In a modern managed workplace environment, ensuring that devices meet minimum operating system (OS) requirements is a critical aspect of security and compliance. By governing the OS versions allowed within your Microsoft Intune environment, you can prevent unsupported or outdated systems from accessing corporate resources. Additionally, having well-configured Windows Update for Business (WUfB) settings can support enforcing OS versions later on by streamlining updates to meet compliance. For more information, refer to Configuring even better Windows Update for Business settings for your Microsoft Intune managed modern workplace. To understand what OS versions are supported by Microsoft Intune, refer to Microsoft Intune Supported OS Documentation. This blog outlines the steps and strategies to configure OS version governance using device enrollment restrictions and compliance policies for various platforms, including Android Enterprise, iOS/iPadOS, macOS, Windows 10 and later, and Linux. Last but not least, we also discuss how to configure OS versions in Conditional Launch as part of an App Protection Policy for MAM
This article contains the following sections:
- Why Govern OS Versions? – Explains the importance of OS version control for security, compatibility, and compliance.
- Overview of Options – Describes the two primary methods for OS governance: device enrollment restrictions and compliance policies.
- Determining the versions to use – Covers how you can find what values you need to provide for each OS
- Configuring Device Enrollment Restrictions – Covers how to define OS version requirements during device enrollment.
- Configuring Compliance Policies – Discusses setting up compliance policies to enforce OS versions over time.
- Configuring Conditional Launch in App Protection Policies for MAM – Discusses how to configure conditional launch within your App Protection Policy.
- Summary – Recaps key takeaways on managing OS versions in Intune.
- References – Provides links to official vendor documentation and resources.
Why Govern OS Versions?
There are several reasons to enforce OS version control within your organization:
- Security: Older OS versions may lack critical security patches, exposing devices to vulnerabilities.
- Compatibility: Ensuring devices meet minimum requirements for applications and services.
- Compliance: Adhering to internal policies or regulatory standards.
- User Experience: Maintaining functionality and performance with supported features.
Overview of Options
Microsoft Intune provides two primary methods to govern OS versions:
- Device Enrollment Restrictions: These rules prevent devices with unsupported OS versions from enrolling in Intune.
- Compliance Policies: These policies check enrolled devices to ensure they meet OS version requirements and mark non-compliant devices appropriately.
Both options can be configured for Android Enterprise, iOS/iPadOS, Windows 10 and later. For macOS and Linux we can only use a Compliance Policy as setting the version in Device Enrollment Restrictions is not available.
Determining the versions to use
To ensure compliance and security, it’s important to determine the correct OS versions for each platform. The following resources can be used to find the latest supported OS versions, build numbers, and security patch levels:
- Android: Refer to the Android Security Bulletins and Android version history to determine the minimum security patch levels and OS versions.
- iOS/iPadOS and macOS: Check Apple’s official release notes and Apple Developer News Releases for details on OS versions and build numbers.
- Windows 10 and later: Use
- Linux: Refer to Linux kernel version history and distribution-specific documentation such as Ubuntu, Red Hat, or Debian to find the latest supported kernel versions.
By leveraging these sources, organizations can ensure that devices meet security and compliance requirements while maintaining functionality.
Configuring Device Enrollment Restrictions
When setting up Device Enrollment Restrictions, you can define different requirements for OS versions depending on the organization’s needs. From an enrollment perspective, devices should meet a minimum OS version to ensure compatibility with the latest deployment functionalities. However, organizations can allow updates to be applied later, ensuring security patches and compliance improvements over time. This approach balances the need for immediate functionality with long-term security. Currently, Linux does not support enrollment restrictions in Microsoft Intune.
General Steps:
- Navigate to Devices > Enrollment restrictions in the Microsoft Intune admin center.
- Select the platform (e.g., Android, iOS/iPadOS, or Windows).
- Choose Create restriction or edit an existing restriction.
- Provide name and description
- Define the minimum and maximum OS versions under platform settings. You should define versions as major.minor.build.
- Save and apply the restriction.
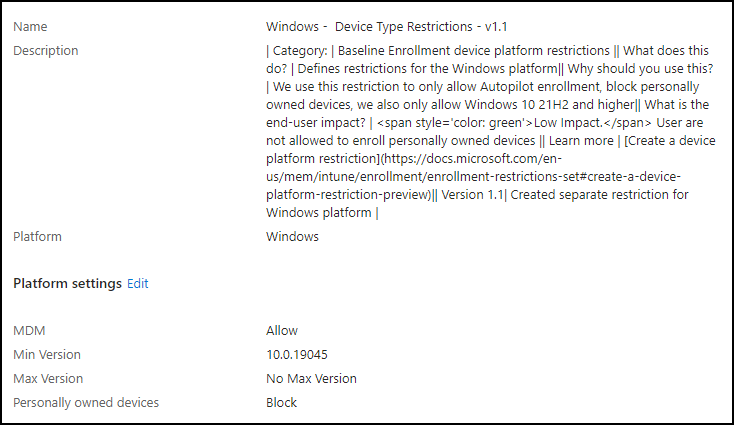
For example, this is a possible option for setting the Device Enrollment Restriction for Windows devices, where we only allow Windows 10 22H2 and higher versions. And with the upcoming end of support for Windows 10, you might want to adjust this to at least version 19.9.22631.0 (Windows 11 23H2). The minimum supported version should at least be equal to the minimum supported version which Microsoft supports, see Microsoft Intune Supported OS Documentation
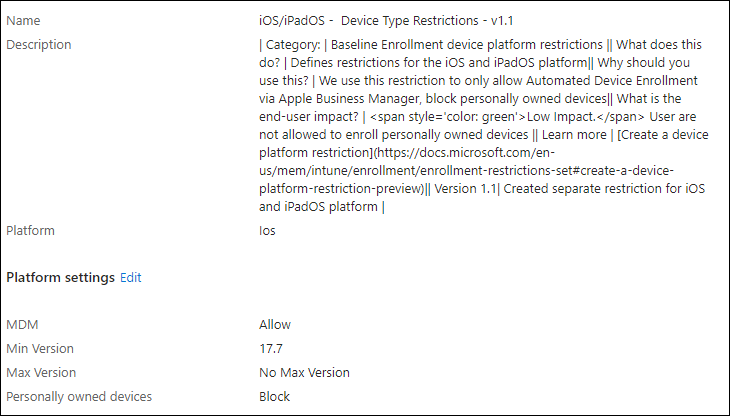
In the following example, we set the Device enrollment restrictions for iOS/iPadOS. Here we only allow enrollment of version 17.7 and higher.
Configuring Compliance Policies
Defining compliance policies should be based on security risks. Organizations must determine the minimum and maximum OS versions that align with security and functionality requirements. The OS version requirement should mitigate security vulnerabilities while ensuring devices remain operational and compatible with corporate resources. The amount of time before a device is considered non-compliant (the grace period) is a key factor in choosing whether to use one or multiple compliance policies. A shorter grace period enforces compliance more strictly, while a longer grace period allows gradual enforcement to minimize disruption.
The compliancy status can later be used in Conditional Access in order to determine whether resources are available for the device.
To manage this effectively, organizations can create multiple compliance policies:
- Primary Compliance Policy: This policy defines the minimum allowed OS version. Devices that do not meet this requirement will be marked as non-compliant immediately, preventing access until they are updated.
- Secondary Compliance Policy: This policy sets the desired OS version with a longer grace period. This allows devices sufficient time to update while gradually enforcing security standards.
This approach provides flexibility while ensuring security compliance over time.
General Steps:
- Navigate to Devices > Compliance policies in the Microsoft Intune admin center.
- Select Create Policy and choose the platform.
- In the configuration, specify minimum and maximum OS versions, OS Build versions, and security patch levels as needed.
- Assign the policy to appropriate groups.
- Monitor compliance in the Reports section.
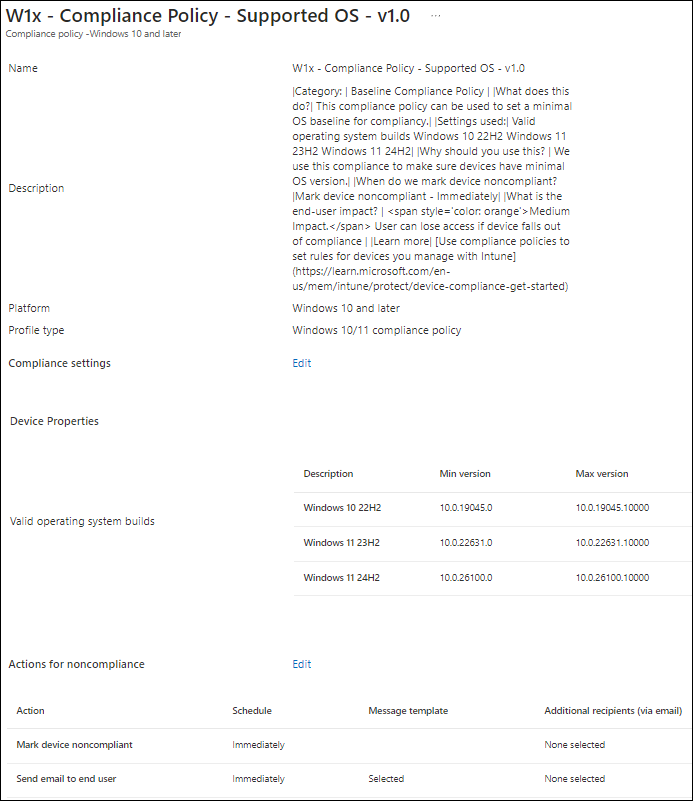
Below is an example of the minimum supported OS versions that we want to support on Windows. We configure this compliance policy in such a way that if the device doesn’t meet these versions, it will be non-compliant immediately.
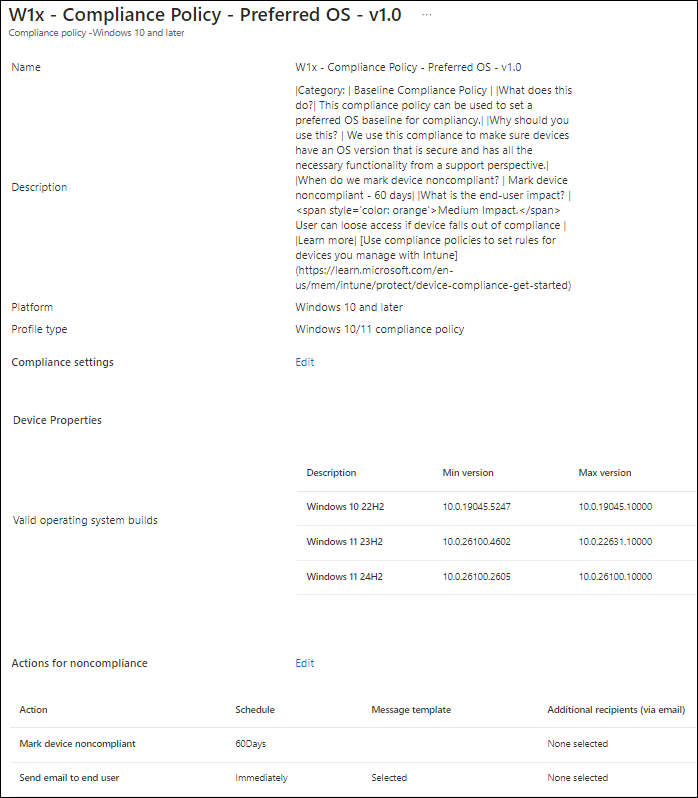
For the versions that we prefer, we can have a more relaxed policy, for example the one below, where we set the Mark device noncompliant setting to 60 days, allowing devices to become compliant in 60 days.
Challenges with Android OS Updates
Managing OS versions for Android devices presents unique challenges due to the fragmented nature of the Android ecosystem. Unlike iOS and Windows, where updates are controlled centrally by Apple and Microsoft, Android updates depend on device manufacturers and carriers. This means that:
- Different vendors release updates at different times, making it difficult to enforce a unified OS version requirement.
- Some Android devices may receive updates months after Google releases a new Android version.
- Certain models might not receive updates at all, leading to security risks if they fall behind on patching.
To mitigate these challenges, organizations should:
- Define OS version requirements based on security patch levels rather than just major OS versions.
- Regularly review vendor update schedules and restrict devices that no longer receive updates.
- Encourage the use of Android Enterprise Recommended (AER) devices, which follow stricter update policies.
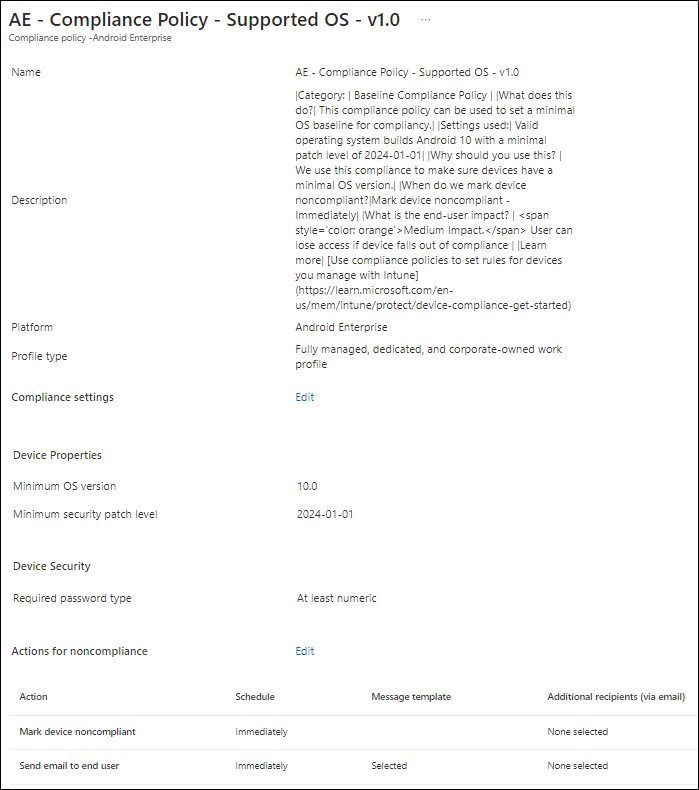
For Android we therefore specify the minimum security patch level, for the Android OS versions that we want to support. Be careful though with this especially with Android, there are simply too many versions and therefore an inventory of what is available within your environment is necessary to minimize the impact of this change.
Configuring Conditional Launch in App Protection Policies for MAM
When using Mobile Application Management in Intune, you create an App Protection Policy to define the policy applicable for the MAM protected app on the iOS/iPadOS or Android device.
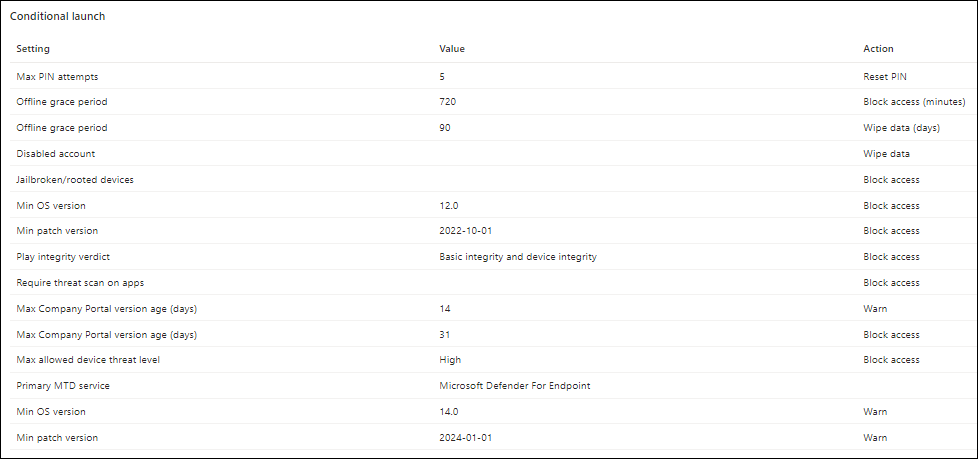
Here we have the option to either Warn of Block access based on OS Version, so for example in the configuration of an App Protection Policy for Android, we specify OS version 12 with a patch level of 2022-10-01 as the minimum level (or else we block access), but warn users if they have an OS version less dan 14.0 with patch level 2024-01-01.
Note: this is just an example, again be very careful when it comes to Android
Summary
Governing OS versions is a fundamental part of managing a secure and compliant device environment in Microsoft Intune. By configuring device enrollment restrictions and compliance policies, you can ensure that only supported OS versions are allowed within your organization. Regularly update these policies to reflect the latest vendor releases and security updates.
The purpose of this article is give an overview of the options, and provide some possible scenario’s on how to have better control over which OS versions are available within your Modern managed environment.