Microsoft has extended the capabilities of Azure AD authentication context to Azure AD Privileged Identity Management (PIM). By doing this we can trigger a Conditional Access policy to be executed at the moment someone elevates their role using Azure AD PIM. This functionality is now in preview.
In June 2021 I already provided a first look at Azure AD Conditional Access authentication context, please read this article first if you want to know more about this functionality.
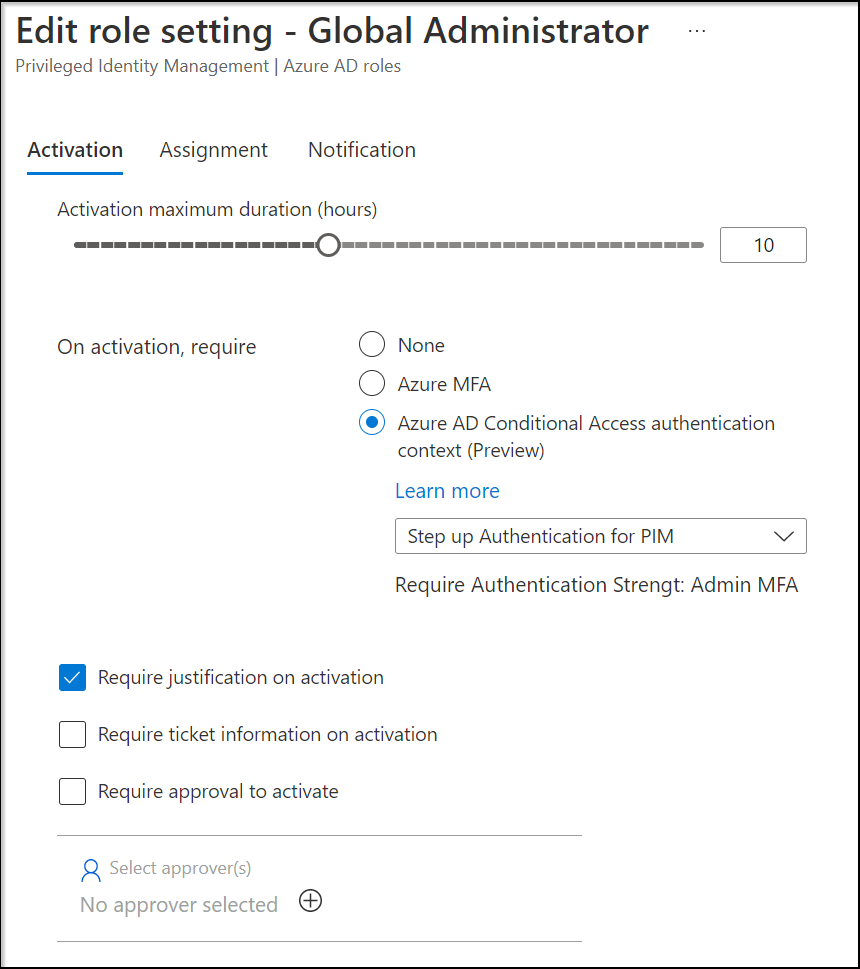
Up until now, we had the option to require MFA for elevation of a Azure AD when defined in PIM, and this has now been extended to modify this to “Azure AD Conditional Access authentication context”
In the example below, we modified the Global Administrator role so that the “Step up Authentication for PIM” authentication context is selected when elevating for this role.
Once this setting has been modified, we can create a Conditional Access policy which requires Step Up MFA using Authentication Strength for example. See the following article for more information about Authentication Strength.
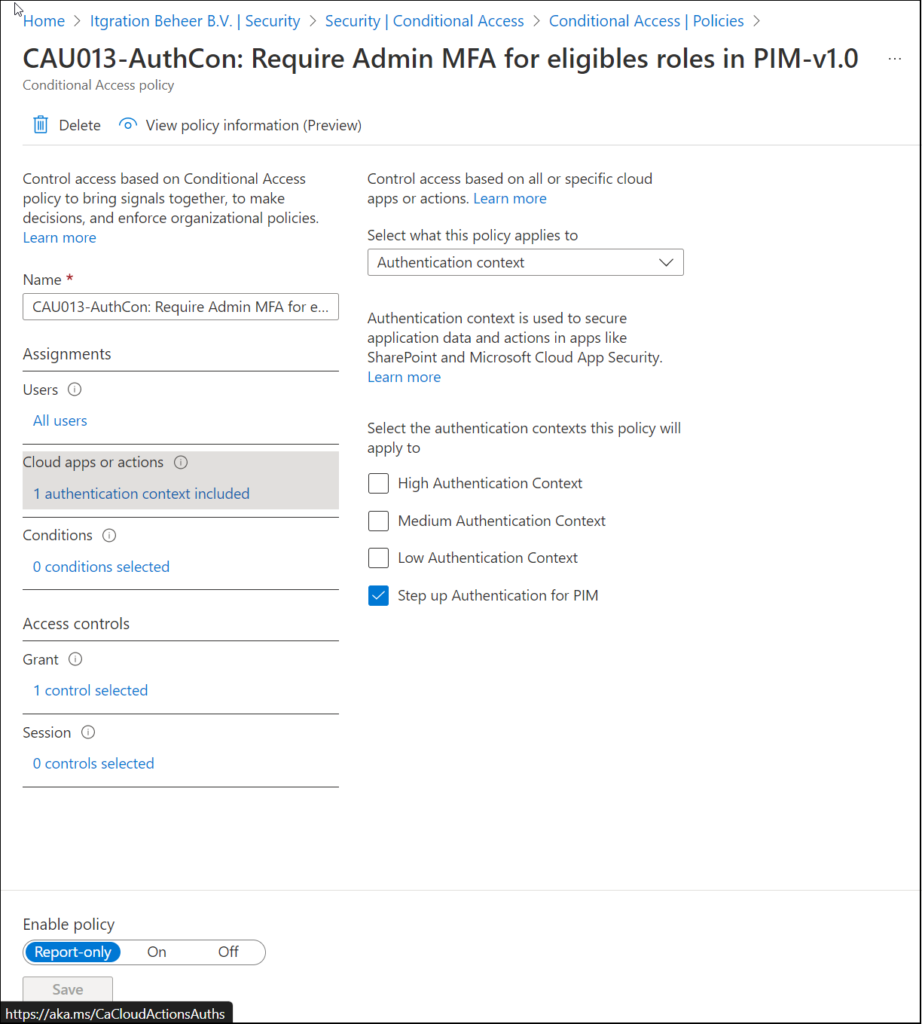
So, let’s create a new Conditional Access policy which gets triggered when the Authentication Context is hit.
The first thing we have to do is to target the Conditional Access policy to “Authentication Context”, and select the “Step up Authentication for PIM”
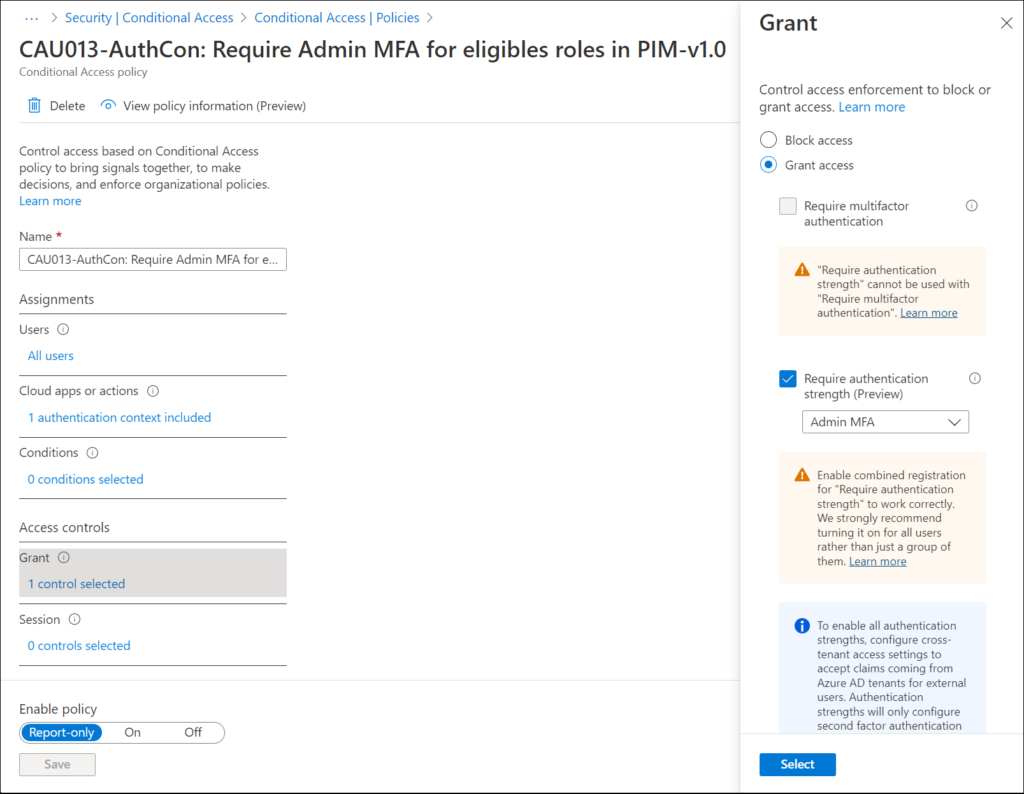
Next we can select the Grant controls which are required to give access, in this example we require the “Admin MFA” authentication strength
Conclusion
Adding authentication context to Azure AD Priviliged Identity Management (PIM) is a welcome addition to further leverage the flexibility of Authentication Context.
In the example of this blogpost we used the Step up MFA as an example, but we can also use other Grant controls, like for example only allow elevation on a Compliant or Hybrid Azure AD joined Device.

1 thought on “Azure AD Conditional Access authentication context now also available for Azure AD Privileged Identity Management”