This week, during the virtual Ignite event Microsoft made several announcements related to the Modern Workplace. The event started yesterday (March 2nd) at 17:00 hours in my time zone (Amsterdam) with a keynote held by Microsoft CEO: Satya Nadella. The keynote was related to Microsoft’s vision for the future of Mixed Reality running on top of Microsoft Azure.
Right before the event started, my RSS feed ran over with all kinds of announcements which was a challenge on its own in order to keep up. It took me some time to digest all the news which hit us, and hopefully I managed to extract the key takeaways when it comes to news related to the Modern Workplace. Let’s see if the skills I built during my work as a news writer for virtualization.info/cloudcomputing.info in the 2010 – 2015 timeframe are still of any use.
The first place to start if you want to digest all the news coming from an Ignite (or any other big Microsoft event) is to search for the book of news. The March 2021 book of news contains an overview of all the news Microsoft released during the event. Besides what’s in the book of news I also have an RSS reader with lots of RSS feeds giving me the announcements coming from the different product groups within Microsoft.
My key takeaways below
Azure AD related announcements
All the Azure AD related announcement are summarized in the following article: Identity at Microsoft Ignite: Strengthening Zero Trust defenses in the era of hybrid work.
The Azure AD related announcements:
- General availability of passwordless authentication.
- Preview of Temporary Access Pass.
- Preview of Azure AD Conditional Access authentication context.
- AWS Single Sign-On now available in Azure AD app gallery.
- General availability of AD FS activity and insights report.
- New secure hybrid access partnerships with Datawiza, Perimeter 81, Silverfort, and Strata.
- General availability of Azure AD App Proxy support for header-based authentication apps.
- Preview of Azure AD App Proxy support for traffic optimization by region.
- General availability of Azure AD External Identities.
- General availability of Azure AD access reviews for all guests in Teams and Microsoft 365 groups.
- Preview of Azure AD verifiable credentials.
- Release of the Microsoft Identity and Access Administrator Certification.
Some more details about some of the announcements:
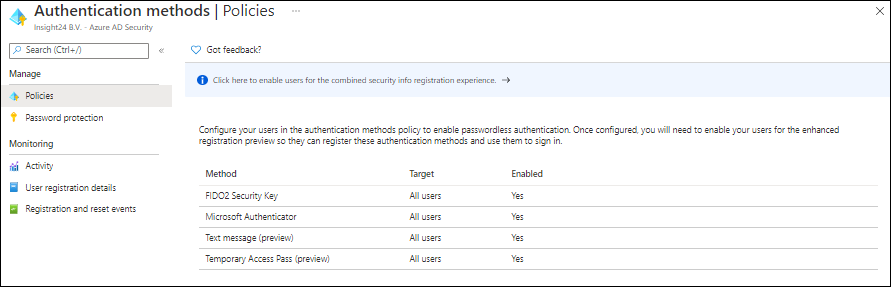
Passwordless and Temporary Access Pass.
Microsoft really wants companies to move away from using passwords only, by making passwordless authentication generally available customers can start implementing the different available passwordless authentication methods. You can do so by either configuring FIDO2 Security Keys, the Microsoft Authenticator app, Text message and Temporary Access Pass.
With the preview of the temporary access pass functionality users are now able to configure other passwordless authentication methods without even knowing their password. New users simply get a temporary password which they can use once (the Temporary Access Pass), with this they can setup their Authenticator App and/or Security keys. Once those are configured, the user can use these methods to logon to the system.
This assumes that the user will never need their password anymore, but just in case it’s needed it’s important to have Self Service Password Reset functionality enabled in that case, so that users can reset their password themselves. See: Enabling Self Service Password Reset (SSPR) for your Modern Workplace users
What’s also interesting to mention is that Microsoft now also supports signing in with a phone number and corresponding text message in certain scenario’s. This will not work for Modern Workplace scenarios, but is more suitable for what Microsoft calls “Frontline workers”, people only needing some specific information like for example access to Microsoft Teams.
Which authentication method to use in what scenario? – That is quite a complex question, the best way to start your passwordless journey is to read the following article and work from there: Create a resilient access control management strategy with Azure Active Directory.
Azure AD Conditional Access authentication context
Microsoft explains this concept as following: you can move away from one-size-fits-all security and adopt more granular policies that protect resources with the right level of controls based on user actions or the data they are trying to access.
As an example Microsoft mentions the following scenario: “For accessing certain sensitive sites, you may require additional authentication based on the condition in which user accesses them and the sensitivity and authentication context of the sites. For example, when users visit a Confidential labelled high-sensitive site you want to enforce a step-up authentication with granular policies like MFA (multi-factor-authentication) provided the user’s context does not meet the access requirement of the site.”
and
“For example, ‘Low authentication context’ requires single factor authentication whereas ‘High authentication context’ requires MFA like OTP (one time passcode) verification and IP network location policy. Admins can then associate the authentication contexts with MIP sensitivity labels in Microsoft 365 Compliance center. For example, ‘General’ label requires ‘Low authentication context’ policies whereas ‘Confidential’ label requires ‘High authentication context’ policies. When a sensitivity label is assigned to a site, the associated policies are automatically enforced.”
So what does it mean?
You can protect the access to SharePoint data from unmanaged devices (devices which are not compliant) using Conditional Access in combination with either:
- A global setting in SharePoint either limiting the access or denying access
- A setting per SharePoint site which you can set via PowerShell to either limit of deny access
- Use a sensitivity label to control these settings.
I blogged about these concepts here: Limit Access to Outlook Web Access, SharePoint Online and OneDrive using Conditional Access App Enforced Restrictions and Defining more granularity for your Conditional Access App Enforced Restrictions using Sensitivity Labels.
What Microsoft is now adding are two things:
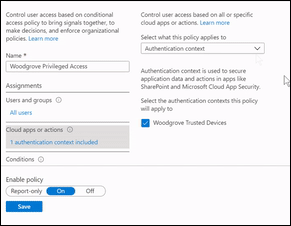
- New option in your Conditional Access Assignments section
Within the assignments section of your conditional access policy you can now select either cloud aps or user actions. For authentication context a new option will be added allowing you to secure application data and actions. Below is a screenshot from the announcement, what’s not totally clear for my yet is what the “Woodgrove Trusted Devices” option refers to, I think it’s related to the sensitivity label defined. Guess I’ll find out when this functionality is available and I can further test.
- New option in the definition of the Sensitivity label
A new option on the External sharing & device access page for the sensitivity label will be added where a new authentication context option will be added. You can specify this for the container level.
Here you can choose, between High, Medium and Low authentication context:
- High requires MFA
- Medium requires a managed device (compliant)
- Low only requires single factor authentication
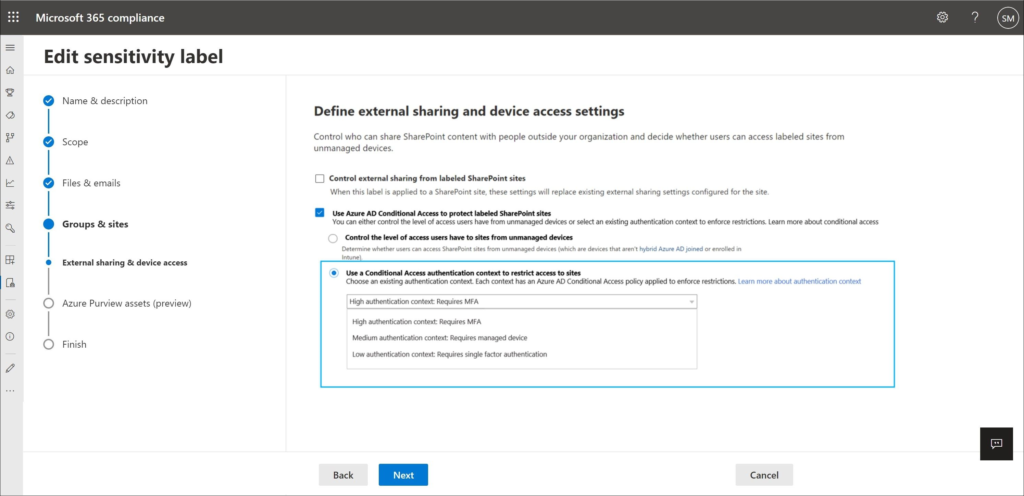
Once available to test I will dig deeper into this functionality but it looks like you can now even require MFA even on compliant devices if the authentication context on the container is set to high. It’s also interesting to see that you must either choose “control the level of access users have to sites from unmanaged devices” or “Use a Conditional Access authentication context to restrict access to sites”. I really wonder if we can keep the option to require MFA and disable the option to download or print any data in that case. More to follow.
Microsoft Endpoint Manager announcements
Besides the regular updates which Microsoft released for Microsoft Endpoint Manager, as mentioned in “What’s New” and “Features in Development“. Microsoft made some other announcements related to MEM at ignite.
Some of the announcements:
Endpoint Analytics
Microsoft has added “Application reliability” to Endpoint analytics. Endpoint analytics can help identify policies or hardware issues that may be slowing down devices and help you proactively make improvements before end-users generate a help desk ticket, even they even bother to create one.
With the addition of Application reliability you now have insights into:
- Startup performance, giving us insights into Model, Device performance, startup processes and now also Restart frequency
- Application reliability, giving us insights into App, Model, Device and OS version performance
Besides these two insights, Endpoint analytics also provides Proactive remediations (Enterprise license required) where you can create and run script packages on devices to proactively find and fix the top support issues in your organization. Endpoint analytics also has an Recommended Software option, which displays how far companies are towards a full Modern Workplace implementation (Windows 10, Azure AD joined, AutoPilot Capable and MEM managed).
My recommendation is to turn on Endpoint Analytics in your Modern Workplace environment. For this you need to configure a Configuration Policy with the Windows Health monitoring profile type.
Microsoft Defender for Endpoint risk signals available for your App protection policies
As part of a App Protection Policy (APP) for your iOS/Android based devices, you will be able to define the Max allowed threat level in the conditional launch policy which must be met in order to be able to use the app. This threat level signal will be coming from the Microsoft Defender for Endpoint app. End users will be prompted to install and set up the Microsoft Defender for Endpoint app from the appropriate store.
In your App Protection policy specify either Secured, Low, Medium, or High. Secured requires no threats on the device and is the most restrictive configurable value, while High essentially requires an active Intune-to-MTD connection. You can also define what needs to be done if the threat level is not met, either Block Access or Wipe data.
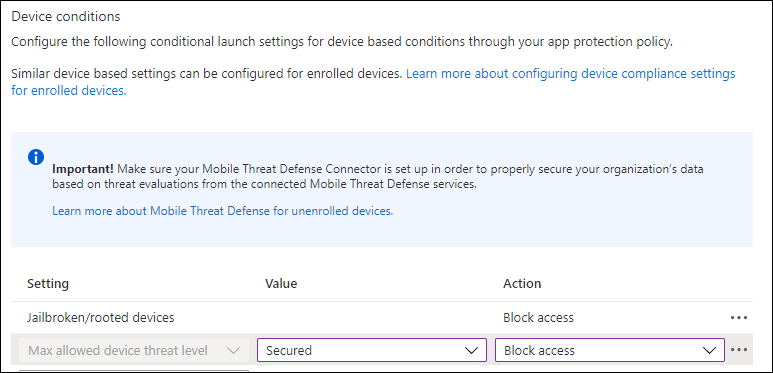
Also keep in mind that you need to setup the Mobile Threat Defense Connector in Intune if you want to support this in your MAM scenario’s.
Other announcements
Univeral Print now Generally Available
Microsoft announced that Univeral Print is now GA, in the last couple of weeks Microsoft already published many articles from vendors supporting this solution, where we don’t need print servers anymore and allow end users to print from where ever they are. If you have Enterprise, Education or Business Premium licenses you can license the functionality, see List of subscriptions that include Universal Print for more information.
Windows Update for Business deployment service
Announcing the Windows Update for Business deployment service
The deployment service is a new cloud service within the Windows Update for Business product family. It provides control over the approval, scheduling, monitoring, and safeguarding of content delivered from Windows Update, and is designed to work in harmony with your existing Windows Update for Business policies.
The deployment service significantly extends the management plane available to devices connecting to Windows Update. It will enable you to:
- Schedule update deployments to begin on a specific date (ex: deploy 20H2 to these devices on March 14, 2021)
- Stage deployments over a period of days or weeks using rich expressions (ex: deploy 20H2 to 500 devices per day, beginning on March 14, 2021)
- Bypass pre-configured Windows Update for Business policies to immediately deploy a security update across your organization when emergencies arise
- Ensure coverage of hardware and software in your organization through deployments that are tailored to your unique device population through automatic piloting
- Leverage Microsoft ML to automatically identify and pause deployments to devices which are likely to be impacted by a safeguard hold
- Manage driver and firmware updates just like feature updates and quality updates
Especially the option to managed driver and firmware updates like the other updates is a welcome addition, Microsoft published an article with more information on this specific subject: Introducing a new deployment service for driver and firmware updates“.
Intune admins, who have adopted cloud servicing and point their devices to scan Windows Update, can choose to accept drivers whenever they become available on the service or instruct Windows Update never to offer these updates. Admins set a policy in Intune that is, in turn, set on each device.
The policy choice is communicated to the Windows Update service as part of the daily scan from the device. Windows Update will only offer drivers it determines to be better than what is on a device only if the policy to allow driver updates stipulates it.
Known Issue Rollback (KIR)
Known Issue Rollback: Helping you keep Windows devices protected and productive
Known Issue Rollback allows you to quickly return an impacted device back to productive use if an issue arises during a Windows update. It only supports non-security bug fixes, as Microsoft mentions that In the context of security fixes, older code is typically more vulnerable or exploitable as the reason.
When Microsoft decides to rollback a bug fix in an update because of a known issue, they make a configuration change in the cloud. Devices connected to Windows Update or Windows Update for Business are notified of this change and it takes effect with the next reboot.
This is a very welcome addition, since we have seen some recent issues where an update caused blue screens on devices. Hopefully Microsoft can get more grips on updates using this new functionality.
Conclusion
A lot of news has been announced this week, and I’m still digesting and can’t wait to start testing with some of the announced functionality once it’s available. In this article I covered everything that I could pick up, and I’m sure that I missed some other important announcements as well. It will probably take me some weeks to get a total overview.
With the current pace of change, I do wonder though if companies are able to keep up with the speed of change. For me as a fulltime Modern Workplace consultant it’s already hard to keep up. Even though I’m really excited about all this new functionality and looking forward to some more session at Ignite later this week to hear some more in-depth context related to the announcements.
5 thoughts on “Modern Workplace Management key takeaways from the Microsoft Ignite March 2021 announcements”