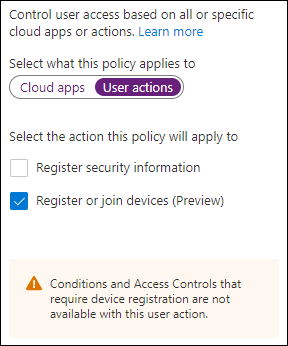
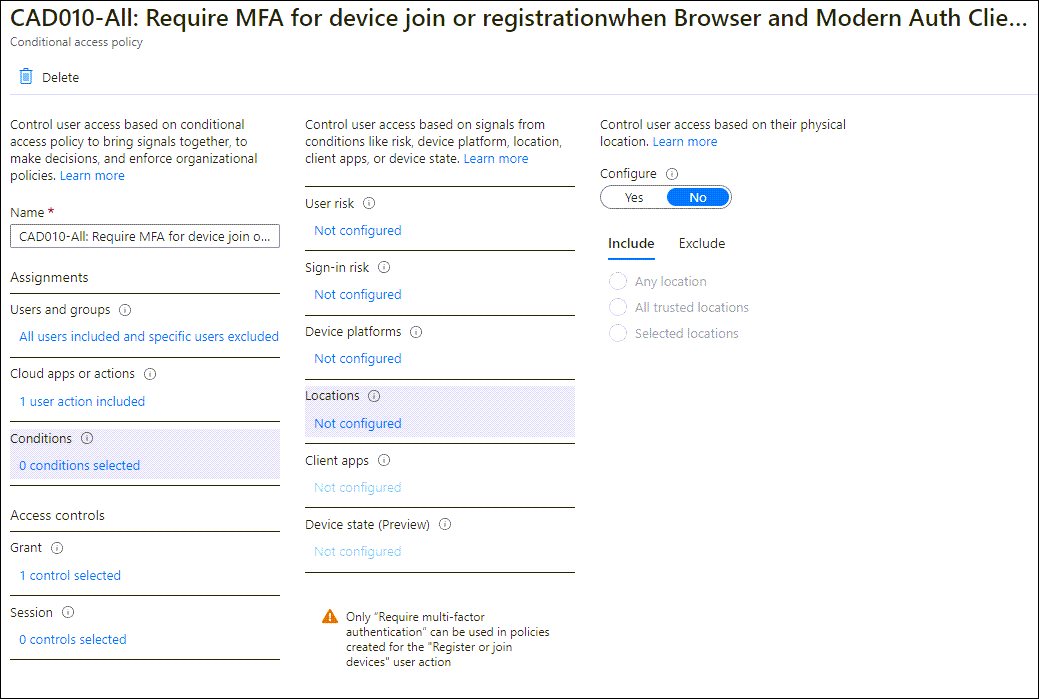
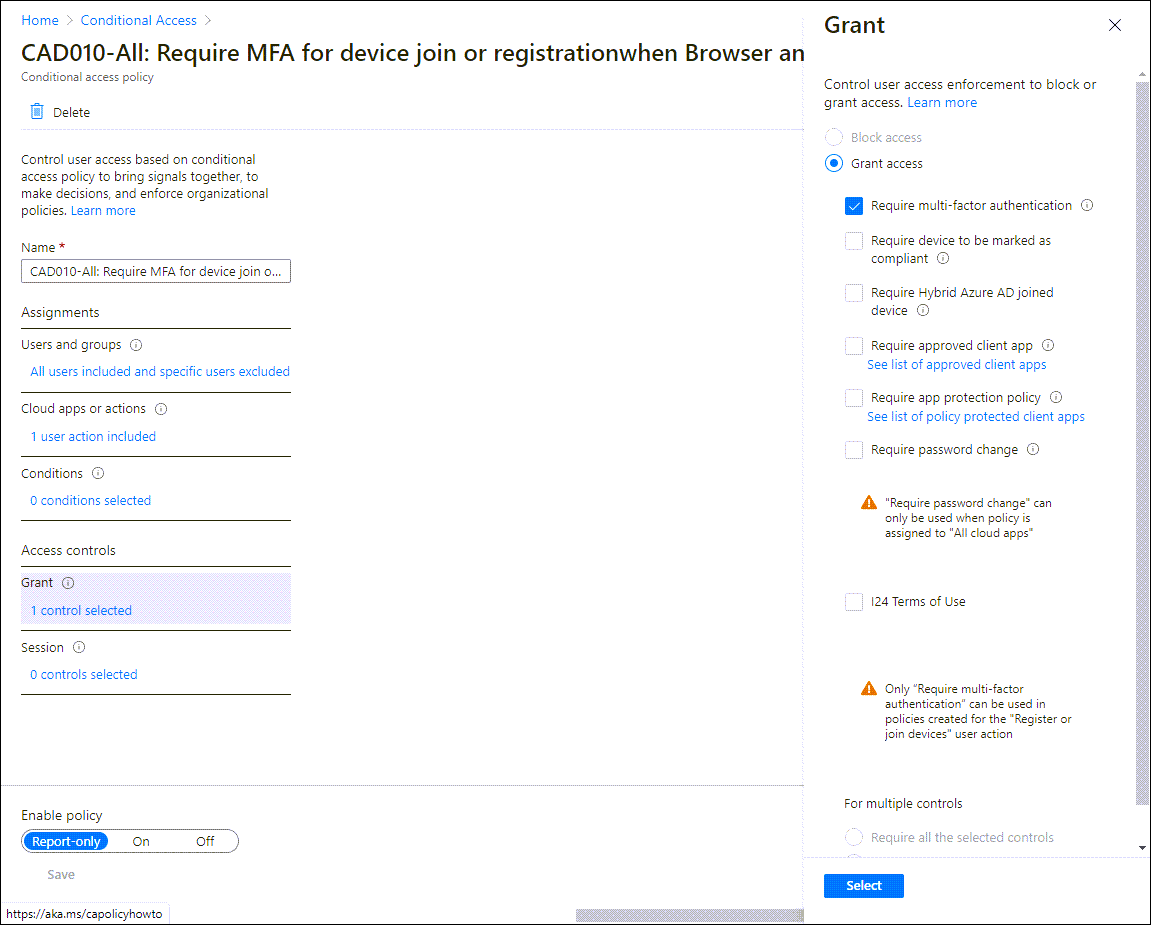
This month Microsoft released a new “User Action” for Conditional Access in public preview. The new user action called “Register or join devices” can now be used to provide more granularity related to joining or registering a device in Azure Active Directory.
Up until now, there was a global setting which you could define related to whether Multi Factor Authentication (MFA) was necessary to register or join a device to Azure Active Directory. This setting is found under Device Settings in Azure AD and now contains the following message: “We recommend that you require Multi-Factor Authentication to register or join devices using Conditional Access. Set this device setting to No if you require Multi-Factor Authentication using Conditional Access.”
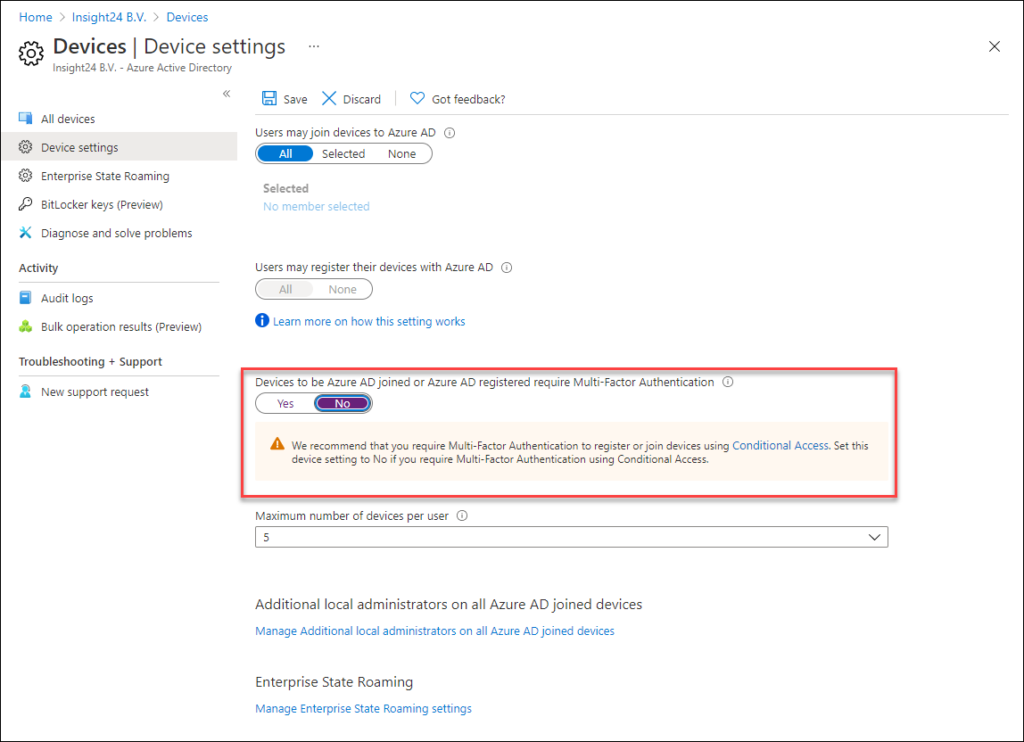
The disadvantage with this setting is though that its global and there are some circumstances where having this option enabled is causing us some challenges. These challenges are mainly related to the rollout of Android and iOS device enrollment scenario’s where the MFA challenge could not be completed because the device cannot receive calls or text messages during the provisioning process.
With the “register or join devices” user action we can build some new scenario’s – not all Conditional Access functionality is available (yet) though. You cannot use the Client apps and Device state conditions as part of the assignments for example, and you can only use the “Require multi-factor authentication” grant control.
Based on this you can build the following scenario’s:
- Only require MFA for device registration and join when device platform is Windows and macOS, or exclude iOS and Android
- Require MFA for device registration and join when performing this action from any location excluding trusted locations
- Require MFA for device registration and join when User risk or Sign-in risk is at a certain level
Excluding whole platforms is risky though, since the platform can easily be “mimicked”. A better option would be to temporarily exclude the users for which you know that they are going to perform a device enrollment from the policy.
Conclusion
Even though I understand the challenge that we can solve here with mobile device enrollment in certain scenarios, just excluding these platforms from MFA registration should be considered a “temporary” situation. So if you are going to use this new option, make sure that you govern who is excluded from the policy, and preferably let this be temporary. Another option could be to only allow enrollment of these devices from trusted locations. Not really an option today with the pandemic unfortunately, but perhaps in the future this will be a usable situation again. Strictly we want to allow initial MFA registration to take place from trusted locations as well.
References
Public preview – New “User action” in Conditional Access for registering or joining devices