In April 2020 Alex Weinert, Director of Identity Security at Microsoft announced that Microsoft was working on moving towards real time policy and security enforcement. The first implementation for this move is now available as an option you can enabled within Azure AD, called Continuous access evaluation (CAE). The functionality released in April was only applicable for customers using the Azure AD Security defaults, on which I wrote a blogpost in January this year. Yesterday (October 9th 2020) though, Alex Simons announced that the CAE functionality is now also available for customers using Conditional Access policies. Keep in mind though that at time of writing this functionality is still in preview, and works with Exchange Online, SharePoint Online and Teams for now.
Continuous access evaluation allows for a quicker response by forcing an access token refresh in case of a certain events taking place. In this version of the preview the following events will be supported:
- User Account is deleted or disabled
- Password for a user is changed or reset
- MFA is enabled for the user
- Admin explicitly revokes all Refresh Tokens for a user
- Elevated user risk detected by Azure AD Identity Protection
Microsoft already announced that in the future these events will be extended to include for example location and device state changes. So, we can for example request MFA when the user switches from the trusted network to an untrusted network or block access when the device is becoming non-compliant.
Up until now, tokens for these scenarios were refreshed every hour, this can now be reduced to near real-time by using CAE. There is also an option to configure the lifetime for tokens overall, using configurable token lifetimes, which is also in preview at this moment, see: Configurable token lifetimes in Microsoft identity platform (preview). These configurable token lifetimes can be used in Conditional Access policies using the Sign-in frequency session controls, see: Configure authentication session management with Conditional Access, Sign-in frequency will be honored with or without CAE.
Continuous access evaluation is implemented by enabling services (resource providers) to subscribe to critical events in Azure AD so that those events can be evaluated and enforced near real time
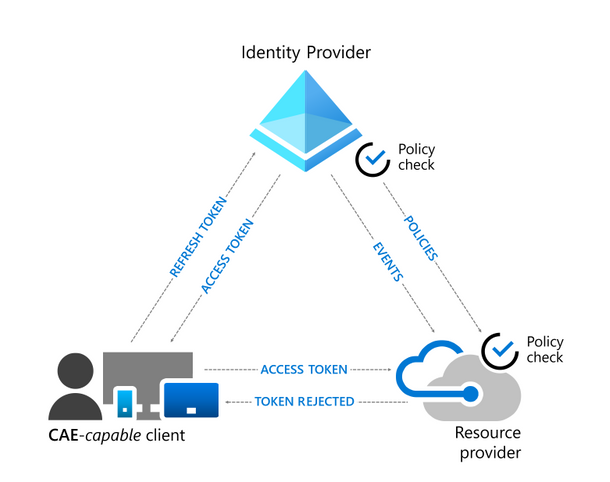
So how does it work?
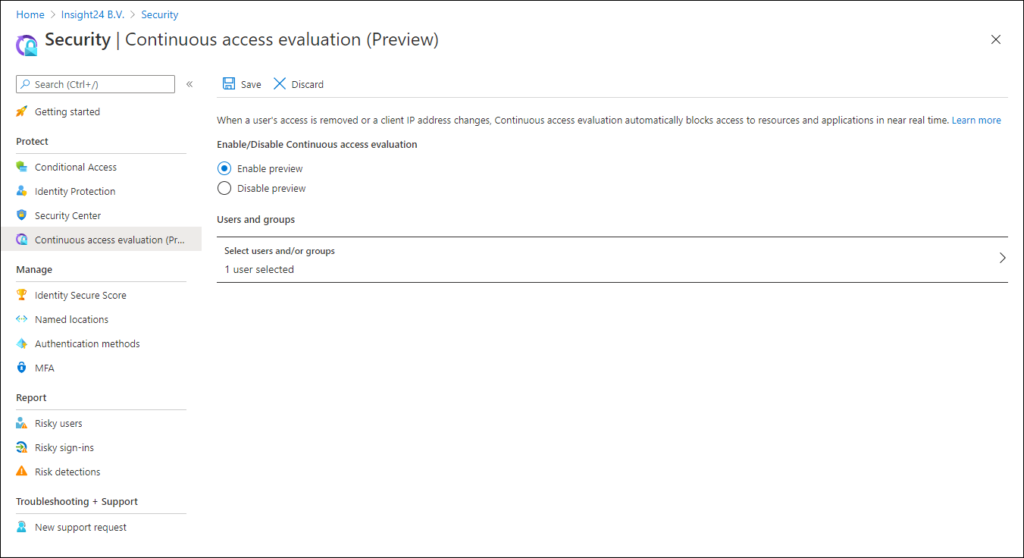
Continuous access evaluation can be enabled in the Azure AD portal. The setting can be found in the security blade. In the portal you have to enable the functionality, and you can define the setting to be enabled for All users of for specified users only.
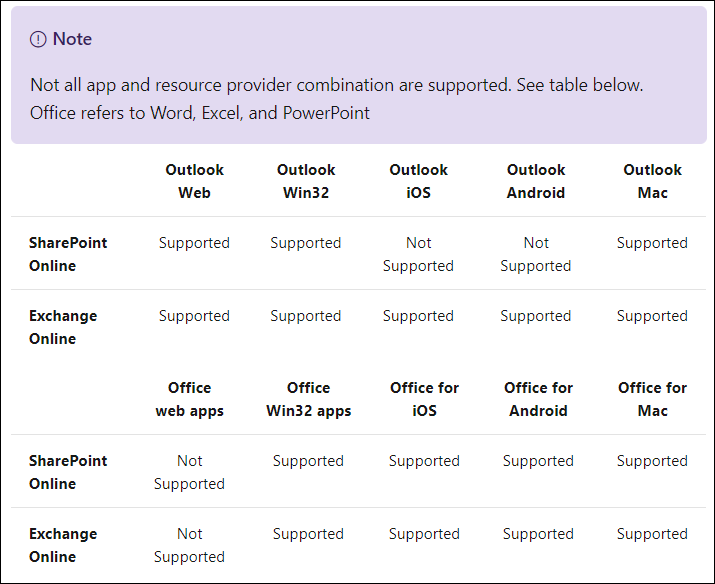
In order to inform clients to bypass their cache even though the cached tokens have not expired, Microsoft has introduced a mechanism called claim challenge. Clients need an update in order to support the concept of claim challenge, and for now the following clients have this update.
- Outlook for Windows, macOS, iOS and Android and Web
- Teams for Windows, macOS, iOS and Android
- Word/Excel/PowerPoint for Windows, macOS, iOS, Android
For these clients not every scenario is available yet, Microsoft provides the following table to explain what’s possible:
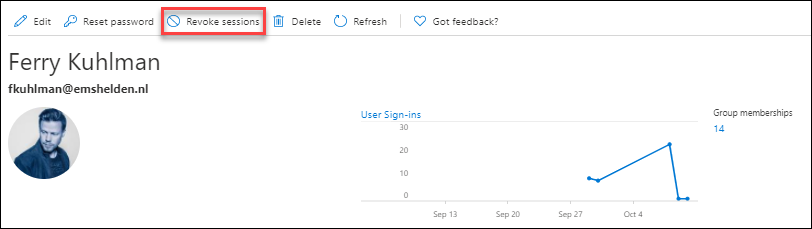
After enabling the feature, we can test the scenarios in different ways, for this blogpost I added the test account of Ferry Kuhlman as a user for CAE policy.
Revoke Sessions
So, I started a web browser session for my test user Ferry Kuhlman, logged into Outlook Web Access. Next, I went to the Azure AD admin portal and revoked all the sessions of Ferry
Within the minute Ferry was presented with the following screen:
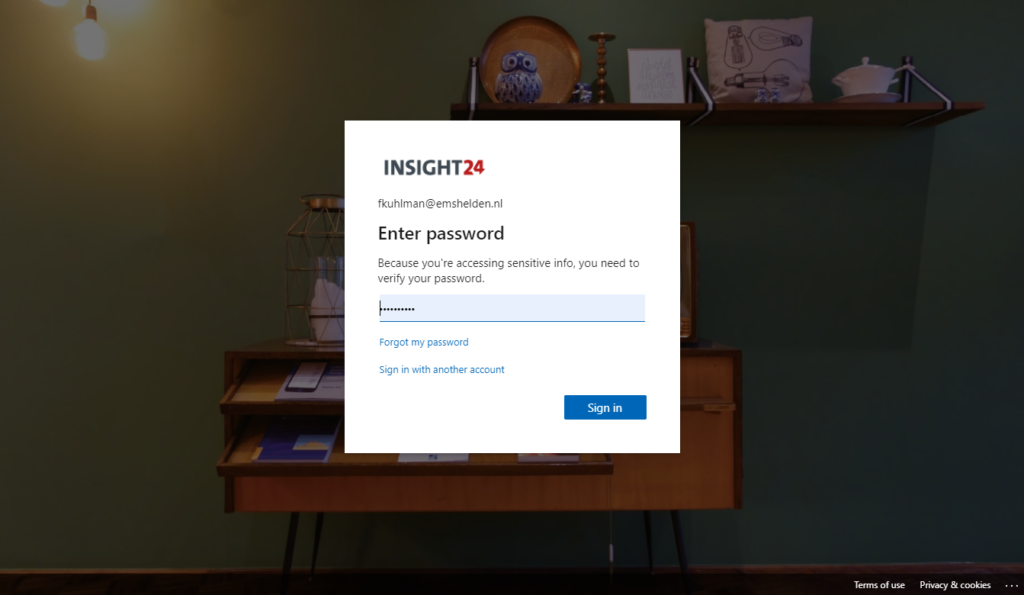
And from the Azure AD sign-in logging Sign-in error code 50133 was logged
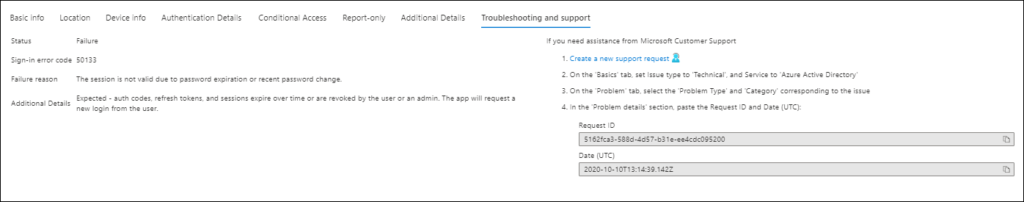
Testing with user not enabled for CAE
I then executed the same test using another test account, Stanley Messie. In my scenario it took a much longer time before the account was presented with the screen to login again. (5 minutes in my case)
Conclusion
Continuous Access Evaluation is a welcome addition to the already awesome options we have within Azure Active Directory. I will be closely following its capabilities, and start implementing it as soon as possible once released.
We’ll have to see whether both Microsoft and other vendors pick up on the requirement on having their apps updated in order to support Client-side claim challenges. The past has learned us that the Microsoft apps most commonly used (Office etc..) usually have the functionality quite fast, but other Microsoft apps and Partner apps usually fall behind, which can have impact on the total experience.
References
Moving towards real time policy and security enforcement, April 21 2020 by Alex Weinert
Azure AD security enforcement with Continuous Access Evaluation, May 5 2020 by Sonia Cuff
Continuous Access Evaluation in Azure AD is now in public preview!, October 9 2020, by Alex Simons
Configurable token lifetimes in Microsoft identity platform (Preview)
1 thought on “Azure AD Continuous access evaluation (CAE), a first look”