where users sharing data with External Users can easily review this access once in a while and have a way to remove the access to external users if that access is not needed anymore.
Some of these challenges can be solved with the Access Review for Guest users functionality, let’s have a look.
Access Reviews for guests in all Teams and Microsoft 365 Groups
You can create an access review from the Identity Governance blade in the Azure AD administration portal.
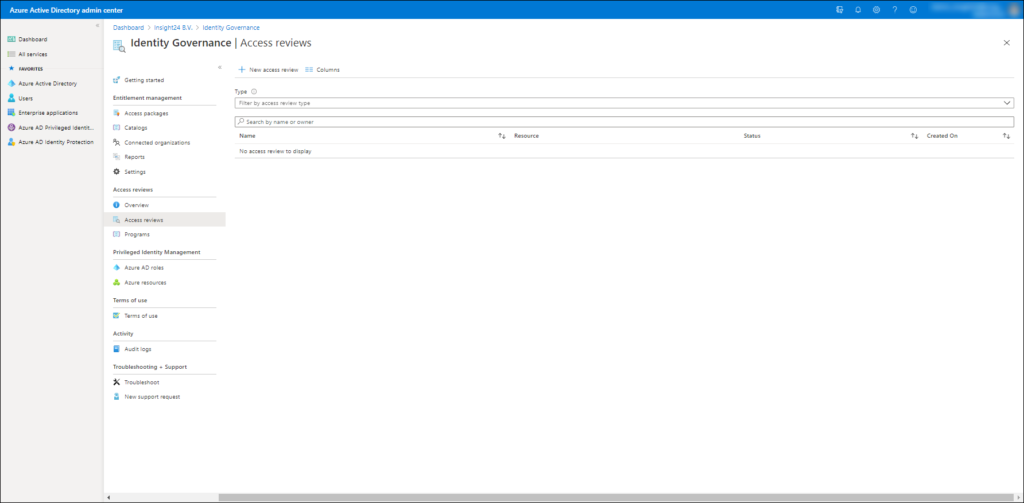
If you click on “+ New access review”, the new access reviews creation experience will open. From this page you can either select to create an access review for a Microsoft Teams or Microsoft Groups or you can create one for an Application.
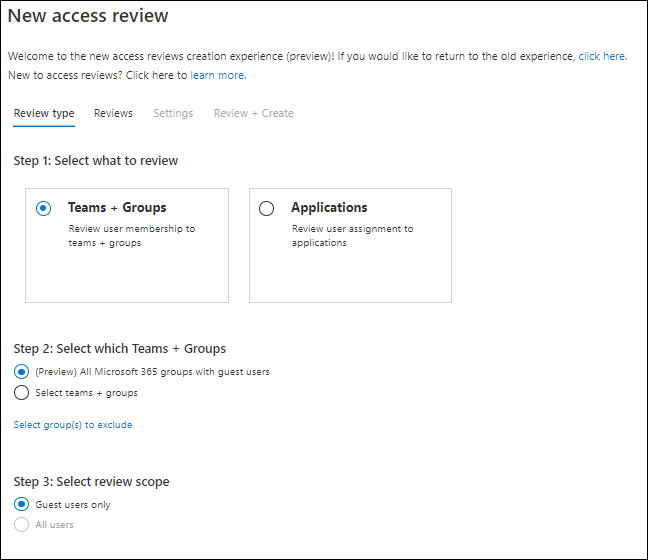
Once Teams + Groups is selected, you can choose whether you want to include all Microsoft 365 groups with guest users, or if you want to select your Teams and Groups for which the access review is applicable. If you select “(Preview) All Microsoft 365 groups with guest users” you can only have Guest users in your scope. If you select an individual group you can also select “All users”. You can continue with the configuration by clicking on the “Next: Reviews” button, which will bring you to the review tab.
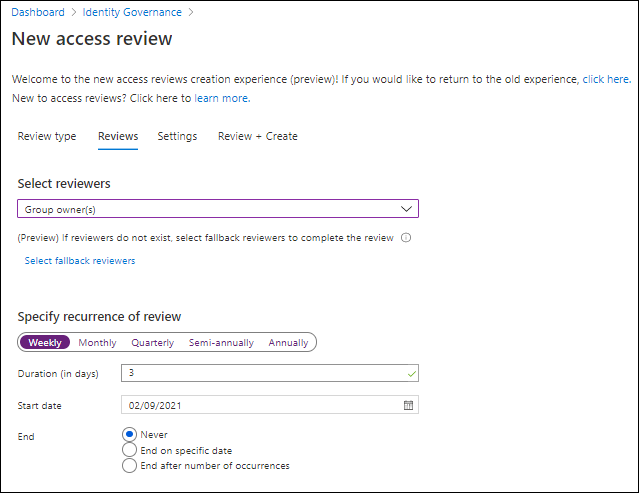
On the review tab you can select the reviewers for this access review. This can either be:
- Group owner(s)
- Selected user(s) or group(s)
- Users review own access
- (Preview) Managers of users
You can also define the schedule, which can either be weekly, monthly, quarterly, semi-annually or annually. The duration of the review in days, the start date and when the access review should end. Once finished you can continue to the settings tab by clicking on “Next: Settings”
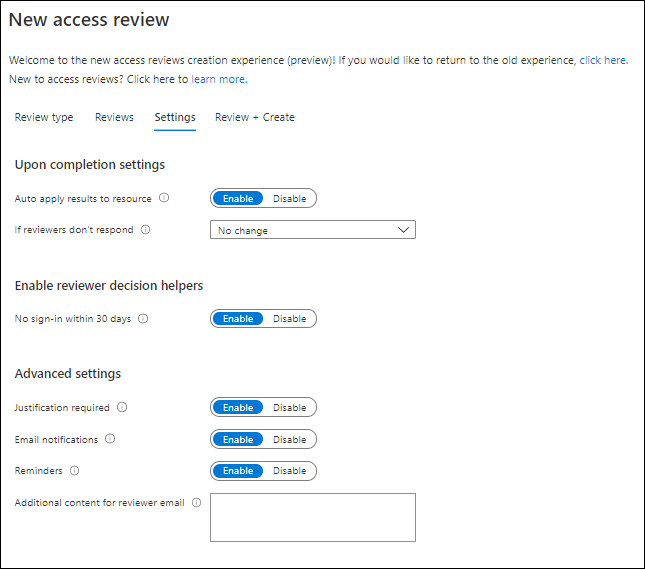
On the settings tab you can configure the following settings:
Upon completion settings, where you can define what must be done with the results of the access review. So for example if the reviewer specifies that the access for the guest user is not needed anymore, the access is removed. If you disable this setting you’ll see that the access is not necessary anymore in the access review reporting. You can also specify what happens if the reviewer doesn’t respond, by default “No change” is selected, but you can also select; Remove access, Approve access and Take recommendations.
You also have the option to enable reviewer decision helpers, which will notify the decision maker if the account being reviewed hasn’t signed-in within the last 30 days. (too bad you adjust this value)
Last but not least, you can configure some advanced settings.
- Justification required, which requires the reviewer to supply a reason for approval
- Email notifications, which enables Azure AD to send emails to reviewers when an access review starts, and to admins when a review completes
- Reminders, where Azure AD will send reminder emails for Access Reviews in progress to all reviewers at the midpoint of the review period
- Additional content for reviewer email which will show some additional text in the email sent to reviewers. Best practices are to include context on why users are being asked to do this review and where they should go if they have questions.
Once finished you can continue to the Review and Create settings tab by clicking on “Next: Review + Create”
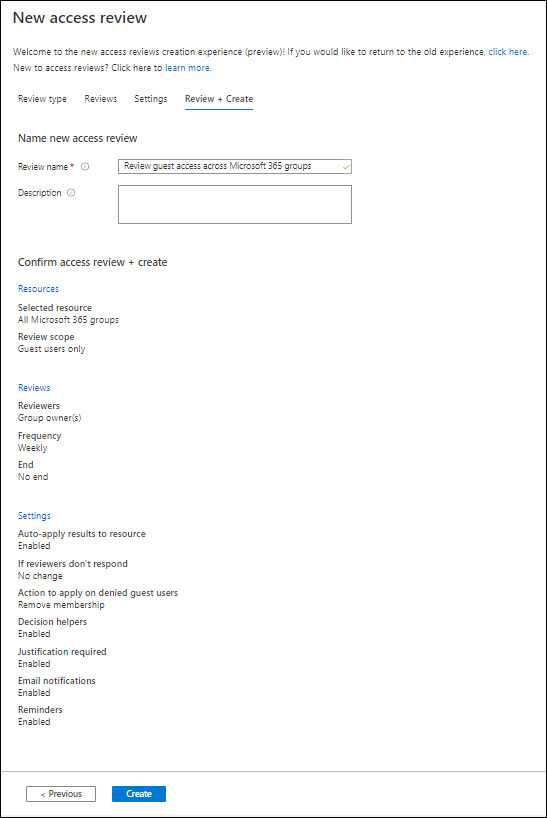
On the review and create tab you can review the settings you just set, and you can provide a name and description for the Access Review for later identification. If you are satisfied with the settings you can click on Create to create the Access Review.
Reviewer Experience
Once the access review is active, the reviewer will get an email like the one below. The email is localized, that’s why it’s in Dutch.
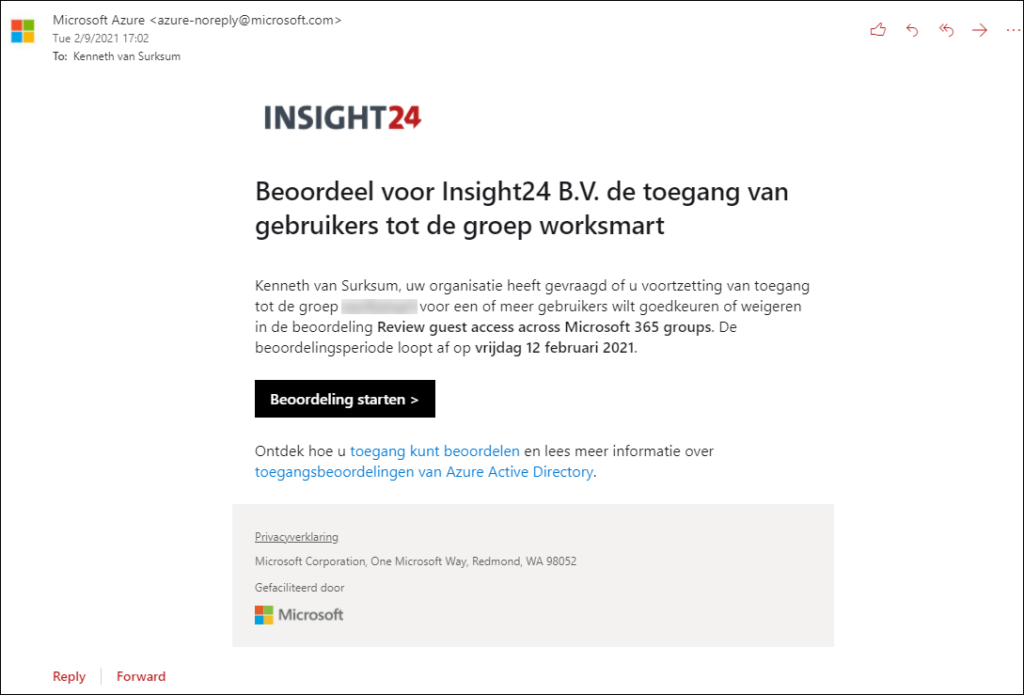
The reviewer can start the access review by clicking on the Start Review button, which will open a Web browser to the My Access panel.
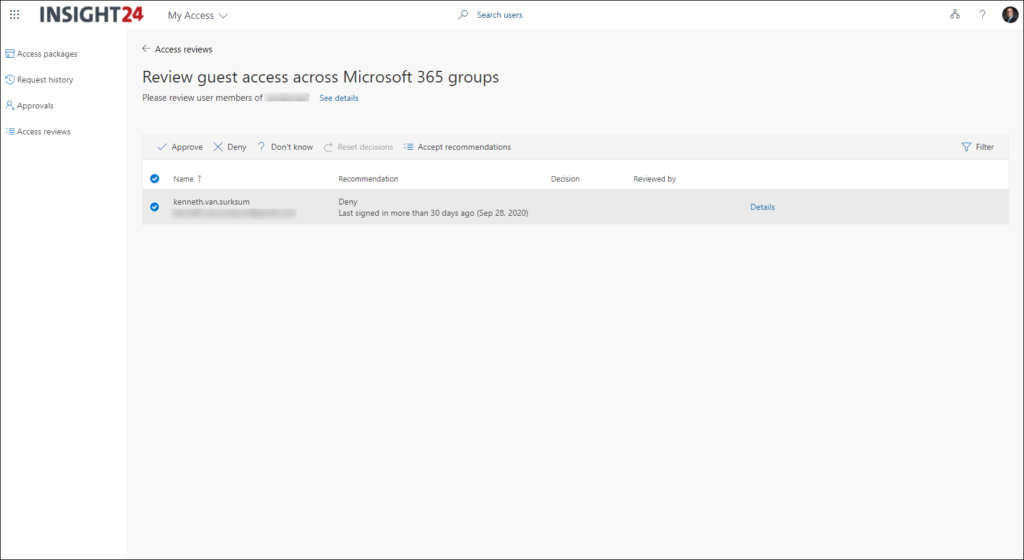
From here the review can see which Guest user has access to the Microsoft 365 group, notice that there is a recommendation to deny access, because the user hasn’t signed-in in the last 30 days.
From the overview the reviewer can select the Guest user account, and select either Approve, Deny, Don’t know or Accept recommendations. For each choice made you have to provide a reason, as specified in the properties of the access review earlier.
The reviewer can change its decision for as long as the access review is running
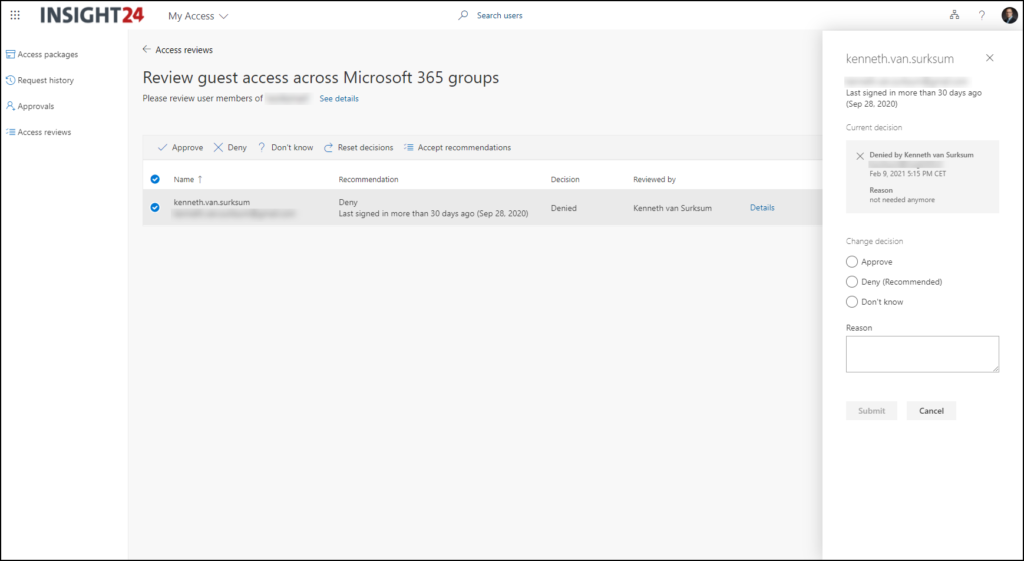
For each group you can view the status of the access review from the Azure AD management portal
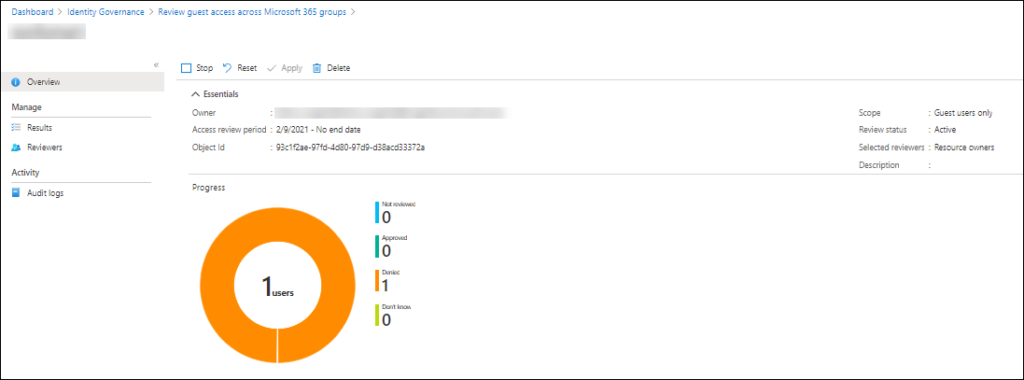
Once the access review is finished, or you an admin stops the access review the denied guest account is automatically removed from the M365 Group.
Conclusion
Access Reviews for guests in all Teams and Microsoft 365 Groups is a welcome addition to the Access Reviews functionality. The big advantage is that newly created Microsoft Teams and/or Microsoft 365 groups fall under the regime of the access review and therefore maintaining the solutions requires minimal effort.
Removing access from a Microsoft 365 group doesn’t remove the Guest account from Azure AD though, and it might be that individual documents are still shared with the Guest user. So you must still build something which can help you report on that.
Hi, This is really useful and I’m planning to implement this feature, but I’m not sure how to apply settings to get email if any changes happened to the assigned groups and weekly once review email. It would be really helpful if you could provide some suggestions on the same. Thanks!