With the introduction of a converged policy combining settings from the legacy MFA portal and SSPR configuration, separating the use of SMS for password resets from its use as an MFA method has become challenging. This guide explains how to configure authentication policies effectively using authentication strengths in Microsoft Entra to address this issue.
Table of Contents
- Why This Matters
- Key-Configuration-Options
- Step-by-Step Configuration
- Benefits of This Approach
- Conclusion
- References
Why This Matters
Organizations need flexible authentication options to balance security and user convenience. While SMS can be useful for password resets, its vulnerabilities—such as interception and SIM swapping attacks—make it less suitable as an MFA method. Microsoft Entra’s conditional access policies provide the tools to manage these scenarios securely.
Key Configuration Options
- Enable SMS for Password Resets Only
- SMS can simplify password recovery for end users but should be restricted to avoid compromising MFA security.
- Leverage Authentication Strengths
- Authentication strengths allow administrators to define which authentication methods are acceptable for MFA, providing granular control.
- Restrict SMS in MFA Conditional Access Policies
- By defining policies that exclude SMS for MFA, you maintain stronger security for multi-factor authentication.
Step-by-Step Configuration
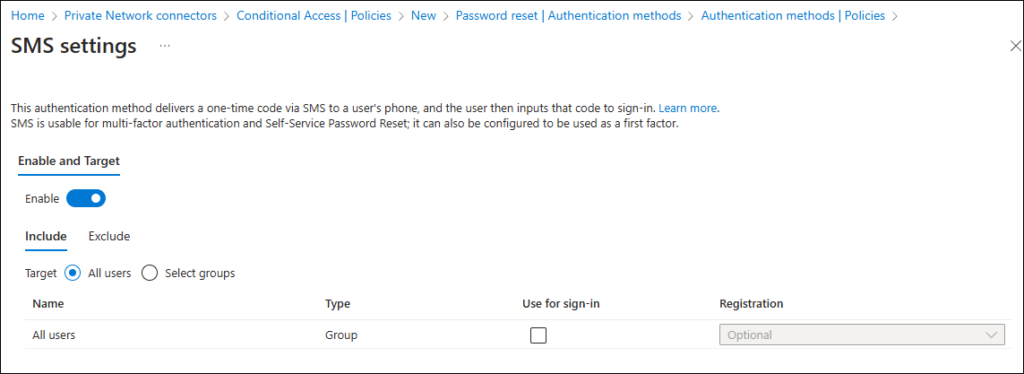
Enable SMS in Authentication Method Policies
- Log in to the Microsoft Entra Admin Center.
- Navigate to Security > Authentication methods.
- Enable the SMS option to allow users to register their phone numbers for password reset.
If you don’t want users to sign-in with their phone-number (scenario mainly for specific frontline worker cases) disable the option “Use for sign-in” – also make sure that you exclude groups of users for which you don’t want them to register SMS settings, think of break-glass accounts and non-personal service accounts.
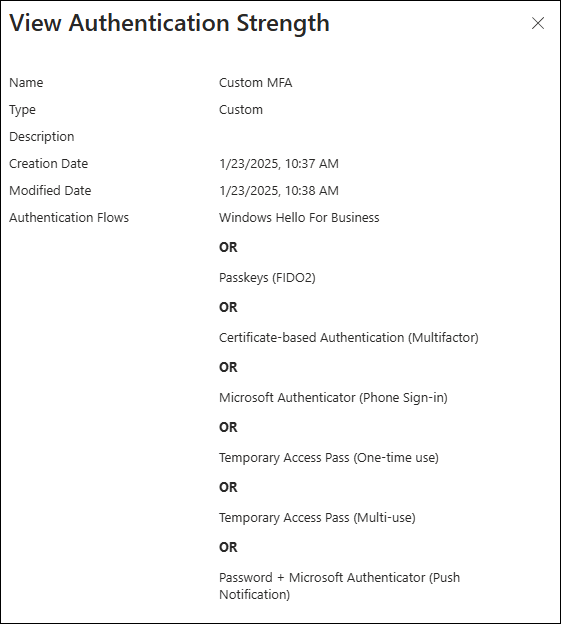
Define an Authentication Strength in Entra
- Go to Microsoft Entra > Protection > Conditional Access > Authentication strengths.
- Create a new authentication strength policy, selecting the methods you want to allow (e.g., passwordless and phishing-resistant options like Microsoft Authenticator or FIDO2).
- Make sure to at least exclude SMS from the list of permitted methods.
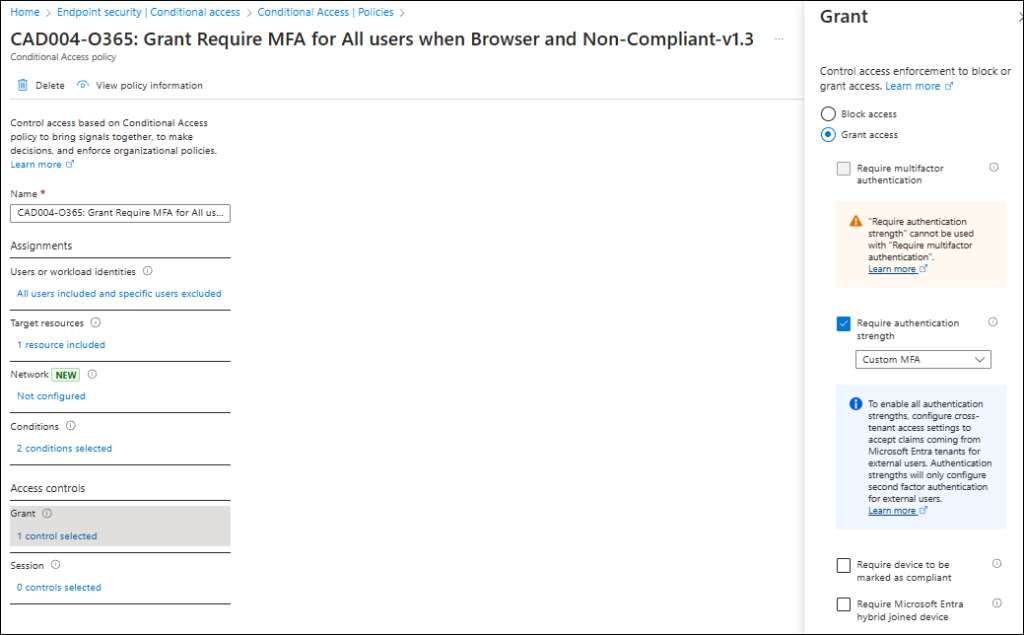
Create or modify your Conditional Access Policy
- Navigate to Security > Conditional Access.
- Click + New policy to create a new conditional access rule.
- Configure the following:
- Assignments: Select users, groups, or roles to apply the policy.
- Cloud Apps or Actions: Choose the apps requiring MFA.
- Conditions: Define specific conditions, such as sign-in risk or location.
- Under Grant, choose Require authentication strength, and link it to your newly created authentication strength policy.
- Save the policy.
Test and Monitor
- Ensure users can register their phone numbers for password resets.
- Verify that MFA prompts do not include SMS as an option during sign-ins.
- Use Entra logs to monitor authentication attempts and confirm the policy is functioning as intended.
Benefits of This Approach
- Improved Security: SMS is restricted to low-risk scenarios, reducing exposure to attacks.
- User Convenience: Users retain the ability to reset passwords via SMS.
- Granular Control: Conditional access policies ensure alignment with organizational security goals.
Conclusion
Using Microsoft Entra’s authentication strengths and conditional access policies allows organizations to enable SMS for password resets while maintaining robust security for MFA. By separating these use cases, you enhance both user experience and overall security posture. 🚀