As Microsoft continues to enhance security across its platforms, Multi-Factor Authentication (MFA) is becoming mandatory for an increasing number of administrative portals. This shift means that relying solely on a username and complex password for break glass accounts is no longer viable and should be revisited (if not already done).
This initiative aligns with Microsoft’s Secure Future Initiative, which was introduced in response to the increasing sophistication of cyber threats and the need for a more resilient security framework. Microsoft launched this initiative in response to a critical report from the U.S. Cyber Safety Review Board (CSRB) following a significant cyber incident involving unauthorized access to U.S. government email accounts. The report highlighted security gaps, prompting Microsoft to commit extensive resources to improving its security posture by addressing vulnerabilities, enhancing authentication security, and reducing reliance on outdated security models like passwords, which are often targeted in attacks. For more details, refer to the official Microsoft report on the initiative here.
In this article, we’ll explore which admin portals currently enforce MFA independently of Conditional Access policies, provide an overview of upcoming changes, and discuss best practices for managing and protecting break glass accounts in this evolving landscape.
Current and Upcoming MFA Enforcement on Admin Portals
Microsoft has implemented MFA enforcement on several admin portals to bolster security, with additional enforcement scheduled for the near future. This enforcement will also apply to break glass accounts that have been excluded from Conditional Access policies, meaning organizations must ensure these accounts are compliant with updated authentication requirements. Notably:
- Azure Portal: MFA is enforced for all users with privileged roles.
- Azure DevOps: MFA enforcement is in place for users accessing the portal.
- Microsoft 365 Admin Center: Microsoft will begin rolling out mandatory MFA enforcement starting February 3, 2025. This rollout will be gradual, with notifications sent approximately 30 days before enforcement begins for specific tenants. For more details, refer to the official Microsoft announcement here.
Microsoft has announced plans to extend MFA enforcement to additional portals, including a gradual rollout for Microsoft 365 Admin Center starting February 3, 2025. Administrators should proactively enable MFA to avoid access disruptions. Administrators should proactively enable MFA to avoid access disruptions. While specific timelines may vary, administrators should anticipate MFA becoming mandatory across all management interfaces. For the most current information on MFA enforcement timelines, refer to Microsoft’s official documentation:
Best Practices for Managing Break Glass Accounts
Given the increasing enforcement of MFA, it’s essential to adopt best practices for managing break glass accounts:
- Limit the Number of Break Glass Accounts: Maintain only the minimum number necessary to reduce security risks.
- Use Strong Authentication Methods: Implement phishing-resistant MFA methods, such as FIDO2 security keys, to enhance security.
- Monitor Account Activity: Set up alerts for any unusual or unauthorized access attempts.
- Document and Train: Maintain clear documentation on the use of break glass accounts and train relevant personnel on proper procedures.
For detailed guidance, consult Microsoft’s recommendations:
Protecting Break Glass Accounts with Authentication Method Policies
To safeguard break glass accounts, first ensure that your organization has migrated to the new authentication method policies. This step is critical as it allows for better control and flexibility in managing authentication methods. After migration, utilize authentication method policies to restrict allowed methods, ensuring compliance with Microsoft’s best practices. For more details, refer to Microsoft’s official documentation on managing authentication method policies.
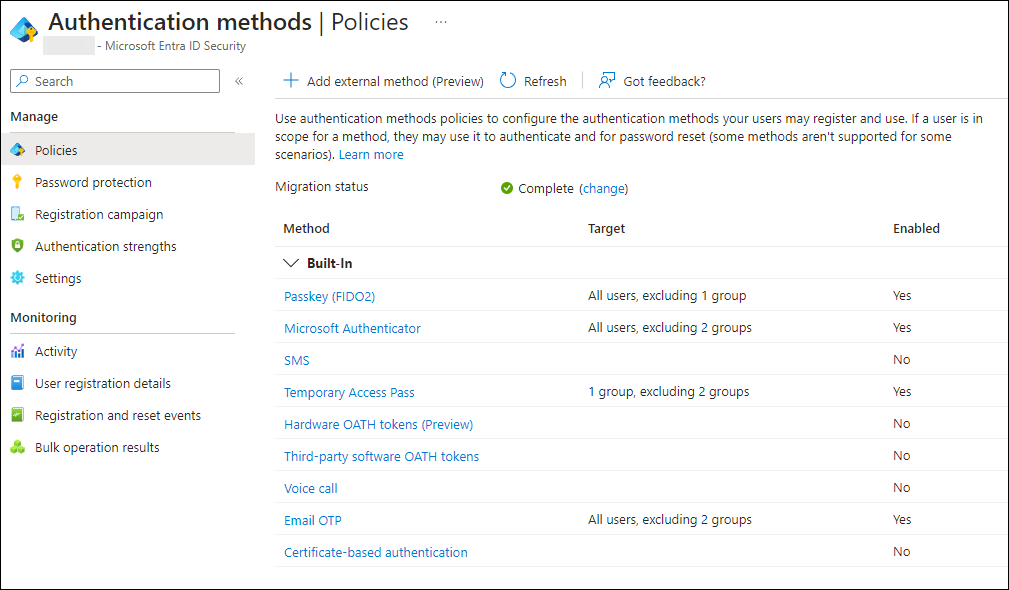
Explanation of the screenshot: As you can see , in my environment we do not allow SMS, Hardware OATH tokens, Third-party software OATH tokens, Voice call and certificate-based authentication. Passkeys, Microsoft Authenticator and email OTP are enabled, but we do exclude the group containing the break glass accounts, and a group containing service accounts (accounts which cannot have MFA configured at all, mainly for legacy purpose and reasons), which are restricted by a Conditional Access location policy. For Passkey (FIDO2), we don’t exclude the break glass account group, but do restrict service accounts from creating passkeys. Temporary access pass is available for a specific group containing our Modern Workplace users, during creation of the TAP for the break glass account we should add the account temporarily to the group.
For comprehensive instructions, refer to:
Rolling Out a New Break Glass Account Using TAP and Registering a FIDO2 Security Key
To implement a new break glass account with a FIDO2 security key:
- Create the Account: In Azure AD, set up a new user designated as a break glass account. Use a password generator to generate an initial password which is very long and do not safe the password.
- Assign Privileged Roles: Grant the necessary administrative roles to the account.
- Exclude from Conditional Access Policies: Ensure the account is excluded from ALL conditional access policies that might block access during emergencies.
- Generate a Temporary Access Pass (TAP) with a very limited timeframe for the account, make sure that account is temporarily added to the group for which TAP usage is allowed.
- Register FIDO2 Security Key:
- Access Security Info: Sign in to the Azure portal with the break glass account and use TAP, then navigate to My Profile > Security info.
- Add Method: Select ‘Add method’ and choose ‘Security key’.
- Follow Prompts: Insert the FIDO2 security key and follow the on-screen instructions to complete registration.
- Test Access: Verify that the break glass account can access necessary portals using the FIDO2 security key.
For detailed steps, see:
Summary
As MFA becomes increasingly enforced across Microsoft’s admin portals, it’s crucial to adapt the management of break glass accounts accordingly. By implementing best practices and utilizing authentication method policies to enforce phishing-resistant MFA methods like FIDO2 security keys, organizations can ensure that these critical accounts remain secure and accessible when needed.
References

This is a well-timed reminder of the changes coming with enforced MFA and the importance of adapting break glass account management. The TAP and FIDO2 key setup is a practical solution! Thanks for sharing.
After this is set up i would encourage the exclusion of tap for the breakglass account as it could be used as a privilege escalation path