With the increasing reliance on mobile devices in the workplace, organizations must choose the right strategy to manage and secure corporate data. Microsoft offers two primary options: Mobile Application Management (MAM) and Mobile Device Management (MDM). Understanding the differences between these approaches is essential for balancing security, user experience, and administrative effort.
This article provides a structured decision-making guide to help determine whether MAM or MDM is the best fit for a given scenario.
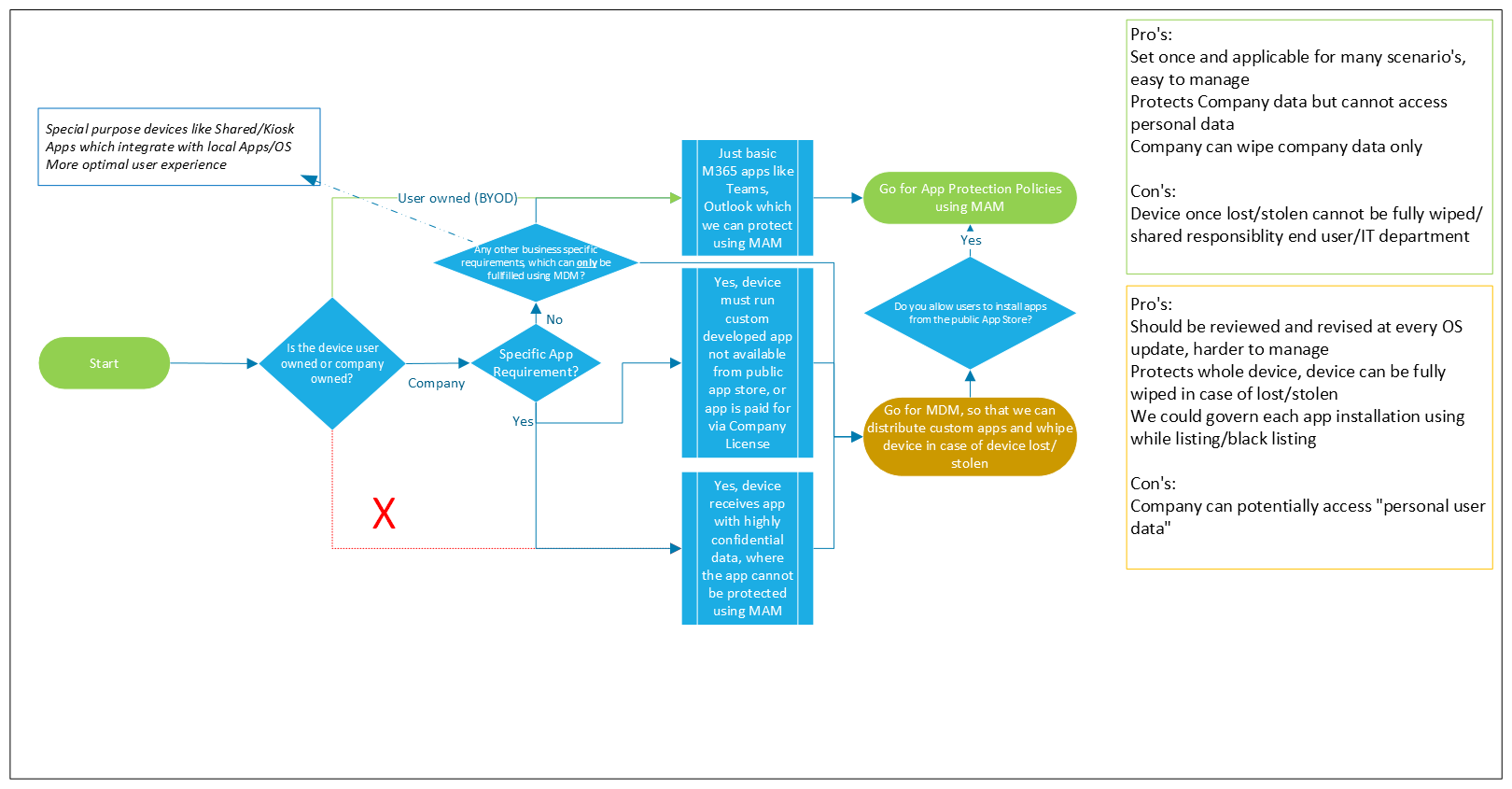
Decision Flow: When to Use MAM, MDM, or Both
There are scenarios where MDM is a requirement, cases where the choice depends on business needs, and situations where MAM is the only viable option. Understanding these distinctions ensures a well-balanced approach.
The choice between MAM and MDM depends on several factors, including device ownership, app requirements, and data sensitivity.
1. Determining App Requirements
- If only basic Microsoft 365 apps (such as Teams and Outlook) are needed, and they can be protected using MAM, then MAM is sufficient.
- If a device must run a custom-developed app not available from a public app store or requires company-paid applications, then MDM is the preferred option.
- If the app contains highly confidential data and cannot be adequately protected with MAM alone, MDM is required.
2. Device Ownership and Policy Consideration
- In some cases, MDM is required. For example, regulatory compliance, enforcing passcodes, or managing corporate-owned devices necessitate MDM.
- In other cases, the choice depends on business needs. If security policies require both device management and app protection, organizations should weigh the pros and cons of a hybrid approach (MAM on top of MDM).
- There are also scenarios where MAM is the only viable option, particularly for BYOD. Since users own the device, enforcing full device management is not practical or desirable.
- If the device is company-owned, then MDM is generally recommended to enforce security policies, control installations, and enable full device wipe capabilities.
- If the device is user-owned (BYOD), MAM is the preferred choice to protect company data while respecting user privacy.
- Some organizations provide devices to employees but allow them to install personal apps and use them as if they were personally owned. These devices operate in a corporate-owned, personally enabled (COPE) model. In this case, MDM is often used to enforce baseline security policies, such as configuring corporate WiFi or enforcing encryption, while MAM can further protect corporate apps and data without restricting personal use. Additionally, organizations can opt for a MAM-only approach on these devices if the MDM configuration is minimal, ensuring that corporate data remains protected without fully managing the device.
3. App Installation Policies
- If users are allowed to install apps from the public App Store, MAM on top of MDM can be a viable option to make sure that company data cannot leak through publicly available apps.
- If specific business requirements mandate MDM, such as:
- Shared/Kiosk devices
- Apps that integrate with local OS or other apps
- More controlled user experience then MDM should be implemented.
Options with Microsoft Intune
MAM-Only (App Protection Policies without MDM Enrollment a.k.a. MAM-WE)
- Best for BYOD scenarios where users do not want to enroll their devices in MDM.
- Protects company data within managed apps like Outlook, Teams, and OneDrive.
- Supports conditional access policies to enforce security compliance.
MDM-Only (Full Device Management)
- Suitable for corporate-owned devices requiring full control.
- Enforces device compliance policies, such as encryption and password requirements.
- Enables remote wipe and app whitelisting/blacklisting.
MAM on top of MDM (Hybrid Approach)
- Best for scenarios where corporate devices need both device-level and app-level protection.
- Allows organizations to enforce device-wide security while applying app-specific protections.
- Provides granular control, enabling selective data wipe in case of employee offboarding.
- Ensures that even if a fully managed device is compromised, apps remain protected with MAM policies.
Pros and Cons of MAM and MDM
MAM (App Protection Policies)
Pros:
- Set once and applies to multiple scenarios, making it easy to manage.
- Protects company data while ensuring personal data remains inaccessible to IT.
- Allows selective wiping of company data without affecting personal data.
Cons:
- If a device is lost or stolen, the entire device cannot be wiped, only corporate data can be removed.
- Security responsibility is shared between the end user and the IT department.
MDM (Device Management Policies)
Pros:
- Ensures full control over the entire device, allowing for a complete wipe if lost or stolen.
- Provides governance over app installations through whitelisting and blacklisting.
Cons:
- Requires frequent updates and policy revisions with every OS update.
- Harder to manage compared to MAM.
- Can potentially grant the company access to personal user data, raising privacy concerns.
Additional Considerations
Passcode Enforcement and MFA Security
If enforcing a device passcode is required, such as for protecting access to the Microsoft Authenticator app, MDM must be used. MAM alone cannot enforce a passcode or biometric authentication for the Authenticator App at the device level. However, it is important to note that passcode/biometric enforcement is not universally applicable to all MFA-supported authentication methods.
For organizations implementing Passwordless or Phishing-resistant MFA, the Microsoft Authenticator app requires configuring a passcode or PIN, with biometrics applied where applicable. This ensures that authentication remains secure even when MAM is used for app protection.
Conclusion
Organizations must recognize that some scenarios demand MDM, while others allow for flexibility. When MDM is required, such as for enforcing security policies on company-owned devices, it ensures full control. However, in cases where the decision depends, IT teams must carefully evaluate the trade-offs between security, privacy, and administrative overhead. Finally, when MAM is the only viable option, especially for BYOD environments, it provides a way to protect corporate data while maintaining user privacy, with least administrative effort.
Choosing between MAM and MDM depends on the organization’s needs and security policies. MAM is best for BYOD environments where personal privacy is a concern, whereas MDM is ideal for company-owned devices requiring complete control over security and applications. The hybrid approach of MAM on top of MDM allows organizations to gain the benefits of both solutions, ensuring device compliance while enforcing application security.
By leveraging the right mobile management strategy with Microsoft Intune, businesses can ensure a secure and efficient mobile workforce while maintaining a balance between usability and compliance.
1 thought on “MAM vs. MDM: Choosing the Right Mobile Management Approach”