Microsoft has made available service release 2111 for Microsoft Endpoint Manager, this release contains a lot of updates which are described on the What’s new page, see: Week of November 15, 2021 (Service release 2111).
Some of the updates are related to who we can gradually rollout to Windows 11, which is reflected in the following released items:
Safeguard holds are now visible in the Feature update failures report
Improvements for managing Windows Updates for pre-release builds
Use Update Rings for Windows 10 and later to upgrade to Windows 11
New scheduling options for Feature updates for Windows 10 and later
When Windows 11 was released, I already posted a short blog article about whether devices would be automatically updated when using the Update ring functionality. In that same article I also referenced to the following article giving a glimpse of what was coming: Endpoint Manager simplifies upgrades to Windows 11 – Microsoft Tech Community
So let’s go through the released items and see the new options we have available to streamline the rollout of Windows 11 within our Modern Workplace environment.
Safeguard holds
Safeguard holds, are basically reasons why a device is not able to upgrade to either a new feature update, or to a new OS release like Windows 11. Safeguard holds can be defined for multiple scenario’s, for example if some software is running on the device which has a known issue, drivers have a known issue. While safeguard holds help you to make sure that incompatible devices are not upgraded, there are some actionable items. To lift the Safeguard hold you could remove or update incompatible software or driver, after which the safeguard hold will be lifted and the device will upgrade. The is an option to lift a safeguard hold on a per device basis, more information here: Opt out of safeguard holds
The Safeguard holds which are currently applicable can be found on the Windows release health documentation page, which is available via the following link: https://aka.ms/WindowsReleaseHealth
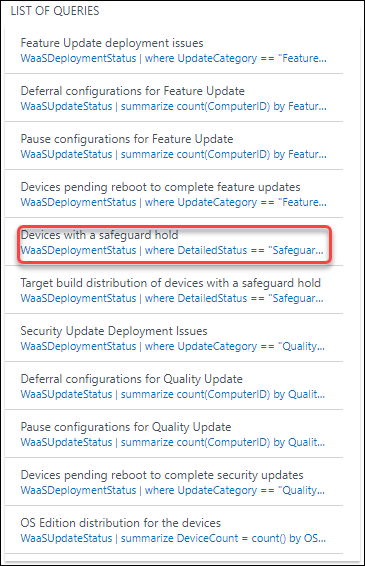
Viewing Safeguard holds with Update Analytics
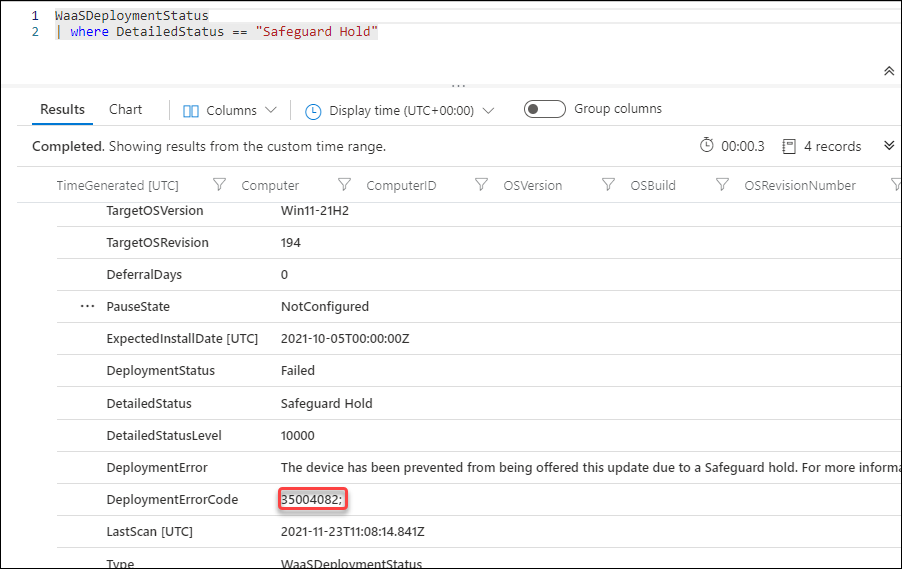
If you have Update Analytics Configured, there was already a predefined query to check for devices with safeguard holds. There is also a Workbook available called Update Compliance – Safeguard holds
The query provides a list of devices holding a Safeguard Hold, in the result of the query you can find the DeploymentErrorCode which you can use to look up the issue on the Known issues and notifications page, and in this case the error translates to: Compatibility issues have been found between Oracle VirtualBox and Windows 11
Viewing safeguards in the Feature update failure report
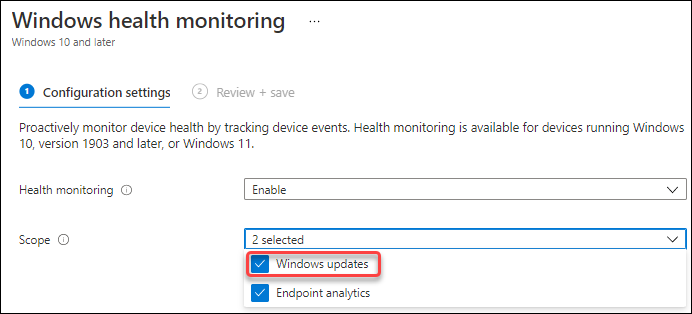
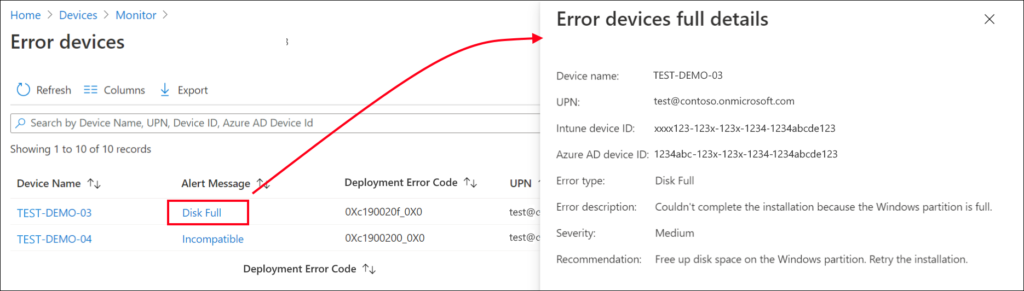
If you don’t have update analytics configured, you can also use the Feature update failures report, which is available under the Software Update section under the Monitor option in Microsoft Endpoint Manager. Before you can use the report, the Windows updates scope within Windows Health Monitoring must be configured though.
The following screenshot is borrowed from the Microsoft documentation page, and as you can see in this specific example the upgrade couldn’t continue because there was not enough disk space available on the device.
Besides these 2 methods, there are other reports available as well, might be a topic for a future blogpost.
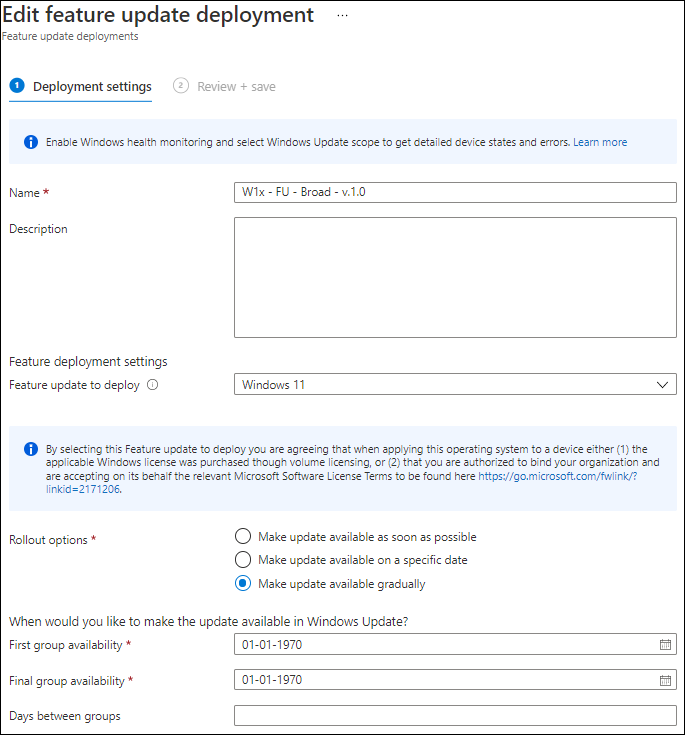
Changes to Feature update deployments
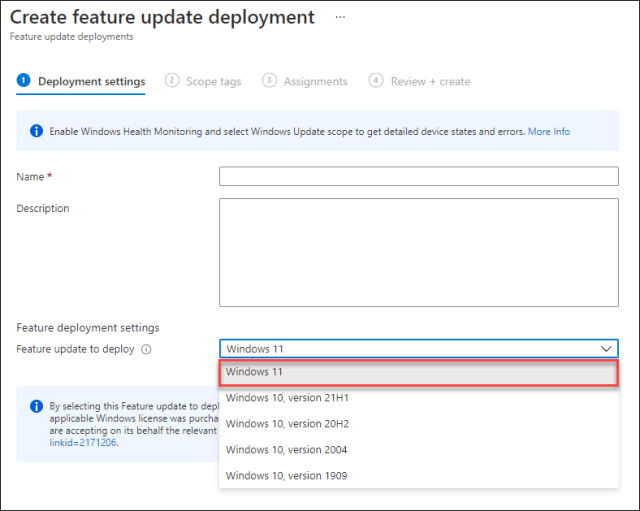
Before the recent changes we only had the option to specify the feature update to deploy, as shown in the screenshot below, devices or users targeted by the feature update deployment received the update to Windows 11 if their device was able to upgrade. (no safeguard holds)
After the recent changes we now have a lot more options available to configure, as shown in the screenshot below
By default the option “Make update available as soon as possible” is selected, which provides the same experience as the old configuration option. We now also have the following options:
- Make update available on a specific date
- Make update available gradually
The make update available on a specific date option allows you to specify a day when the update becomes available to install, making sure that Windows update doesn’t make the update available before that date.
The make update available gradually option allows you to define a time range, after which Windows update will create a subset of the devices which are targeted in the policy. These subsets are called “Offer groups”, and Windows update assigns devices to these “offer groups” randomly, keeping the groups evenly-sized. The rollout will be load balanced in order to reduce the network traffic.
You can specify when the First Group must be offered the update by specify the First group availability date, this date must at least be 2 days in the future from the moment that you configure the value. By doing so, Windows update identifies the devices, define the offer groups and assign the devices to those offer groups.
By specifying the Final group, you specify the date that all remaining devices which didn’t receive the offer yet are offered the update.
By specifying the Days between groups, Windows Update can calculate the amount of offer groups to create, since it knows the amount of devices, when to start and when to end.
For more information about the different options available please read the following article: Rollout options for Windows Updates in Microsoft Intune
Changes to the Update Rings
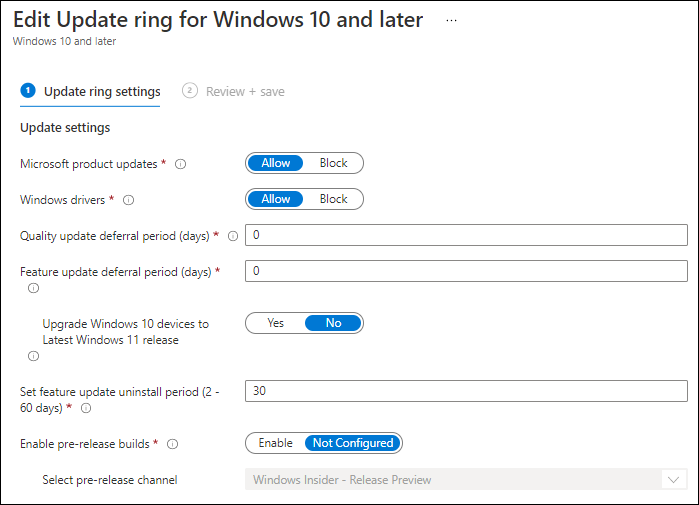
The options available within the Update rings have also changed, the first option added is “Upgrade Windows 10 devices to Latest Windows 11 release”. The setting is set to “No” by default, but when set to Yes devices in the applicable deployment ring will update to the latest release of Windows 11. You could for example use this option, after you did a pilot using the feature updates functionality, enabling the “Upgrade Windows 10 devices to Latest Windows 11 release” option per deployment ring to rollout the remaining devices within your organization.
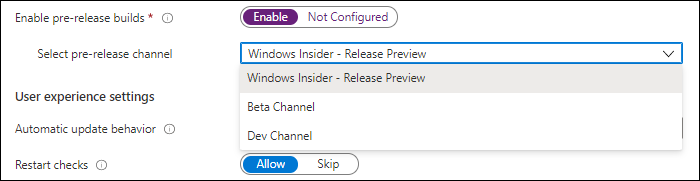
What also changed is that the “Servicing channel” option is now removed, and replaced by the option “Enable pre-release builds”. If you enable this option you can choose between the following pre-release build options:
- Windows Insider – Release Preview
- Beta Channel
- Dev Channel
By making this optional within the Update ring itself, by default the correct servicing channel is now configured, which makes more sense.
Another welcome change here is that devices assigned Update rings for Windows 10 and later policies will no longer have the ManagePreviewBuilds setting changed during Autopilot. When this setting changed during Autopilot it forced an additional device reboot.
Conclusion
Some welcome additions related to deploying Windows updates to your modern workplace devices if you ask me. Make sure that you properly prepare before you start the rollout of Windows 11. Start with understanding which devices are eligible for an upgrade, by using the Work from Anywhere report as part of Endpoint Analytics. Then start with a small pilot using the Feature Updates functionality. Once you feel that you are in control, you might leverage the options in the deployment rings to use your normal rollout mechanism to deliver the Windows 11 update.
Want to know more about how to configure your Windows Update for Business (WUfB) settings, then I invite you to read the following article as well
References
Safeguard holds – https://docs.microsoft.com/en-us/windows/deployment/update/safeguard-holds
Rollout options for Windows Updates in Microsoft Intune – https://docs.microsoft.com/en-us/mem/intune/protect/windows-update-rollout-options
Feature Update Status – https://docs.microsoft.com/en-us/windows/deployment/update/update-compliance-feature-update-status
Access safeguard hold details with Update Compliance – https://techcommunity.microsoft.com/t5/windows-it-pro-blog/access-safeguard-hold-details-with-update-compliance/ba-p/1809652
Use the Feature update failures (Operational) report – https://docs.microsoft.com/en-us/mem/intune/protect/windows-update-compliance-reports#use-the-feature-update-failures-operational-report