Starting with Firefox version 91, Mozilla is now supporting Single sign-on support (SSO) and device-based Conditional Access as announced by Microsoft in the What’s new in Azure Active Directory for August 2021. The feature is still in Public Preview from a Microsoft point of view, and considered Advanced and experimental from a Mozilla point of view.
I’ve already written about Browser restrictions and configuration when using Conditional Access on your modern workplace where I explained how Google Chrome must be configured in order to work with your Conditional Access policy, and now Mozilla Firefox can be added to the list of browsers.
Configuring Firefox to support SSO for Microsoft, Work and School Accounts
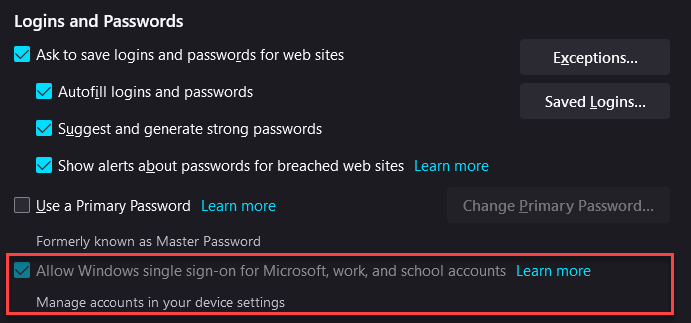
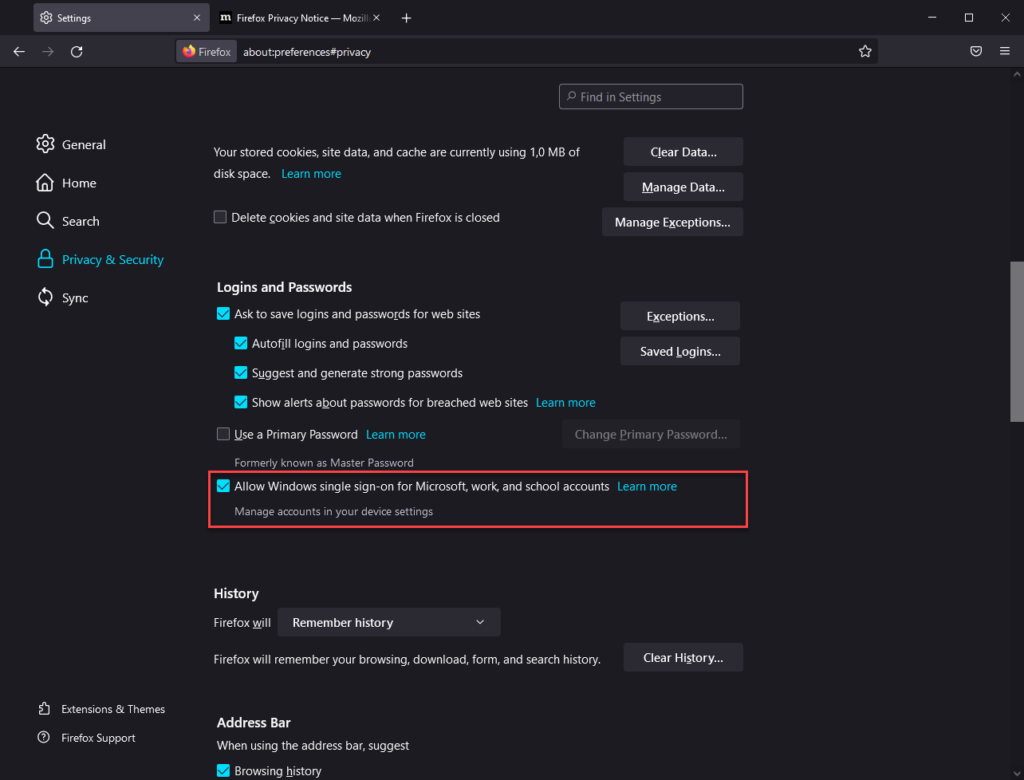
For now the option must be enabled, this can be done by opening Firefox, going to the menu and by selecting settings, from there you can go to Privacy & Security and go to the Logins and Passwords section. From there you can enable the feature by selecting the checkbox in front of “Allow Windows single sign-on for Microsoft, work and school accounts”.
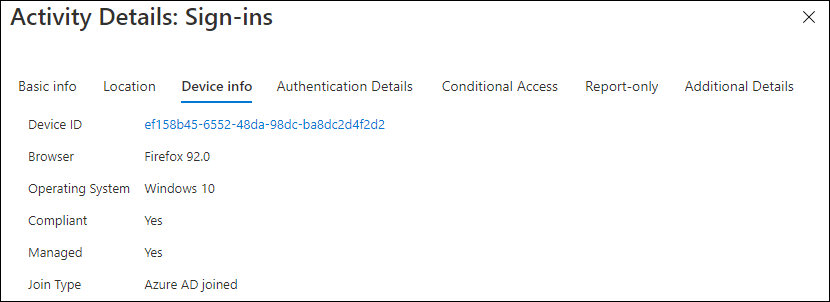
Within Azure AD sign-in logging we can now see that compliant and managed options are set to yes.
Configuring the settings from Microsoft Endpoint Manager
Since Mozilla is also providing ADMX files for configuring it’s browser, we can use this functionality to configure the “Allow Windows single sign-on for Microsoft, work and school accounts” setting using a custom Configuration Profile.
I will not go into too much detail on how you can use a custom ADMX file and leverage its settings in a Microsoft Endpoint Manager configuration profile. If you want to know more about that, I suggest that you read the following article from fellow-MVP Peter Klapwijk: Manage new ADMX Backed Windows 10 policies with Microsoft Intune and the Microsoft documentation “Win32 and Desktop Bridge app ADMX policy Ingestion“
You can download the latest ADMX file for FireFox from the Mozilla Github page. Mozilla even has a Knowledge base article explaining how to ingest and set settings which you can find here: “Managing Firefox with Microsoft Endpoint Manager (Intune)“. The OMA0URI configuration string and possible values can be found under the WindowsSSO section of the Readme.md file.
Based on the information provided above we can create our custom configuration profile in Microsoft Endpoint Manager.
Create the custom Device Configuration Profile
Name: W10 – CP – Mozilla Firefox Configuration – v1.0 (or any other name you want to provide)
Profile type: Custom
OMA-URI settings:
| Name | FireFox ADMX Ingestion |
| Description | FireFox ADMX Ingestion |
| OMA-URI | ./Device/Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/Firefox/Policy/FirefoxAdmx |
| Value (String) | Copy the content of the firefox.admx file into the Value field |
| Name | Enable Windows SSO |
| Description | Enable Windows SSO |
| OMA-URI | ./Device/Vendor/MSFT/Policy/Config/Firefox~Policy~firefox/WindowsSSO |
| Value (String) | <enabled/> <data id=”WindowsSSO” value=”1″/> |
After the Configuration profile is successfully applied, you will notice that in FireFox the option is grayed-out meaning that it cannot be changed by the user.
Conclusion
On a modern workplace users like to have options, and having support for the Mozilla Firefox browser within you Conditional Access framework is a good thing. So let’s hope the feature comes out public preview soon so that we can also support the FireFox browser as well.
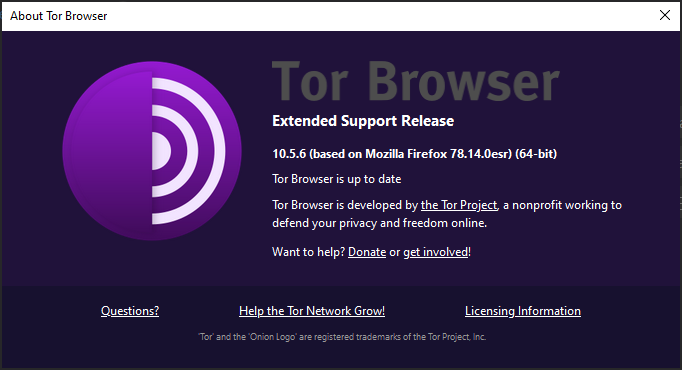
I did a quick check on whether the Tor Browser was also supporting the functionality, but as you can see that browser is still based on Mozilla Firefox 78.14.0esr. It will most probably be a matter of time before the TOR browser supports this functionality as well, and it will be interesting to see how we can handle that.
References:
https://support.mozilla.org/en-US/kb/windows-sso
https://docs.microsoft.com/en-us/windows/client-management/mdm/understanding-admx-backed-policies
https://www.inthecloud247.com/manage-new-admx-backed-windows-10-policies-with-microsoft-intune/
https://github.com/mozilla/policy-templates/releases
https://github.com/mozilla/policy-templates/releases
https://github.com/mozilla/policy-templates/blob/master/README.md#windowssso
https://support.mozilla.org/en-US/kb/managing-firefox-intune
I tried this and got remediation failed.
Looking on Firefox policy template page, the string should just be or
No data ID element required
Indeed, I did see that on the Firefox documentation page, but that didn’t work – hence my article with a working solution
Are you experiencing any issues?
/Kenneth
That’s strange then coz mine didn’t work with the data ID and value of 1 in the string, but did work with the string just enabled!
Hey Tim,
That is strange indeed. Give me some time to see if I can reproduce this issue in other tenants.
If anyone else reading this article experiences the same issue, please let me know.
/Kenneth
Hey there!
Same issue… the configuration looks fine to me as it is basically just what’s in the FireFox documentation, but I always get the same “Remediation failed”-error (0x87d1fde8).
This happens regardless of the data id value is set or if I just set the string to “”.
Cheers!
Hi Achim,
Did you use both the settings from my article, and the setting that TIM is referring to (as stated on the Mozilla documenation page: https://github.com/mozilla/policy-templates/blob/master/README.md#windowssso)
Very strange that we get different results, I implemented my solution in several tenants without any issues .