In March 2021, I published the blogpost “Configuring Windows Update for Business settings for your Microsoft Endpoint Manager managed Modern Workplace“, in that blogpost I described the Windows Update for Business (WUfB) configuration I used, based on the best practices defined by Microsoft defined in their paper titled: “Optimizing Windows 10 Update Adoption“, which is part of the Windows 10 Update Baseline.
For context it might be interesting to read the article below first
In the blogpost I detailed the following configuration:
- Windows 10 Update Rings
- Power Settings
- Modifications to the MDM Security Baseline
- Delivery Optimization
All of the components are still necessary to configure, but in the last 2 1/2 years some modifications have been made by me, based on customer feedback and new functionality and insights. The goal of this blogpost is to give an up to date “best practice” on how to configure Windows Update for Business in your Modern Managed environment using Microsoft Intune.
The Windows Update for Business team also posted some interesting blog articles in the meantime which I advise you to read as well:
Why you shouldn’t set these 25 Windows policies – Windows IT Pro Blog (microsoft.com)
The Windows Update policies you should set and why – Microsoft Community Hub
Windows monthly updates explained – Microsoft Community Hub
I further highly recommend to follow Aria Carley (ariaupdated (@ariaupdated) / X (twitter.com) on Twitter/X since she regularly shares best practices and gives updates on the topic of Windows Update for Business as well. B.t.w did you know that Windows Update for Business will be renamed to Windows Autopatch.
Based on experiences implementing my initial settings at a diverse set of customers in the past 2 1/2 year, some modifications have been made to my initial recommendations, therefore this blog article.
In this blogpost I will cover the following topics:
- Update Rings for Windows 10 and later
- Tweaking end user notifications
- Power Settings
- Security Baseline modifications
- Delivery Optimization, including necessary Firewall settings
- Restartable Apps
- Allow Windows updates to install before initial user sign-in
- Windows Autopatch
- Windows Update for Business Reporting
- Windows 11 Enterprise Feature Control
- Driver Updates
- Sharing is caring
- Summary
Update rings for Windows 10 and later
The following settings have changed:
- Automatic Update Behavior has changed from value “Auto install and reboot with end-user control” to value “Reset to default”
The old setting “Auto install and reboot with end-user control” is described as follows: Updates download automatically and then install during Automatic Maintenance when the device isn’t in use or running on battery power. When restart is required, the device restarts when not being used. This option sets the end-users control pane to read-only.
The new setting “reset to default” is described as follows: Windows will automatically determine active hours for the device. Using the active hours, Windows then schedules the best time to install updates and restart the system after updates install.
- Feature update deferral period (days) has changed from value “14” to value “0”
The reason for this change, is because we can now control Feature Update rollout by using the “Feature updates for Windows 10 and later” functionality. If we would keep a value in the “Feature update deferral period (days)” this would “add” to the settings in the “Feature updates for Windows 10 and later” policy. Therefore it’s recommended to set it to value 0 in this policy and control the values in the other policy.
For different deployment rings, we have some settings which are different based on the deployment ring. See table below:
| Setting | Update Ring 1 | Update Ring 2 | Update Ring 3 |
| Quality update deferral period (days) | 0 | 3 | 7 |
| Feature update deferral period (days) | 0 | 0 | 0 |
| Deadline for feature updates | 7 | 7 | 7 |
| Deadline for quality updates | 3 | 3 | 3 |
| Grace period | 2 | 2 | 2 |
The Deadline for feature updates specifies the number of days a user has before feature updates are installed on their devices automatically. The Deadline for quality updates the number of days a user has before quality updates are installed on their devices automatically. The Grace period specifies a minimum number of days after deadline until restarts occur automatically.
So for Update Ring 2, when Microsoft releases their Quality update (patch Tuesday), 3 days after that day the update will be made available for the clients in that update ring. If will then be installed within 3 days and once installed the user has 2 days time to reboot before that reboot is enforced.
Tweaking end user notifications
In order to optimize the user experience, two settings catalog settings are used to accomplish the following:
- Auto Restart Notification Schedule: 240 Minutes
- Auto Restart Required Notification Dismissal: User Dismissal
The Auto Restart notification schedule setting is normally set to 15 minutes, by extending this to 240 minutes (4 hours) we make sure that the user is notified on time before the deadline is reached. By configuring the Notification Dismissal and set it to User Dismissal we make sure that the user sees the notification. By default, the notification is automatically dismissed, so we risk that the user doesn’t see the notification if kept to the default setting.
Power Settings
Compared to the initial Power Settings we made the following modifications:
- Energy Saver Battery Threshold Plugged In, modified from 40 to 20
- Select Lid Close Action Plugged In, modified from “Sleep” to “Take no action”
The reason for these changes is related to the use of docking stations, where the user sometimes connects the laptop, uses the power button on the laptop and then closes the lid to continue working on an external screen only. With the old policy setting, the system would go to sleep which is frustrating for the end user. We also modified the Energy Saver setting to be 20% for devices connected to power, since the battery saver also influences OneDrive sync behavior among others. While the device is power connected and charging we can therefore tweak this setting to 20% instead of 40 (while on battery)
Security Baseline modifications
Just as with the old settings, we must make sure that we set the “Standby states when sleeping while on battery” or “Standby states when sleeping while plugged in” is set to Not configured in the security baseline. If the baseline receives an update, make sure to reconfigure these settings back to “Not configured” again, so that they don’t interfere with our intended settings.
Delivery Optimization
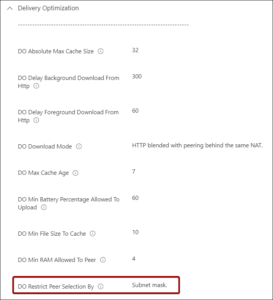
A new setting was added to be configured called “DO Restrict Peer Selection By” which basically makes sure that in a network with VLANs, the Delivery Optimization will only be done within the subnet.
Windows 11 introduced a new setting so that instead of Subnet Mask also ‘Local peer discovery (DNS-SD)” can be selected. This option restricts the discovery of local peers using the DNS-SD protocol.
If you want to learn more about Delivery Optimization, I suggest to read the following article: Skilling snack: Reduce bandwidth for Microsoft content delivery | Windows IT Pro Blog
Windows Firewall settings for Delivery Optimization
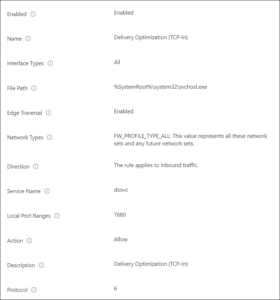
Delivery Optimization listens on port 7680 from other peers by using TCP/IP. If you don’t allow inbound traffic over port 7680, you can’t use the peer-to-peer functionality of Delivery Optimization. So we need to make sure that this port is opened on our devices.
How the firewall rules must be configured can be seen in the locally created firewall rules which are already available for Delivery Optimization, but usually don’t work in a managed environment where the rules must explicitly be defined.
See: Delivery Optimization Frequently Asked Questions – Windows Deployment | Microsoft Learn
Restartable Apps
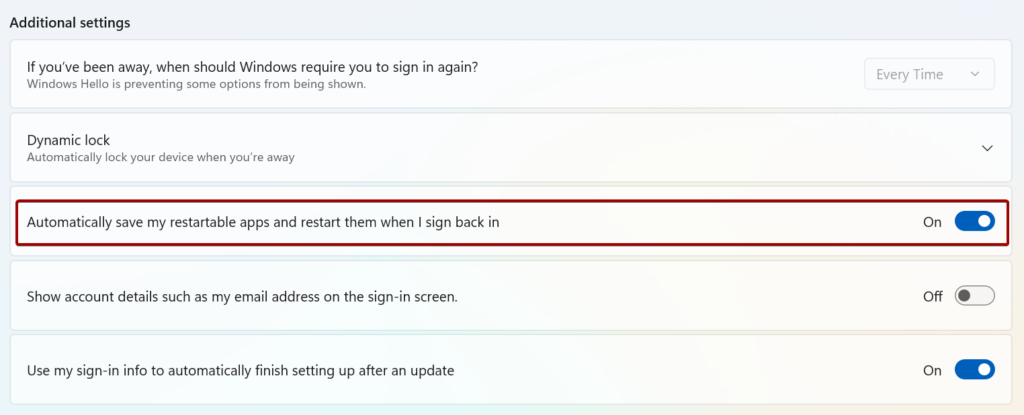
In windows there is a setting called “Automatically save my restartable apps and restart them when I sign back in”. Windows automatically saves your restartable apps when signing out, restarting, or shutting down Windows, and restarts them next time you sign in.
More details for application developers here: Registering for Application Restart – Win32 apps | Microsoft Learn
This setting is not available in the settings catalog unfortunately, so what we do in this case is deploy a script which sets the initial registry value to turn this functionality ON. Advantage of this method, is that users can turn the option OFF themselves if they don’t like the behavior.
# PowerShell Script to Set RestartApps Registry Value
# Registry Path
$registryPath = "HKCU:\Software\Microsoft\Windows NT\CurrentVersion\Winlogon"
# Registry Value Name
$registryValueName = "RestartApps"
# Registry Value
$registryValue = 1
# Check if the registry key exists
if (-not (Test-Path $registryPath)) {
# Create the registry key if it doesn't exist
New-Item -Path $registryPath -Force | Out-Null
}
# Set the registry value
Set-ItemProperty -Path $registryPath -Name $registryValueName -Value $registryValue
# Verify the registry value
$value = Get-ItemProperty -Path $registryPath -Name $registryValueName
Write-Host "Registry Value $($registryValueName): $($value.$registryValueName)"Allow Windows updates to install before initial user sign-in
In some scenarios, like for example Windows 365 user sign-in is deferred to a later point in time. Normally Windows Update doesn’t begin installing background updates until a user signs in for the first time, which is normally after completing the Out of the Box Experience (OOBE). For the scenario’s where the user sign-in is delayed, we can enable a registry key which allows devices to begin background update work before a user first signs in.
Registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Orchestrator
DWORD value name: ScanBeforeInitialLogonAllowed
Value data: 1Keep in mind that Microsoft recommends to only enable this functionality on devices where user sign-in is deferred. If enabled on devices where users sign-in immediately, the setting can have a negative effect on the user experience during initial sign in.
More information here: Manage additional Windows Update settings – Windows Deployment | Microsoft Learn
Windows Autopatch
Windows Autopatch is a cloud service that automates Windows, Microsoft 365 Apps for enterprise, Microsoft Edge, and Microsoft Teams update. Windows Autopatch is only available for companies using Enterprise functionality though, which disqualifies the solution for solutions needing to support Microsoft Business Premium licenses. (hence this article). Microsoft also announced that it will add driver and firmware management to the solutions as well.
There is really added value to using Windows Autopatch, since it automagically configured all the settings needed to update the supported apps, and uses clever mechanisms to determine what device to update when. Even while using Windows Autopatch though, some of the settings mentioned in this article could be useful.
See this article for more information about Windows Autopatch: What is Windows Autopatch? – Windows Deployment | Microsoft Learn
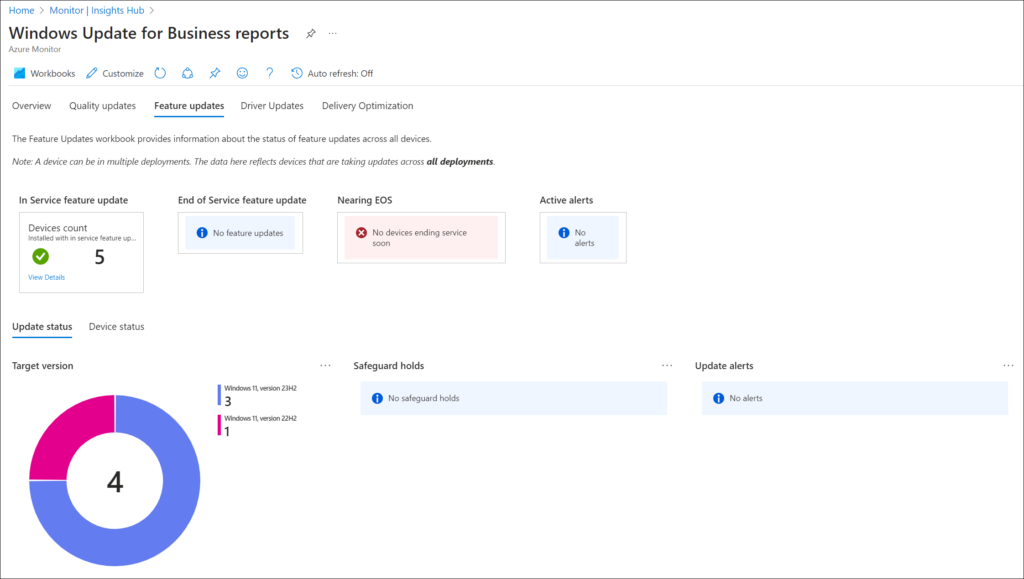
Windows Update for Business Reporting
Clients can upload Windows Update information to an Azure Log Analytics workspace. From there additional information about the Windows Update status of your devices can be found in the Windows Update for Business Reports.
The Report once configured gives details about Quality Updates, Feature Updates, Driver Updates and Delivery Optimization.
Configuring this functionality consists of 2 actions, first of all the Windows Update for Business reports functionality must be configured from the Insights Hub available in the Azure Monitor functionality, and secondly a Configuration Profile must be created and assigned to your users.
What needs to be configured is detailed in the following article: Enable Windows Update for Business reports – Windows Update for Business reports | Microsoft Learn
Windows 11 Enterprise Feature Control
Microsoft has changed the way that they deliver new functionality in the Windows 11 OS. For Windows 11 new features and enhancements are delivered through the monthly quality updates and could potentially already be enabled. Some of the functionality will be automatically enabled once the annual feature update gets installed (for example the 23H2 feature update for Windows 11), this is called an “enablement package”
There is a distinct between Temporary enterprise feature control and Permanent enterprise feature control. Features behind temporary enterprise control are automatically disabled for devices that have their Windows updates managed by policies, but can be enabled by using the “Allow Temporary Enterprise Feature Control” settings catalog option under the Windows Update for Business category.
Once the annual feature update is released, some of the temporary enterprise features are enabled by default, But you can of course disable them if you want. Other functionality is disabled by default, and can be enabled if you want.
So for example to disable Windows Copilot, a CSP is available under: ./User/Vendor/MSFT/Policy/Config/WindowsAI/TurnOffWindowsCopilot. Strangely enough, no Settings Catalog setting is (yet) to be found.
Microsoft provides an overview of the permanent feature control features, and how you can enable/disable them. You can find that table in the following article: Enterprise feature control in Windows 11 – What’s new in Windows | Microsoft Learn.
As the table explains, the Windows CoPilot functionality should have been enabled, but due to regulations in Europe, we still don’t see the Windows CoPilot on our devices. So there is something else (not documented in the article) stopping the rollout. Once Microsoft gets a Go though, Windows CoPilot will automatically be enabled on 23H2 devices if you don’t do anything about it.
When features are made available using an enablement package, we cannot uninstall the feature by uninstalling the feature update using the Intune methods. If you want to uninstall you need to follow the methods detailed in the following article: Uninstalling Windows updates on managed devices using Intune – Microsoft Community Hub
Driver updates for Windows 10 and later
In June this year (2023), Microsoft made Driver and Firmware management generally available. Driver updates can be made available by creating a driver update policy to be found in the Microsoft Intune portal under “Driver updates for Windows 10 and later”
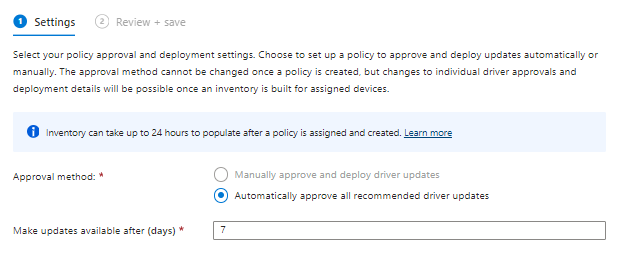
Creating driver update policies is relatively easy, since there are 2 options:
- Whether you want to automatically or manually approve driver updates
- When to make the update available
Based on my Windows Update Rings I configured the following driver set policies
| Setting | Update Ring 1 | Update Ring 2 | Update Ring 3 |
| Approval Method | Automatically | Automatically | Automatically/Manual |
| Make updates available after (days) | 0 | 3 | 7 |
The driver updates have been challenging to implement, first of all since they are not released on patch Tuesday, and therefore we have not control over “when” the drivers should be made available. We can only define how many days after being available the drivers will be installed. I also had an interesting issue where a driver installation initiated the BitLocker recovery key process. Once the support call was created, the Intune team pointed to the Windows team, and the Windows team said it was by design because the BitLocker recovery key is needed in circumstances where something in the hardware changes.
If you want to do this right, you also have to start thinking about what hardware the users in your Ring 1 and Ring 2 should have in order to properly test this. If you are not in-control here, setting the setting for Update Ring 3 to manual is the only option you have. But this introduces extra manageability and monitoring efforts.
Sharing is caring
For easy import, I exported my config using the Intune Manager tooling written by Mikael Karlsson, so that you can easily import it into your own environment.
The source files can be found here: kennethvs/WUfB-Baseline-122023 (github.com)
Summary
Implementing the necessary settings in order to have a reliable and consistent Windows Update experience can be challenging. It’s clear that Microsoft is seeing that as well, hence the reason for Windows Autopatch. For me Autopatch has some disadvantages though, like the license requirements, the fact that it works device based and the custom naming of the created policies which doesn’t align with my own naming convention. Also Windows Autopatch only handles part of the configuration that you want to rollout in a controlled manner, and lacking support for Microsoft Defender but doesn’t provide any strategy to rollout new configurations like Configuration Profiles or new Conditional Access policies.
So if you are in the same situation as me, I hope this article will help you to implement your own settings for Windows Update for Business and especially to build something which makes sense for the users as well.



Thank you for the baseline settings. What is your recommendation regarding the assignment? Do you work with user or device groups for the Update Rings, Feature Update Rings, and Driver Update Rings?
Hi Maximilian,
I prefer to assign everything to a user group, for me (based on experience) that gives the best result. If distinction between machine types must be made, use filters
Regards,
Kenneth
Hi Kenneth,
If we’re patching through rings using with user targeted groups, what would happen if user A who is in the first patch ring started using a colleagues laptop B for 1-2 days which is in the last patch ring?
Would laptop B, given enough usage from user A receive the first patch ring, and if we were doing feature updates targeted at users, would laptop B also consume the feature updates targeted to user A?
Sorry for my late reply, I didn’t notice this question before
So it depends on whether your target user groups or device groups. In the case of device groups, I think its obvious that the policies only hit the device. If you target user groups the policies will become applicable for the user that logs on to the device, and that can lead to strange configurations if other users (in different update rings) login to that device as well.
I personally don’t want users to login to different laptops in this setup, if multiple users must login to one device, please use a shared device profile where you target these policies on device level
/Kenneth
Kenneth,
Long time CM admin, first week intune admin.
Your blog directly addressed some of my questions so thank you.
One thing I’m having trouble getting my head around – suppose you have 50k+ w365 devices. You have a deferral period for up to 28 days, across 4 rings.
20 days into the cycle, the business announces a change restriction for 2 weeks for a single LOB (likely the result of some change breaking production) .
In the CM world this is not a problem. You simply add an exclude rule to the target collection , update collection membership and the other LOBs continue patching. 2 weeks later you setup a one-off deployment of last months SUG and everything is patched.
In intune, if you make a dynamic group change, you are waiting for that membership change for up to 24 hours? Then at the end of the restriction period, you are passed the maximum 30 day deferral period for wufb – so there is no option to have those unpatched machines install last months updates. The last ring is usually the most sensitive user base, so you certainly don’t want those users to be the first to apply n+1 months patches.
This seems like too obvious of a scenario for MS to have overlooked, but after hours of googling, I still don’t know it’s even possible.
Do you have any blogs you’d suggest on these topics? Any experience in your world?
Hi Alex,
First of all, 28 days deferral is not a best practice, and is really coming from the “old way” of working, that’s something you must re-think in my opinion. I understand where its coming from, but it’s not necessarily something which fits the “modern management” though which Intune is built-upon. If it doesn’t match.. keep using ConfigMgr which does the job and has proven it for a long time.
When grouping the w365 in their own deployment ring you can pause the deployment of the quality updates, so just isolate the W365 (using device filters) and pause if this happens. Again, I would advise against waiting for 28 days and try to have everything patched within preferably 7 days.
Again, I understand where you are coming from – but when mixing new technology (W365) with principles from the past, things get “tricky”
/Kenneth
Great article! How would you go about setting up a grace period to restart after 6 hours?