In December last year, Microsoft announced that per April 1, 2021 they updated their service level agreement(SLA) for Azure AD user authentication from 99.9% to 99,99%. While this might seem like a small update in reality it makes a difference of 473 minutes (in a year with 365 days).
With 99.9% the allowed downtime was 525 minutes and with 99.99% this is reduced to 52 minutes. This is still inconvenient though if you experience downtime for let’s say 45 minutes on Monday morning while everyone is starting their work.
One of the techniques that Microsoft rolled out in order to support the new uptime, was the Azure AD Backup Authentication service, which Microsoft describes as the following:
Azure AD Backup Authentication service runs with decorrelated failure modes from the primary Azure AD system. This backup service transparently and automatically handles authentications for participating workloads as an additional layer of resilience on top of the multiple levels of redundancy in Azure AD. You can think of this as a backup generator or uninterrupted power supply (UPS) designed to provide additional fault tolerance while staying completely transparent and automatic to you.
So, what the Azure AD backup authentication service basically does is issuing tokens to applications for existing sessions if there is an outage of the primary authentication service. New sessions, or authentications by guest users are not supported.
Which brings us to Azure AD Conditional Access, since access tokens are re-evaluated by Conditional Access policies before issued. But when the Backup authentication service is used, not all conditions can be evaluated in real time.
Want to know more about Conditional Access, then download my whitepaper on the subject for which the latest version can be found here:
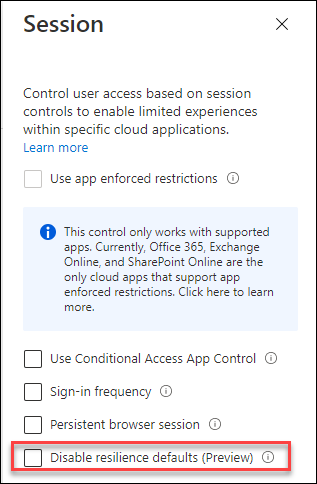
New Conditional Access session control
By introducing a new session control in Conditional Access, called “Disable resilience defaults” it’s now possible to let the policy block authentications in the case that the backup authentication service is active. By default this option is turned off, which means that “in this case” when conditions cannot be evaluated in real time or evaluated with data collected at the beginning of the user’s session that the authentication will not be blocked.
The following conditions cannot be reevaluated during an outage:
- Group Membership
- Role Membership
- Sign-in risk
- User risk
- Country location
That means that all other conditions, like MFA can be evaluated and those policies will not be impacted by this session. If you want to block based on Sign-in/User risk and don’t want to make concessions even during an outage, then this option is for you.
Conclusion
Microsoft recommends to keep the resilience defaults enabled, in order to mitigate the impact of an outage. But in case you have a high secure environment you might want to consider to use this new session control option to control the behavior during an outage.
Testing the options will be a challenge though 🙂 Which might be a reason to leave the options as-is, in my opinion.